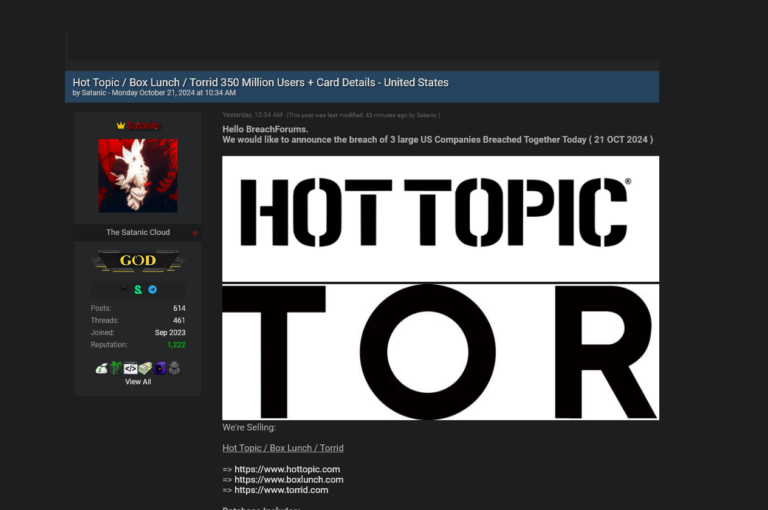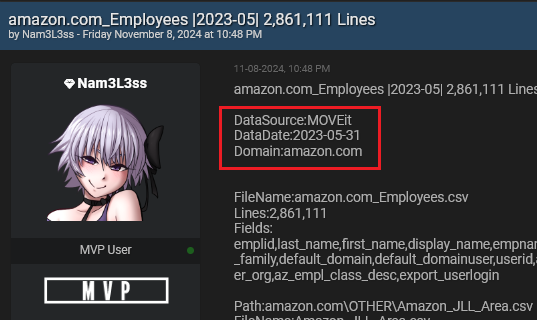
Massive MOVEit Vulnerability Breach: Hacker Leaks Employee Data from Amazon, McDonald’s, HSBC, HP, and Potentially 1000+ Other Companies
Written by Alon Gal A person operating under the username Nam3L3ss has exploited a critical vulnerability in MOVEit, a file transfer software, exposing extensive employee