Introduction
Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare.
This attack not only led to business disruption but also resulted in a ransom payment of $22 million. The likely cause was an employee being infected with Infostealing malware.
To demonstrate the prevalence of Infostealer infections, Hudson Rock researchers tracked all compromised remote accesses offered for sale by Initial Access Brokers (IABs) on underground cybercrime forums during April 2024. The researchers concluded that many of these offerings are highly correlated with Infostealing malware.
Findings
Hudson Rock researchers discovered that in April 2024 alone, there were 105 unique organizations whose remote access was offered for sale as part of the cybercrime monetization chain. To maintain the organizations’ anonymity, IABs collect reconnaissance data to prove the authenticity of their access. This data includes the geo-location of the victim organization, its industry, number of employees, annual revenue, and technical details such as the number of workstations.
Leveraging Hudson Rock’s expertise in cybercrime intelligence, researchers identified 33 of the 105 organizations offered for sale. Of these identified organizations, a staggering 63% had compromised corporate credentials due to employees infected by Infostealers.

Real Example & Identification
Below is a screenshot of an IAB attempting to sell corporate access to an unknown South Korean company with $13.4 billion in revenue, identified as being in the “Cable & Satellite, Telecommunications” industry.

Using Zoominfo and the descriptions from the post, Hudson Rock researchers identified the company as SK Telecom, a major South Korean company with $13.4 billion in revenue and the same industry description.
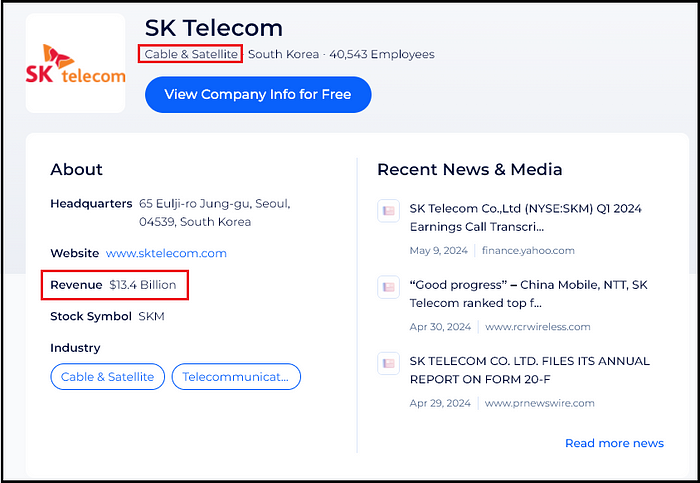
By looking up the company’s domain, sktelecom.com, in Hudson Rock’s database, it was discovered that almost 40 unique employees had their computers infected by Infostealers.

One of the most recent employees infected, on March 5, 2024, had significantly sensitive credentials such as VPN credentials to the organization.

While we cannot confirm if these credentials were used to infiltrate the organization, the high number of infected employees also indicates potential poor cyber hygiene at SK Telecom.
Additionally the threat actor mentions that they have access to the JIRA of the organization, which we identified credentials to within SK Telecom employee infections as well (Confluence) —

Infostealers as a Hot Commodity
How does Hudson Rock know that compromised data from Infostealers is used for initial access purposes?
Threat actors continuously seek “suppliers” with fresh Infostealers data to exploit sensitive credentials associated with well-known remote connections like Cisco, RDWeb, and Fortinet.
The demand for remote access is rising on high-profile cybercrime forums. In another example, a threat actor prioritized corporate access to Amazon and Tesla.
According to the screenshot below, the most common pinned threads on prominent cybercrime forums are typically requests for new remote accesses.
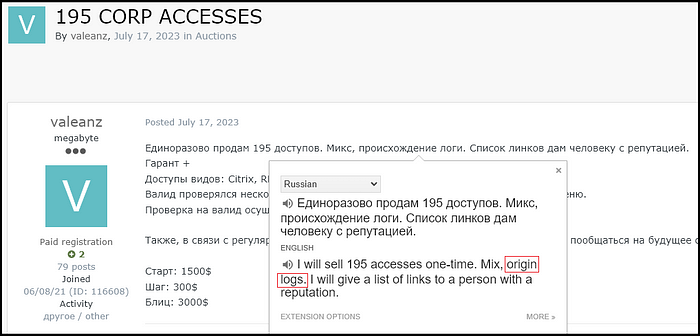
Apart from buyers, some threat actors monetize big bulks of access in one sale.
Hudson Rock researchers found a post in Russian stating that all 195 accesses originated from Infostealer attacks (происхождение логи).
Summary
Data from Infostealer logs has opened new opportunities for cybercriminals, APT groups, and even nation-state actors to find sensitive remote access to companies worldwide.
The combination of valid cookie sessions (exfiltrated during an Infostealer infection) can help attackers bypass MFA, intended to provide an additional layer of security.
According to our statistics, Infostealer infections continue to rise globally. Hudson Rock’s cybercrime intelligence database has just surpassed a worrying milestone of over 27 million historically infected computers worldwide.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
Hudson Rock provides access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools