Written by Alon Gal
A person operating under the username Nam3L3ss has exploited a critical vulnerability in MOVEit, a file transfer software, exposing extensive employee data from prominent companies worldwide.
The vulnerability, known as CVE-2023–34362, has led to one of the most substantial leaks of corporate information this year, affecting various sectors, including finance, healthcare, technology, and retail.
The MOVEit vulnerability, discovered in mid-2023, exposed a critical flaw in the widely-used file transfer software, allowing hackers to bypass authentication and access sensitive data. This exploit was quickly weaponized, leading to numerous high-profile breaches across industries as attackers exfiltrated confidential employee and customer information from vulnerable systems.
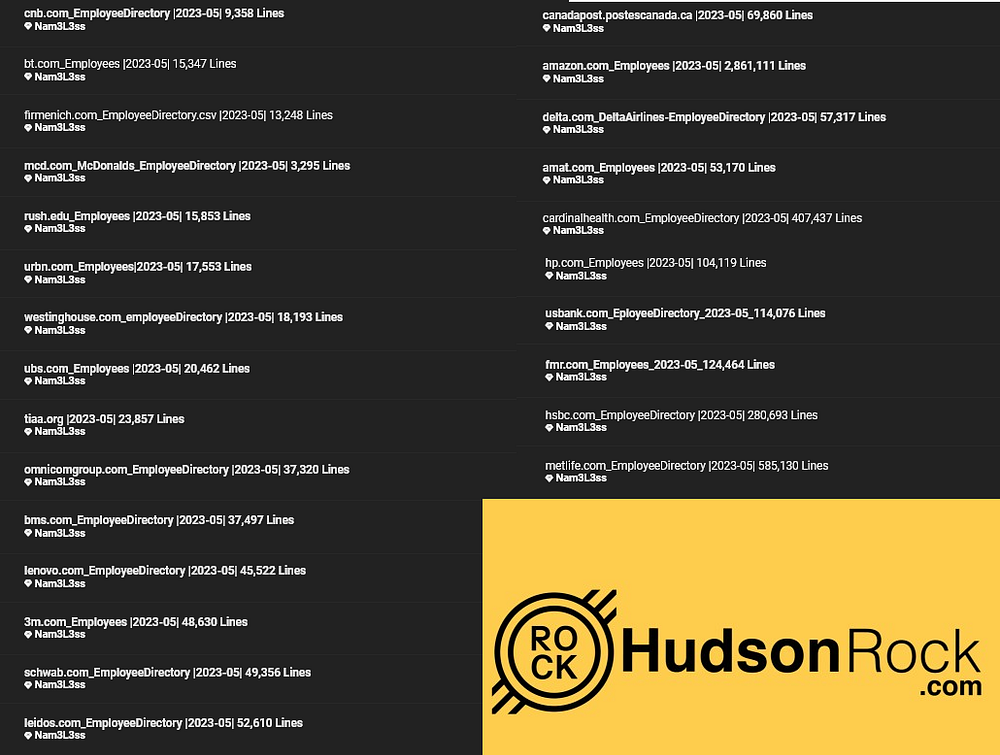
The stolen data, which dates back to May 2023, includes employee directories from 25 major organizations. The directories contain detailed employee information, including names, email addresses, phone numbers, cost center codes, and, in some cases, entire organizational structures. Such data could serve as a goldmine for cybercriminals seeking to engage in phishing, identity theft, or even social engineering attacks on a large scale.
A Timeline and Scope of the Breach
The leaked data, organized by company and dated May 2023, includes detailed employee records from some of the world’s largest companies, many with substantial global footprints. This breach emphasizes the far-reaching impact of MOVEit’s vulnerability and the risks involved when security patches aren’t applied swiftly. Here’s a breakdown of the leak by company:
Companies Impacted and Record Counts:
- Amazon — 2,861,111 records
- MetLife — 585,130 records
- Cardinal Health — 407,437 records
- HSBC — 280,693 records
- Fidelity (fmr.com) — 124,464 records
- U.S. Bank — 114,076 records
- HP — 104,119 records
- Canada Post — 69,860 records
- Delta Airlines — 57,317 records
- Applied Materials (AMAT) — 53,170 records
- Leidos — 52,610 records
- Charles Schwab — 49,356 records
- 3M — 48,630 records
- Lenovo — 45,522 records
- Bristol Myers Squibb — 37,497 records
- Omnicom Group — 37,320 records
- TIAA — 23,857 records
- Union Bank of Switzerland (UBS) — 20,462 records
- Westinghouse — 18,193 records
- Urban Outfitters (URBN) — 17,553 records
- Rush University — 15,853 records
- British Telecom (BT) — 15,347 records
- Firmenich — 13,248 records
- City National Bank (CNB) — 9,358 records
- McDonald’s — 3,295 records
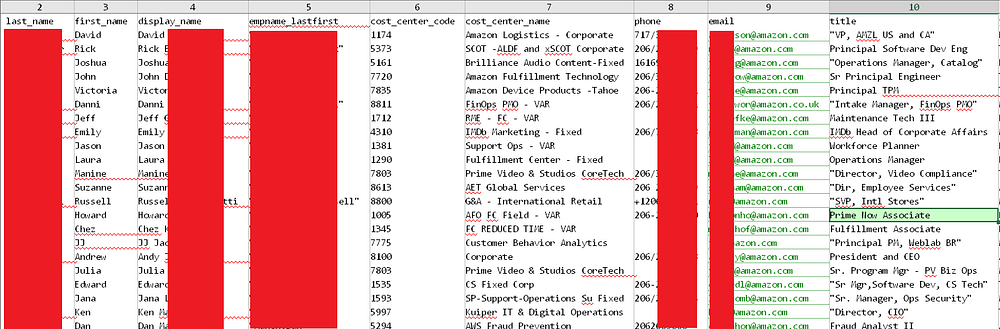
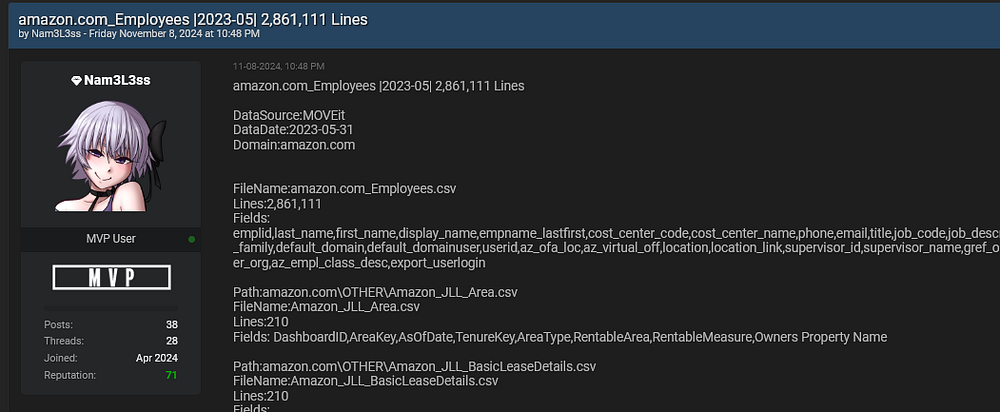
As part of the recent MOVEit vulnerability breach, vast datasets from companies like Amazon and HSBC were exposed, providing insight into the structure and details of the data compromised. The Amazon dataset, for example, contains records for employees that include fields like last_name, first_name, display_name, cost_center_code, cost_center_name, phone, email, and title.
This structured data reveals not only contact information but also sensitive details about organizational roles and department assignments, potentially opening doors to social engineering and other security threats.
Similarly, the HSBC dataset includes structured fields such as user_id, first_name, last_name, email_address, employee_status, company_code, city, and state.
This information spans HSBC’s global operations, listing employees in locations across the UK, India, and other countries, along with their specific branch or department codes. This level of data granularity, combined with personal identifiers, underscores the critical impact of the MOVEit breach on corporate security and employee privacy.
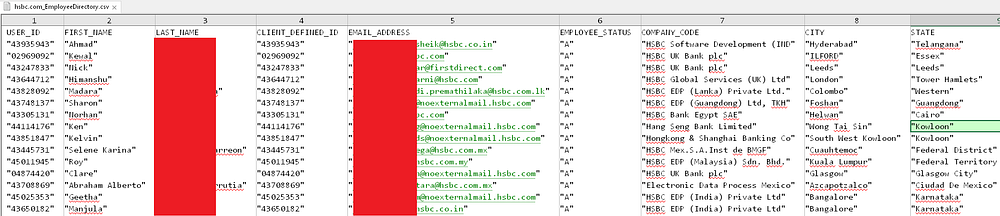
Hudson Rock researchers were able to verify the authenticity of the data by cross-referencing emails from the leaks to Linkedin profiles of employees, and to emails found in Infostealer infections where employees in the affected companies were involved.
The Hacker’s Approach and Initial Discovery
The hacker, Nam3L3ss, posted these files on a prominent cybercrime forum, each thread showing a trove of sensitive information in a CSV format.
In a public post, Nam3L3ss warned companies and individuals to “pay attention” to the magnitude of these leaks, emphasizing the types of details accessible, including cost center codes and in some cases, internal organizational structures.
Example post from Nam3L3ss:
“Folks, PLEASE Pay Attention, these are Company Employee Directories, some sites have the Organizational Structure and even other Files.”
The hacker’s message suggests an intent to make organizations aware of the potential threats and weaknesses in their systems, while also publicizing the data for malicious actors who may misuse it.
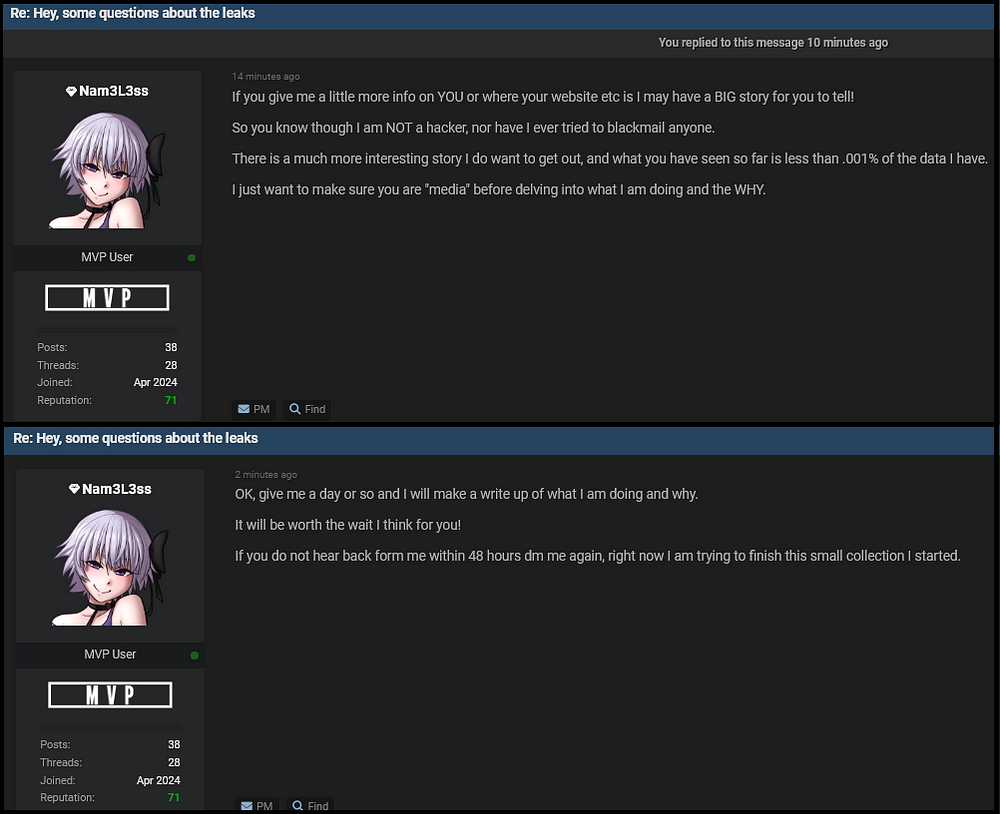
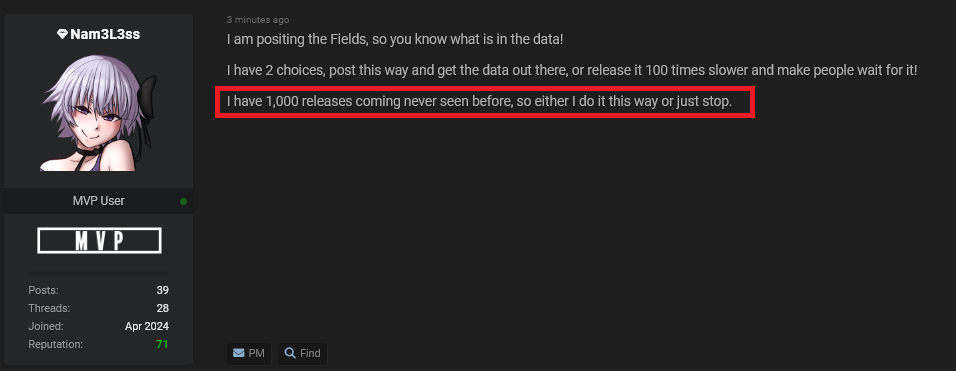
In addition to that, Hudson Rock researchers reached out to Nam3L3ss who claims the breach is just a tiny portion of the data they have which they intent to share more about in the next few days (make sure to re-visit this blog!), this is what they had to say:
Potential Risks and Consequences
This breach holds severe implications, not only for the companies involved but also for the individual employees whose data has been compromised. The depth and granularity of information provide ample opportunity for cybercriminals to conduct highly targeted attacks. Key risks include:
- Phishing and Social Engineering Attacks: With contact details, names, and organizational structures available, cybercriminals can tailor phishing emails to appear more legitimate and bypass security checks.
- Corporate Espionage: Access to hierarchical structures and employee details offers opportunities for corporate spying, giving competitors or malicious entities insights into internal operations.
- Reputational Damage: High-profile companies like Amazon, HSBC, and MetLife are particularly vulnerable to the reputational impact of such breaches, as clients and customers grow increasingly concerned about data security.
- Financial Theft and Fraud: Financial sector data, such as that of Cardinal Health and UBS, is particularly attractive for theft and fraud. Having employee records and communication channels can aid in more sophisticated fraud schemes targeting these organizations.
Mitigation Steps and Security Best Practices
For companies using MOVEit or similar file transfer systems, the incident is a wake-up call. Here are a few key actions to help protect against similar breaches:
- Apply Security Patches Immediately: MOVEit has released patches to address CVE-2023–34362. Organizations should ensure these updates are applied without delay.
- Conduct a Comprehensive Security Audit: Companies impacted by this breach or using MOVEit should conduct a security audit, identifying any potential vulnerabilities that could lead to further exposure.
- Employee Awareness and Training: Employees are often the first line of defense against social engineering attacks. Companies should reinforce training around phishing recognition, safe data handling, and secure communication practices.
- Limit Access and Implement Data Segmentation: By restricting data access based on roles and implementing robust data segmentation, organizations can reduce the amount of sensitive information accessible to hackers if they gain entry to a system.
Conclusion
This breach serves as a powerful reminder of the critical importance of rapid vulnerability management and proactive cybersecurity measures. As cyber threats continue to evolve, every organization, regardless of industry, must prioritize a culture of cybersecurity vigilance and resilience.
For companies impacted, it’s essential to conduct thorough incident response actions, protect affected employees, and rebuild client trust. Moving forward, the MOVEit incident underlines the importance of staying updated on vulnerabilities, especially for any software used to manage or transfer sensitive data.
To learn about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock