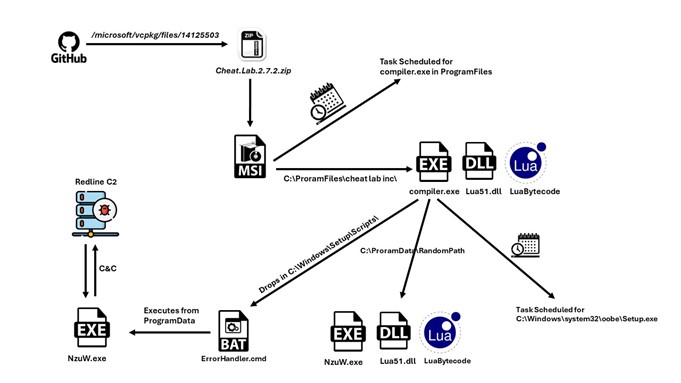
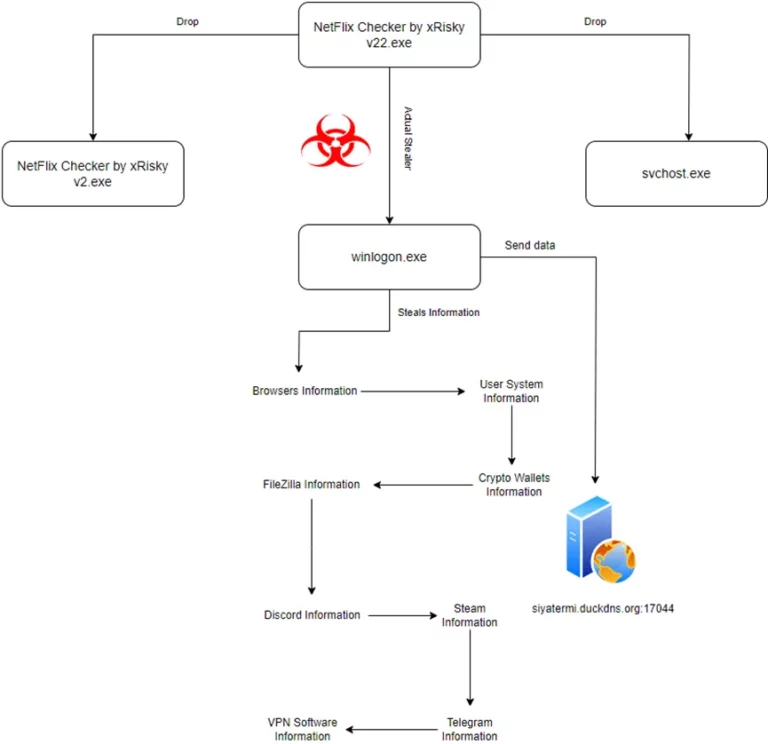
Law Enforcement Hacked Infrastructure of Redline and Meta Infostealers (Operation Magnus)
*Not fully confirmed yet According to the website which was discovered through Redline related Telegram channels, law enforcement was able to hack the infrastructure of