A threat actor attempts to sell access to a sensitive area of Binance — the major cryptocurrency exchange’s law enforcement portal. This kind of access poses specific risks to cryptocurrency holders and users.
Although threat actors often lie about accesses they possess, in this example it appears the threat actor maintains positive reputation from previous sales conducted on the forum, and they also offer a range of other unrelated accesses.
The asking price for the access is $10,000 in Bitcoins or Monero.
In order to identify how the threat actor obtained access to the panel, Hudson Rock researchers first located the location of Binance’s law enforcement panel which is hosted on kodexglobal.com

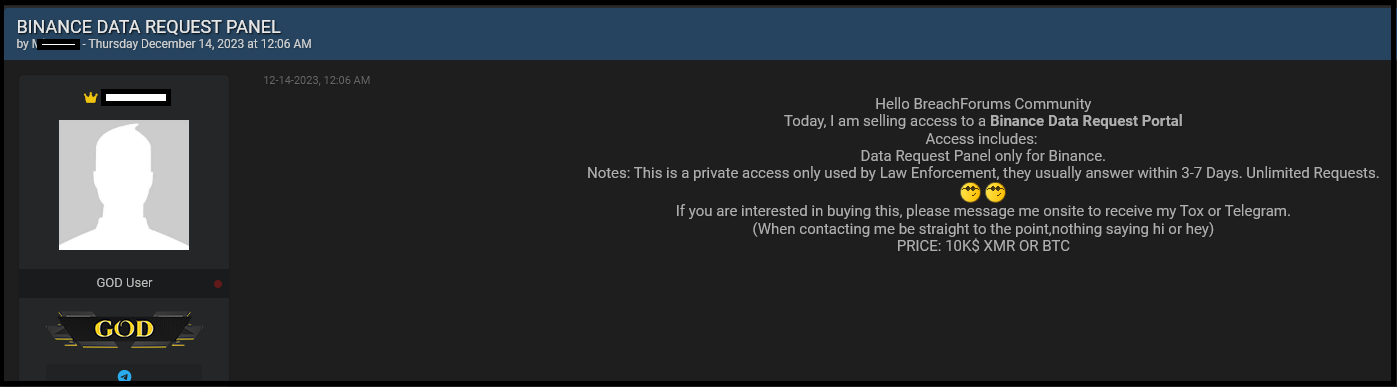
Hudson Rock was then able to identify several computers that were recently infected by Infostealers with specific compromised credentials to https://app.kodexglobal.com/binance/signin:

The image, taken from Hudson Rock’s cybercrime intelligence database, shows three computers that were opportunistically infected by global malware spreading campaigns in 2023, which resulted in credentials that were stored on the victims’ browsers falling to the hands of hackers.
The three logins shown in the image with access to Binance’s login panel appear to belong to compromised law enforcement officers in the Criminal Investigation Bureau (CIB) in Taiwan, the Uganda Police Force (UPF), and the Anti-Cybercrime Group (ACG) of the Philippine National Police (PNP).
While it is uncertain whether the access was obtained through these logins, it is highly probably that credentials from Infostealer infections were used to infiltrate the law enforcement portal, as seen in a recent example we shared of a Hacker Who Used Infostealer Data to Gain Access to Brazil’s Police Portal.
It is worth noting that the threat actors confirms the functionality of the service using the compromised account:

Hudson Rock reached out to Binance in order to share the identified details.
The dangers linked to this breach expand beyond conventional cyber threats and data privacy concerns. For cryptocurrency holders, the potential implications are severe:
- Wallet Addresses and Transaction Records: Leakage of wallet addresses or transaction histories could compromise the anonymity of cryptocurrency transactions. This could lead to targeted attacks or scams against individuals based on their transaction patterns or financial history.
- Identity Theft & Extortion: Personal data exposed through this breach might facilitate identity theft, leading to extortion attempts against cryptocurrency owners, leveraging their sensitive information for malicious purposes.
- Financial Loss: Access to a platform like Binance’s law enforcement portal could allow unauthorized individuals to manipulate or compromise accounts, resulting in significant financial losses for cryptocurrency holders.
As of now, we recommend cryptocurrency holders prioritize:
- Regularly updating passwords and utilizing strong, unique credentials.
- Enabling enhanced security features like two-factor authentication across all platforms.
- Remaining vigilant for any signs of suspicious activity within their accounts and platforms.
This incident emphasizes the importance of a comprehensive approach to cybersecurity, especially in the context of cryptocurrency holdings, where the stakes are notably high.
For more insights into cybersecurity solutions tailored to protect against such threats and to explore Hudson Rock’s tools and expertise, visit: Hudson Rock’s Free Cybercrime Intelligence Tools.
Stay informed and fortified against cyber threats — your digital assets depend on it.
Connect with Hudson Rock:
- LinkedIn: Hudson Rock LinkedIn
- Twitter: Rock Hudson Rock Twitter