In today’s digital landscape, the reliance on password managers has become commonplace, providing users with a sense of security and ease of access to their online accounts. However, recent events have shed light on a crucial vulnerability within these seemingly robust systems: the susceptibility to infiltration by threat actors.
In this scenario, a threat actor gained access to compromised credentials of Bitwarden accounts, a popular password manager utilized by millions. This breach exposes a glaring reality — just one compromised credential could potentially open the floodgates to a complete takeover of one’s identity and finances.

The severity of such an incident cannot be overstated. Once hackers obtain a user’s credentials, they gain access to a treasure trove of personal data.
This includes not only login information but also sensitive details such as credit card information, financial documents, secure notes, cryptocurrency keys, and more.
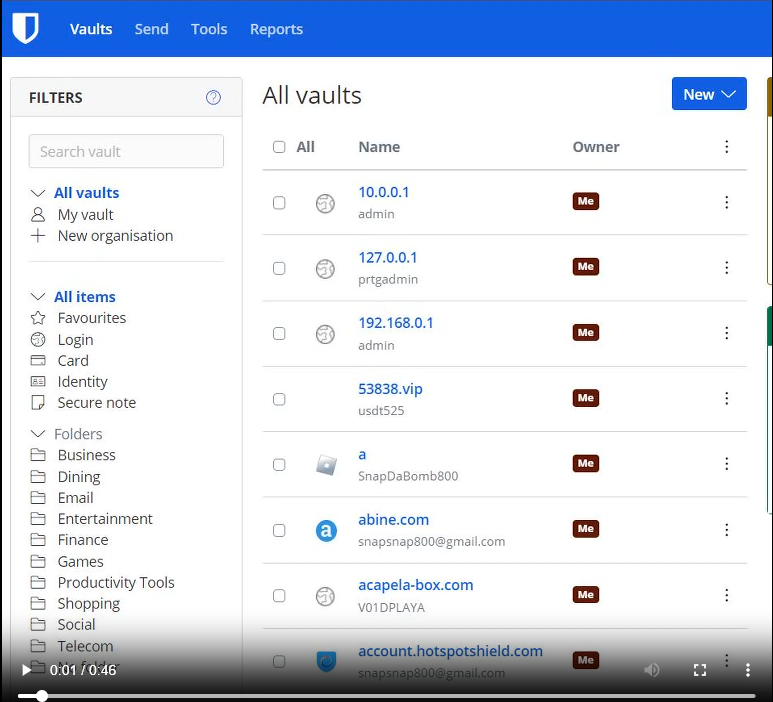
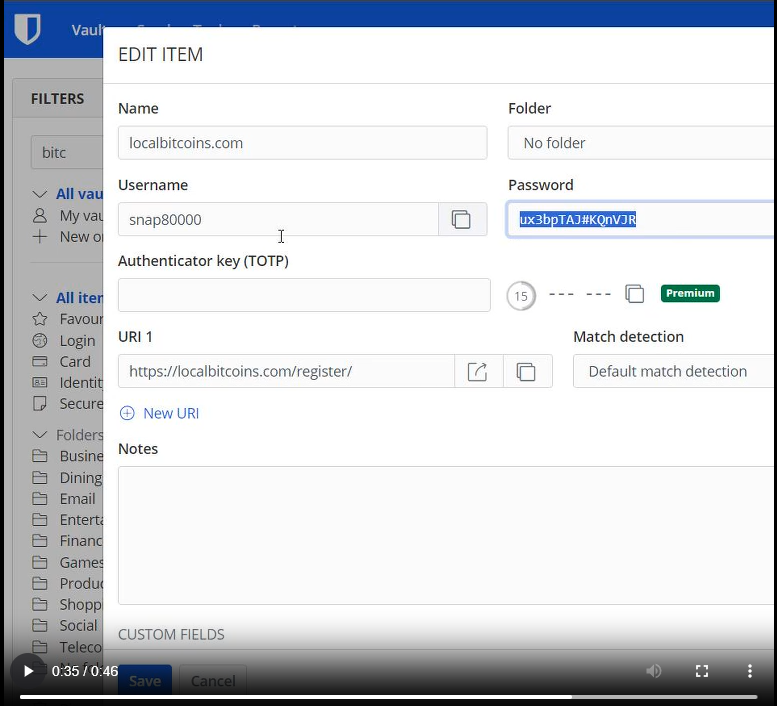
How do hackers typically gain access to these password managers? There are several avenues:
- Infostealer Infections: Hackers exploit vulnerabilities in systems to steal login information directly from infected devices.
- Breached Databases: Compromised databases where user credentials are stored become a goldmine for threat actors seeking unauthorized access.
- Bruteforce Attacks: Using automated tools, hackers attempt various combinations until they crack the passwords.
In the instance shared above, a threat actor was observed selling 130 working credentials. However, startling revelations from Hudson Rock’s cybercrime intelligence database indicate that this threat is far bigger, with over 10,000 Bitwarden credentials harvested from Infostealer infections alone.

Worth noting is that the provided login samples provided by the threat actor align with data found in Hudson Rock’s database, tracing back to Infostealer infections — a classic modus operandi for cybercriminals.

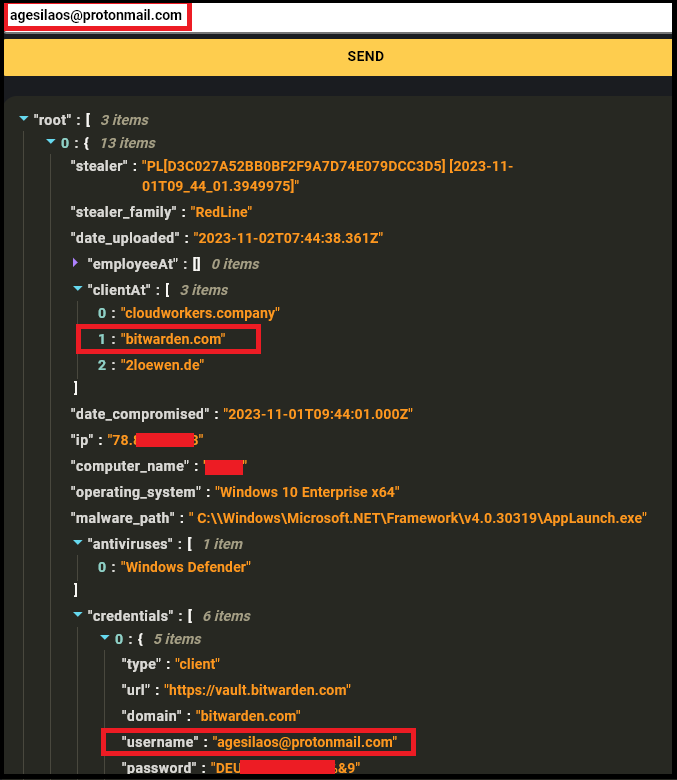
The implications of such breaches are clear: blindly trusting password managers can lead to catastrophic consequences. While these tools offer convenience and security, they are not impervious to exploitation by sophisticated threat actors.
In a landscape where data breaches and cyber threats are so common, vigilance and proactive measures are required. Users must adopt a multi-layered approach to safeguard their digital identities. This includes regular password updates, enabling two-factor authentication whenever possible, and monitoring for any suspicious activity within password managers.
Furthermore, it is important to routinely check your organizational exposure to Infostealer infections which are the top initial attack vector for threat actors to access corporate and customer accounts.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock