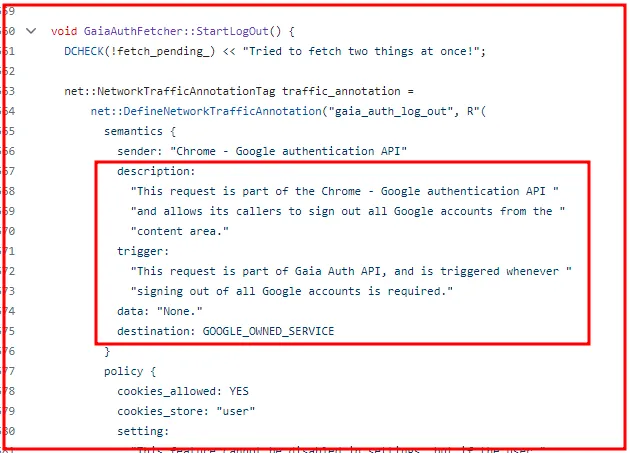
Breaking through the Infostealer Exploit and the Enigma of Cookie Restoration.
The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Home » 0-Day

The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
