
Botnets & Info-Stealers (Part Ⅲ)
In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…
Home » Cyrus

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach
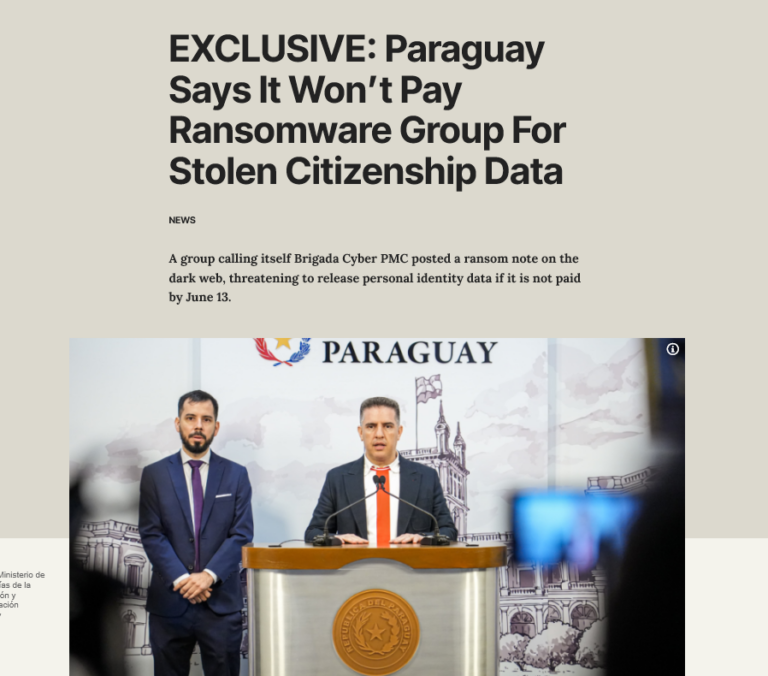
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
