
Key Learnings from Files Present on the C2 Server of an Infamous Infostealer Malware
This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
Home » VirusTotal

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
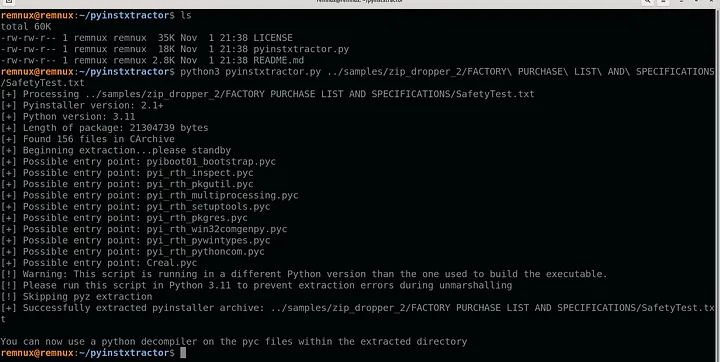
A ZIP/LNK payload and, with some luck, we will end up identifying the infostealer that is being dropped and its source code…
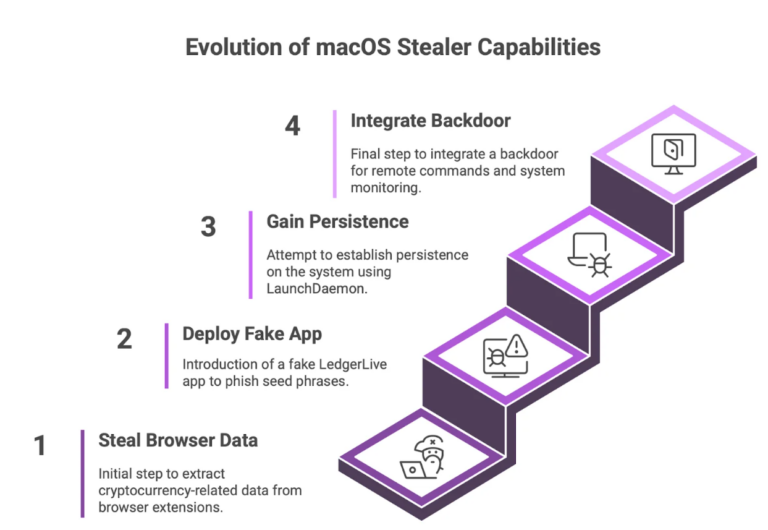
Atomic macOS Stealer (AMOS), a popular piece of stealer malware for macOS, has just received a major update. For the first time, it’s being deployed

At SINCON 2025 in Singapore, Leonid Rozenberg sat down with cyber journalist Jane Lo for a brief but powerful 15-minute interview that catches you up

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
