The rise of infostealer malware has become a serious challenge for organizations worldwide.
These sophisticated malware types are designed to stealthily infiltrate systems, extract sensitive information, and pave the way for more destructive cyberattacks.
The following cases, involving high-profile companies, underscore the critical importance of robust cybersecurity measures. These incidents not only highlight the vulnerabilities that organizations face but also the crucial role of cybersecurity firms mitigating these threats.
Here, we dive into five significant breaches that shook the corporate world, each a reminder of the persistent and evolving nature of cyber threats.
1. Orange Spain Breach
Orange Spain’s network faced a severe disruption when a hacker exploited their RIPE account, leading to a major internet outage. This breach was traced back to an infostealer malware infection on an employee’s computer, which compromised critical credentials.
Hudson Rock’s cybersecurity intelligence was instrumental in uncovering the breach, revealing that the stolen credentials were part of a larger collection of data obtained through information-stealing malware. This incident highlights the necessity of enhanced security protocols, including multi-factor authentication, to safeguard against such advanced cyber threats.

2. CircleCI Data Breach
CircleCI, a prominent continuous integration and delivery platform, confirmed a data breach originating from an infostealer malware on an employee’s laptop. This breach, undetected by the company’s antivirus program, led to unauthorized access to a subset of CircleCI’s databases. The incident underscores the need for advanced malware detection tools and strict control over access to sensitive data in corporate environments.
3. Airbus Suppliers Data Leak
A cybercriminal, identified as USDoD, exploited the RedLine infostealer to access and leak data from 3,200 Airbus suppliers. The breach was executed through a compromised system of a Turkish airline employee, leading to the exposure of sensitive information from numerous military-linked corporations.
Hudson Rock’s prompt detection and alert to Airbus were key in managing this crisis. This breach serves as a reminder of the ongoing cyber warfare in the aerospace industry and the importance of continuous vigilance.

4. Breach Involving 120,000 Hackers
Hudson Rock discovered credentials linked to cybercrime forums on about 120,000 computers infected with information stealers. This finding was part of a larger analysis of millions of infected machines, many owned by hackers themselves. This scenario illustrates the widespread and indiscriminate nature of cyber threats, affecting even those within the hacker community. Hudson Rock’s insights into this breach offer a unique perspective on the complexities of the cybercrime ecosystem.

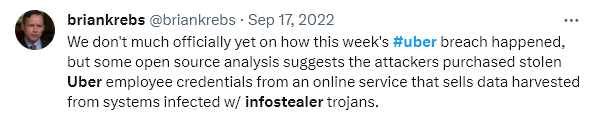
5. Uber Infostealer Attack
Uber experienced a significant security breach when a threat actor deployed the Raccoon stealer to compromise its systems. The attacker used a deceptive two-factor authentication notification to gain access to Uber’s internal network, escalating privileges and accessing various critical resources. This breach at Uber is a stark reminder of the advanced tactics employed by cybercriminals and the continuous need for robust cybersecurity strategies.
It is important to routinely check your organizational exposure to Infostealer infections which are the top initial attack vector for threat actors to access corporate and customer accounts.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock