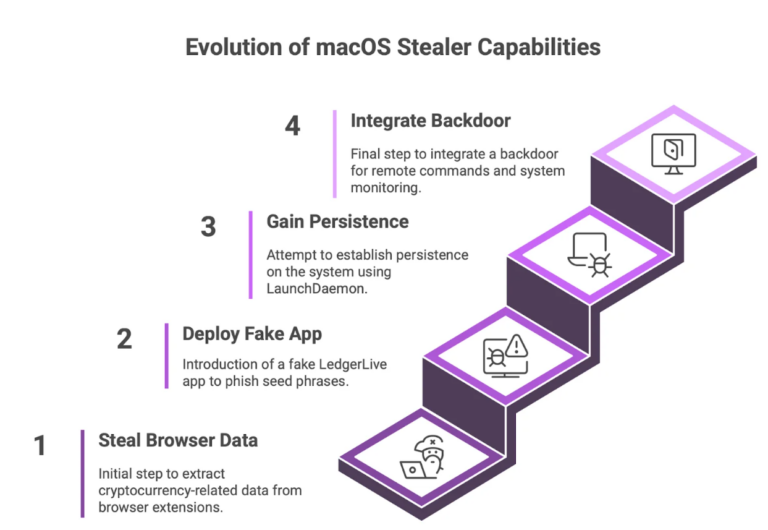
What are infostealers?
Infostealers are a type of malware designed to steal information from the victim system in order to send it to the attacker.
The first infostealer was discovered in 2006 and was known as ZeuS or Zbot. It was known to target credentials of online banking services. The code of ZeuS was leaked and then many variants of it were created.
Infostealer malware is designed to steal data after a single run, and it usually removes itself from the system. These typically operate as malware as a service (MaaS), a business model in which the developers of malicious software lease their malware to others for a fee. This arrangement allows almost anyone to deploy an infostealer regardless of their technical know-how.
What information is collected by infostealers?
Typical information stolen by this type of malware include:
- Computer information such as hostname, username, IP address and OS details.
- Data from browsers such as credentials, credit card numbers, cookies and autofill forms.
- Other types of information such as cryptocurrency wallets, VPN clients’ data, other applications’ credentials (i.e., Steam, Discord, etc.) and any plain-text passwords stored on the system.
Why are they so dangerous?
Infostealer malware is known to steal not only saved credentials but also session tokens, which can help threat actors to bypass multifactor authentication (MFA). As a result, infostealers can provide threat actors with immediate account access without requiring the use of more sophisticated tools or staying active in an environment for long time.
Confidential data stolen by infostealers is later offered through the darknet or other cybercriminal forums. Once bought, this information can fuel further malicious activities. The nature of activities performed by threat actors varies according to the value of the stolen information.
While compromised credit cards or bank accounts might have individual consequences such as fraudulent transactions, etc., it’s not uncommon for users to save credentials to corporate browsers. From an attacker’s perspective, this type of data is low-hanging fruit that can allow quick access to corporate networks — which could lead to serious consequences such as ransomware infection.
How does a system get infected with an infostealer?
The most common methods used by infostealers are:
- Phishing email: Threat actors commonly deliver infostealers via email. This can be through an attachment or tricking users into clicking on a URL within the email.
- Search engine ads: Currently, the most frequent and effective distribution method of infostealer malware is through search engine ads. Threat actors masquerade phishing sites to mimic legitimate websites. Using Google or Bing ad features, attackers position such malicious sites to appear first in the search-engine results for a particular software.
- Cracked/pirated software: Often, users are seen trying to download cracked software and compromising their system with infostealers.
- Infected pen drives: Systems get infected with infostealer or other malware that copies itself to external drives such USB or pen drives. Then, when the drive connects to another system, that system gets infected as well. The technique is usually seen in .LNK malware that tricks users into clicking a file that looks like shortcut to the pen drive itself. However, clicking on the file initiates a connection to a command-and-control server from which the payload is downloaded.
- YouTube videos: YouTube users are offered free game cheats within the videos. Clicking the link in the description box instead downloads an infostealer.
Case study
A recent breach investigated by Atos Computer Security Incident Response Team about ransomware infection in one of the customer environment revealed the following course of action.
A user, working from a corporate device, used their personal Google Account’s password synchronization feature to save their corporate VPN credentials in the browser. The same Google account was used on his private device as well, which meant the VPN credentials were synced to this device.
The user downloaded cracked software to their personal device. The infostealer malware infected the personal device, and threat actors were able to obtain the VPN credentials along with other stored credentials. This account was then used by threat actors to access the corporate environment. After data exfiltration, ransomware was deployed across other devices in the corporate environment. This also highlighted the requirement of MFA which was found to be missing in this case.
Infostealer trends
The below chart shows top user accounts compromised by infostealers. Note: Most targeted user accounts are Microsoft or Google accounts, which are also in many cases used by corporations. It also shows other social accounts.
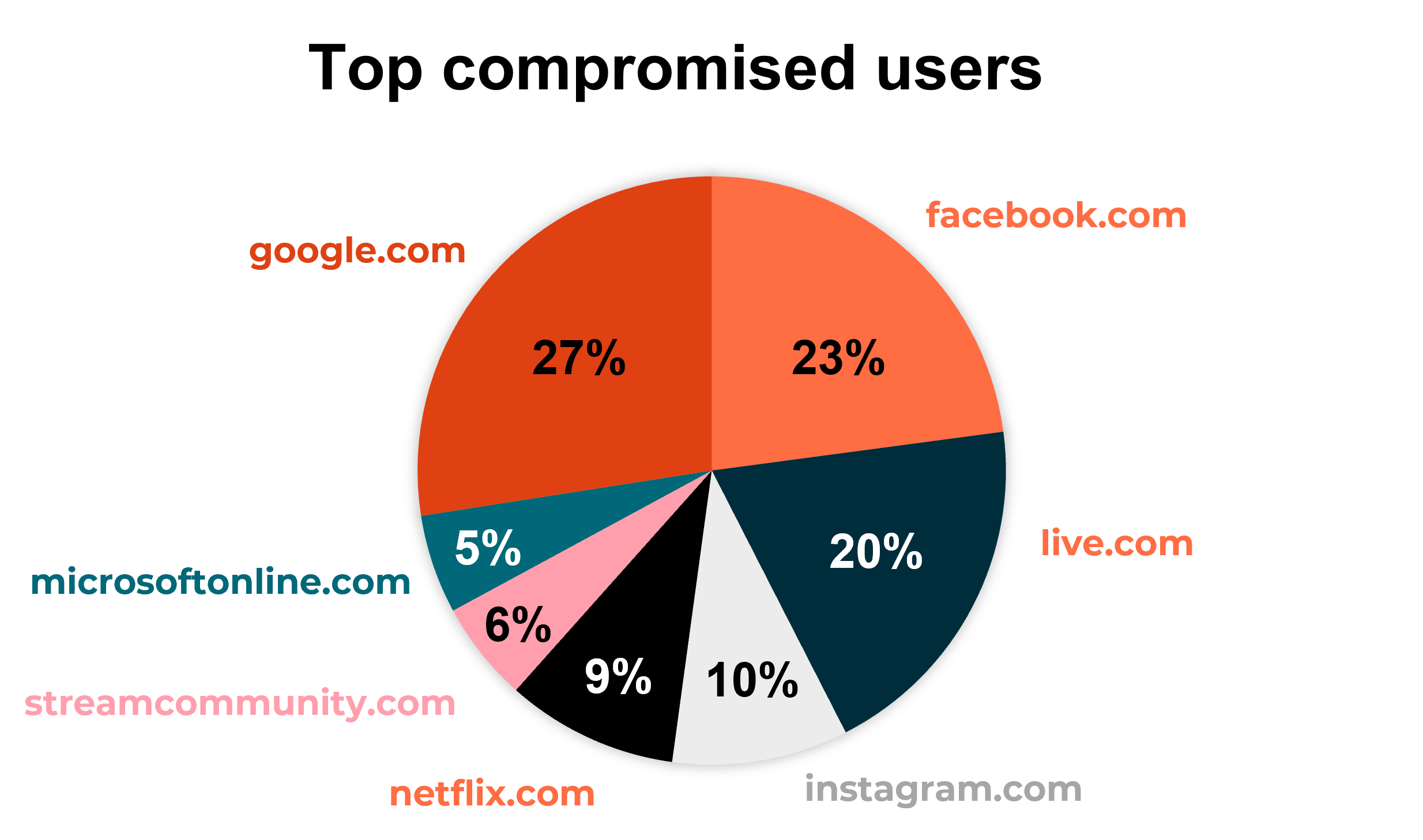
Source – Hudson Rock
The graph below shows top infostealers seen in worldwide attacks. Note: Redline, Raccoon and Vidar contribute the most compromises worldwide.

Source – Hudson Rock
Below are the top mobile applications compromised by infostealers.
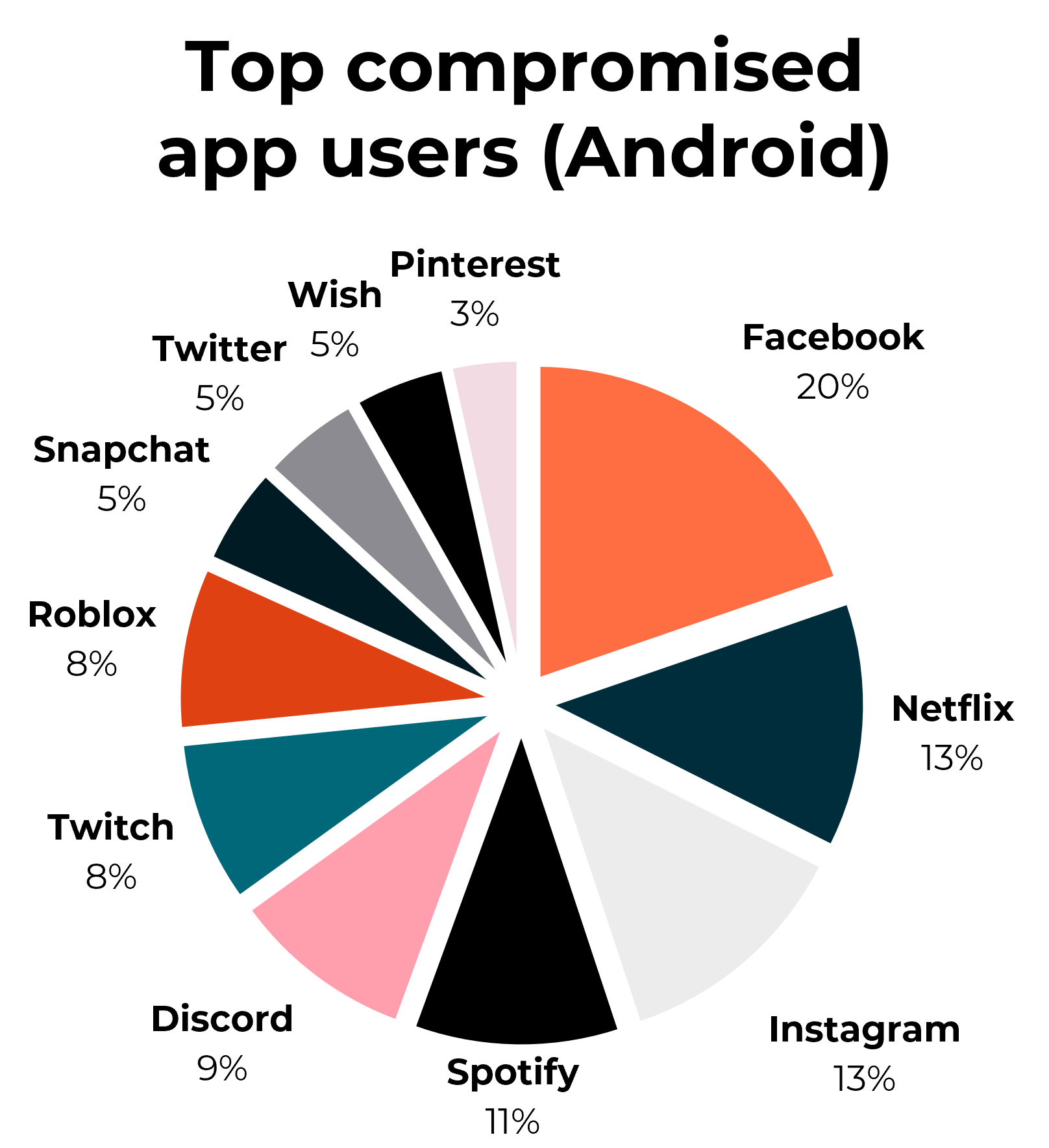
Source – Hudson Rock
See below the number of users compromised by infostealer malware. This chart shows a significant increase in 2022.
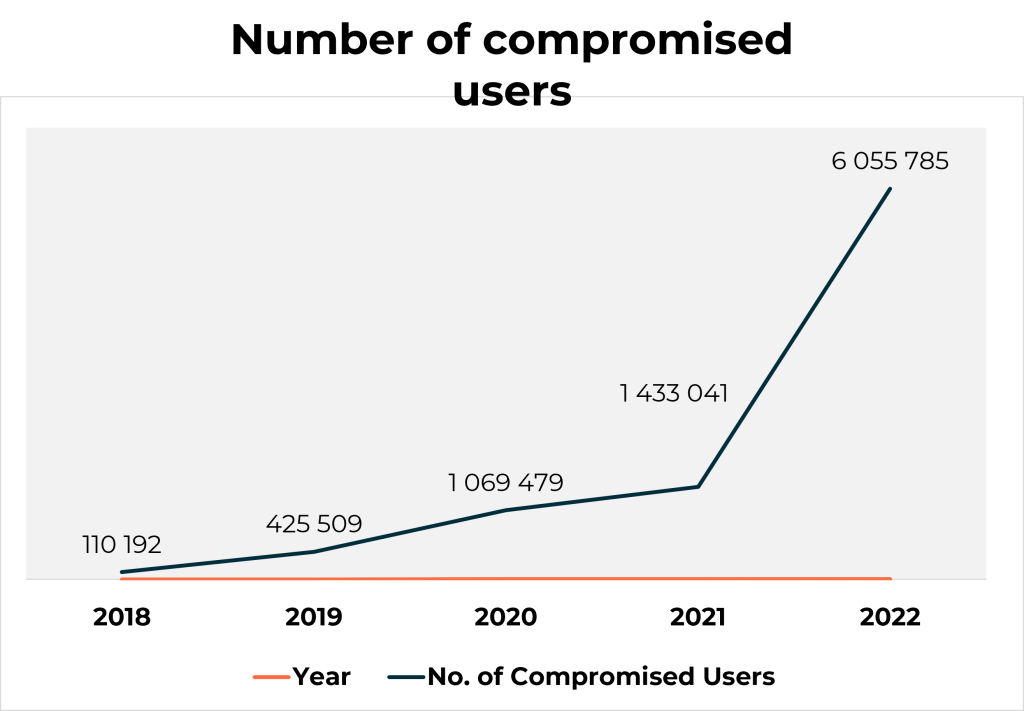
Source – Hudson Rock
How to protect your organization from infostealers
The following practices will help reduce the risk of infostealer infection.
- Conduct regular user security awareness training: In most attacks, users are the weakest link no matter how sophisticated your security tools are. So user training is very important, specifically on spotting fake/spoofed email. Users should stay vigilant when opening any email from unknown senders and report any suspicious emails to your security operations center for analysis.
- Scan/limit email attachments: Scan email attachments at the gateway level to check for malicious content. Block known malicious file extensions at the gateway level.
- Use MFA for all applications: MFA acts as an additional layer to protect users even if the user account gets compromised.
- Use password manager for storing and generating complex passwords, and do not store passwords in browsers.
- Deploy an endpoint detection and response (EDR) solution on all endpoints: This way, even if a user opens a malicious attachment or clicks on a malicious URL, EDR will be able to detect, alert and block the threat.
- Block search-engine ads: Block search-engine ads at the proxy or web gateway level, or use ad-blockers to prevent malicious ads.
- Limit admin rights: Do not give admin rights to users. Whenever there is need of such rights, temporary permission can be assigned dynamically.
- Block unwanted applications through Microsoft Intune: Intune policies such as Windows Defender Application Control management prevent users from installing pirated/cracked software.
- Do not synchronize credentials between corporate and private devices: For example, don’t use private Google account sync features.
- As Defense strategy monitor what is available on the Dark Web within DRPS (Digital Risk Protection Services) which includes continuous monitoring of compromised credentials with technology like Hudson Rock Cavalier.
Hudson Rock is an Israel company, which is utilizing cybercrime intelligence and forensic technologies that helps prevent ransomware attacks and data breaches caused by infostealer infections. Hudson Rocks provides continuously updated databases- sourced from threat actors and millions of compromised machines to support Threat Intelligence Professionals and Cybersecurity Experts.