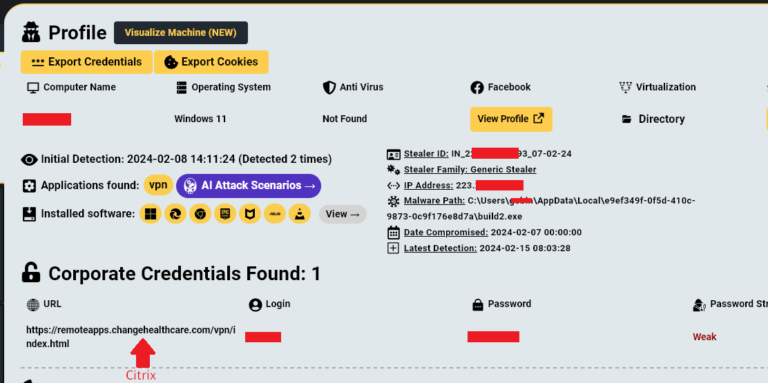
Single Citrix Compromised Credential Results in $22,000,000 Ransom to Change Healthcare
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000