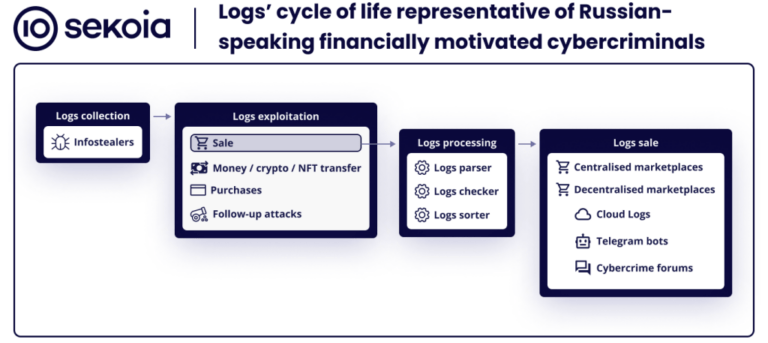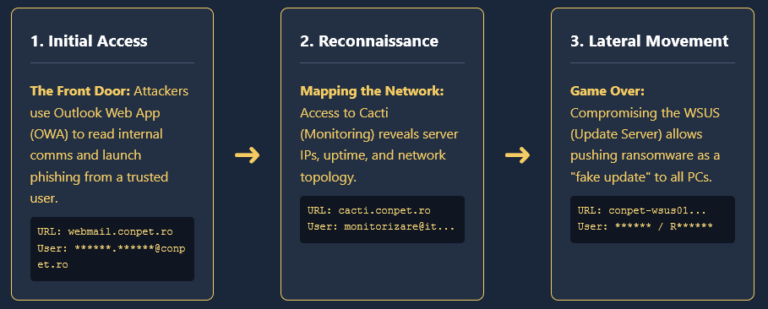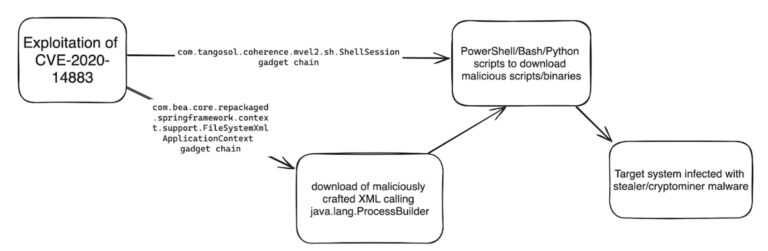
8220 gang exploits old Oracle WebLogic vulnerability to deliver infostealers, cryptominers.
The 8220 gang has been leveraging an old Oracle WebLogic Server vulnerability (CVE-2020-14883) to distribute malware, the Imperva Threat Research team has found…