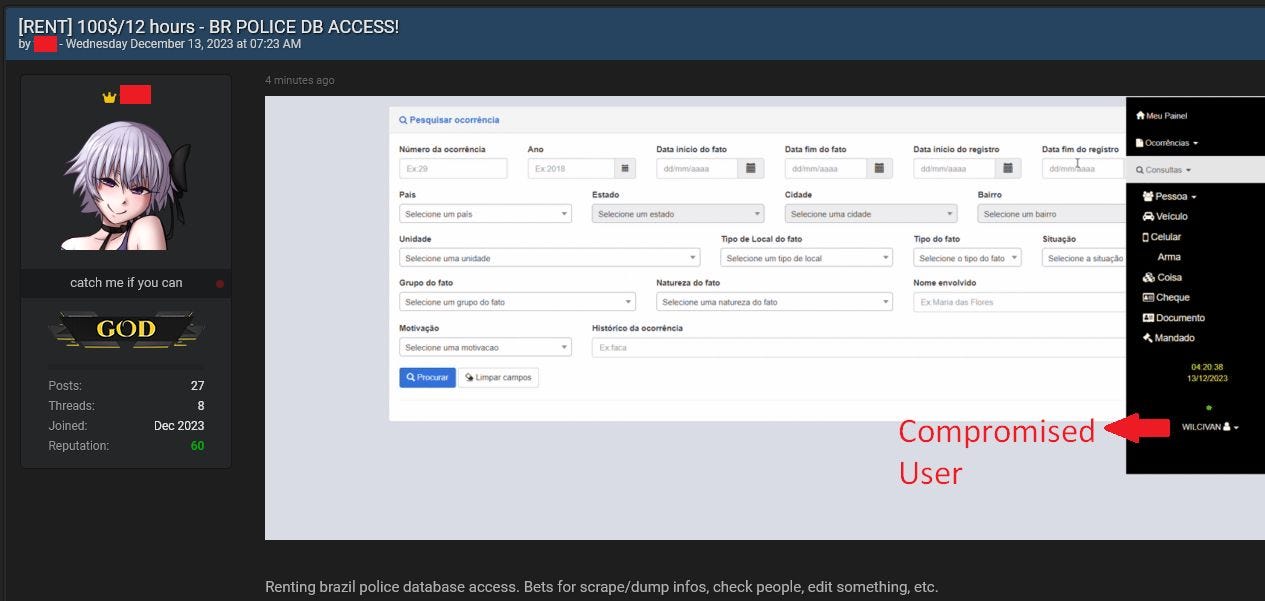
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks, including ransomware, data breaches, account takeovers, and corporate espionage. Hudson Rock recently identified a thread posted on a prominent cybercrime forum in which a threat actor attempted to rent access to the Brazilian police database.
The risks associated with having such access are significant, including:
- Privacy violations
- Identity theft
- Extortion
- Data alteration
- Data leakage
Fortunately, researchers at Hudson Rock noticed that the hacker inadvertently left a crucial piece of identifying information regarding the compromised access. In the image above, we can see that the portal was signed into by a user with the username “Wilcivan.” Using this information, Hudson Rock was able to determine that the access originated from a recent Infostealer infection on a Brazilian computer. This was confirmed by comparing the victim’s username to Hudson Rock’s cybercrime intelligence database.
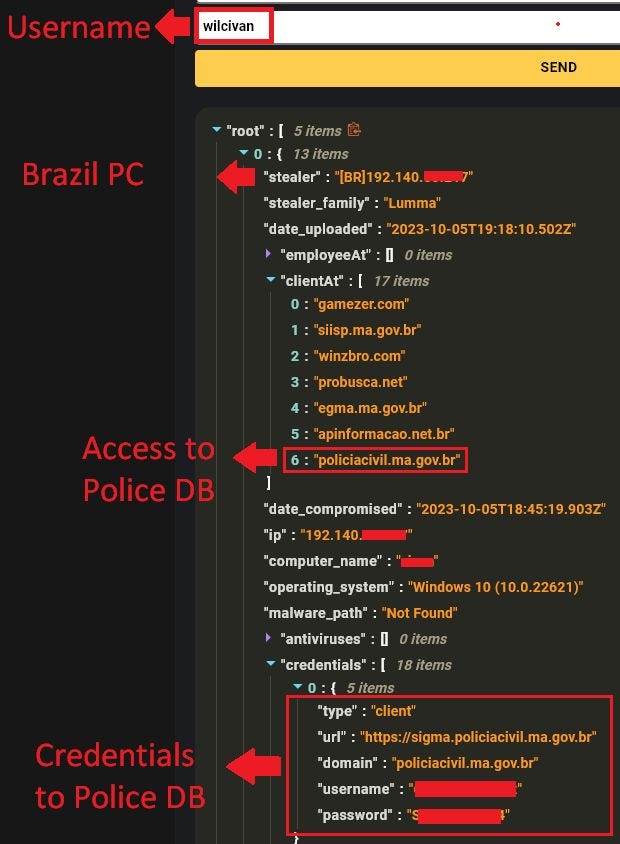
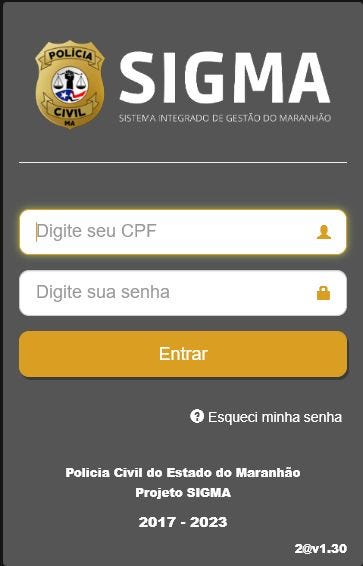
The infected computer contained credentials for a URL belonging to the Brazilian police: https://sigma.policiacivil.ma.gov.br. Associated with this URL were the username and password of the victim whose account had been breached.
This incident highlights a significant risk posed by Infostealers. Once an individual is compromised, hackers will leverage all their resources and creativity to exploit the stolen information for various types of breaches. Fortunately, in this instance, access was revoked, and Hudson Rock was able to alert Brazilian authorities to take action.
In a landscape where data breaches and cyber threats are so common, vigilance and proactive measures are required. Users must adopt a multi-layered approach to safeguard their digital identities. This includes regular password updates, enabling two-factor authentication whenever possible, and monitoring for any suspicious activity within password managers.
Furthermore, it is important to routinely check your organizational exposure to Infostealer infections which are the top initial attack vector for threat actors to access corporate and customer accounts.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock