
Hudson Rock Announces First Comprehensive Infostealers AI Bot: CavalierGPT
Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data
Home » Hudson Rock

Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data

In this new episode of the mnemonic security podcast, Robby Peralta is joined by Leonid Rozenberg, a cybersecurity expert and dark web researcher at Hudson
Disclaimer: Hudson Rock does not insinuate or imply responsibility or liability on behalf of any parties mentioned herein. The content is intended solely for informational

Interview with Malware Protection expert Leonid Rozenberg with Hudson Rock (www.hudsonrock.com) on exposing information stealers, protecting identities online, hackers who sell vulnerabilities, and how to

Learn about Infostealers with actual real life breaches caused by Infostealer infections with Leonid Rozenberg, Hudson Rock’s Head of Partnerships & Integrations. To discover how
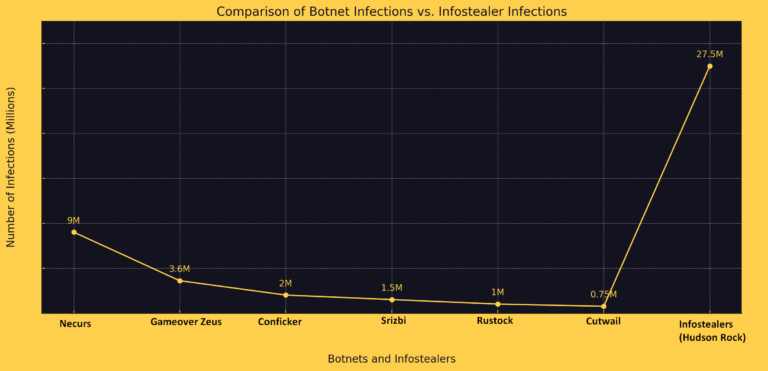
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
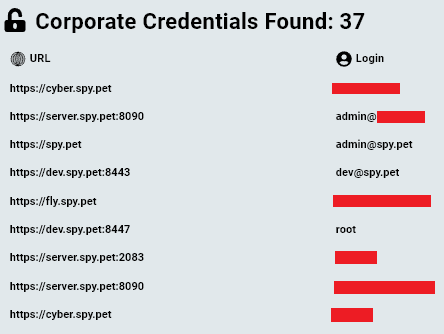
This article aims to shed light on the identity behind a massive Discord spying tool and raise concerns about the possibility of private Discord data
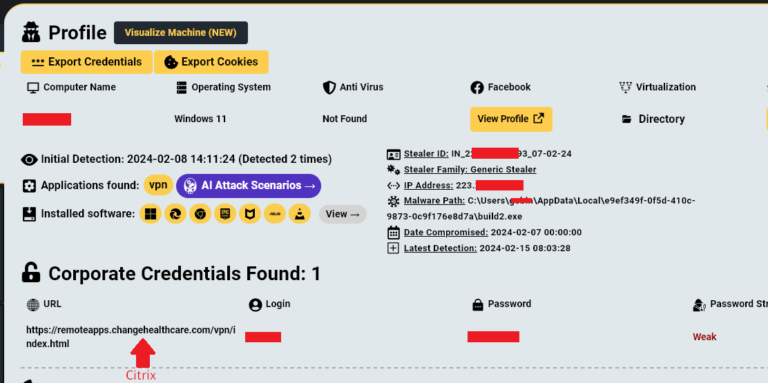
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000

In this Help Net Security interview, Alon Gal, CTO at Hudson Rock, discusses integrating cybercrime intelligence into existing security infrastructures. Our discussion will cover a range
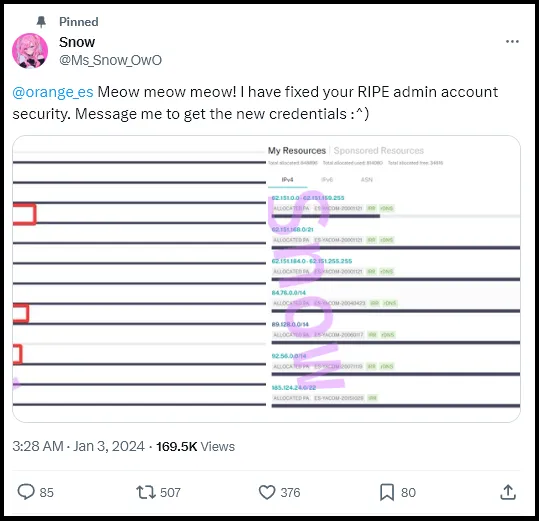
Using the stolen account, the threat actor modified the AS number belonging to Orange’s IP address, resulting in major disruptions…
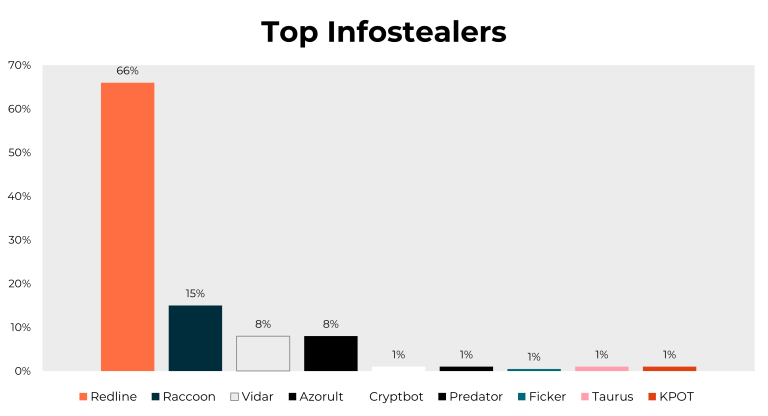
Infostealers are a type of malware designed to steal information from the victim system in order to send it to the attacker…

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach
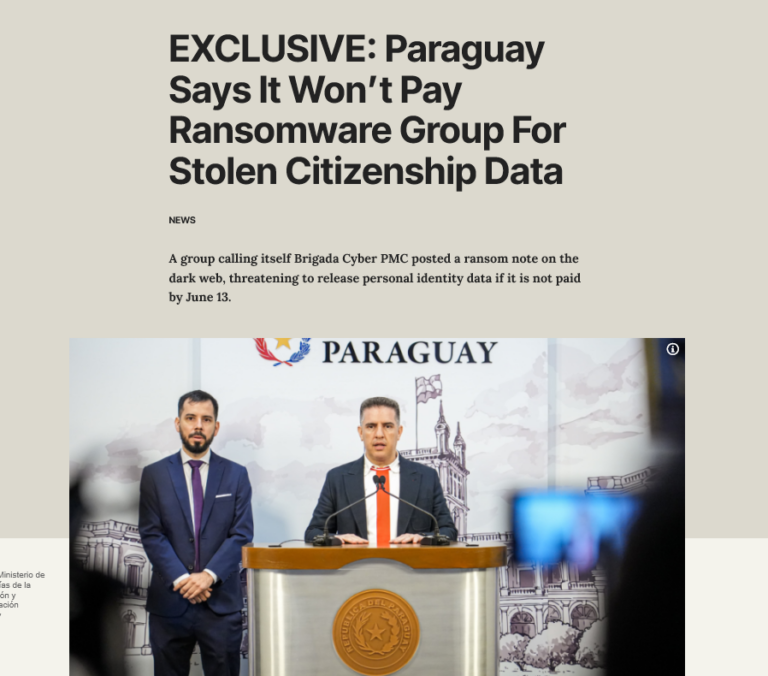
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
