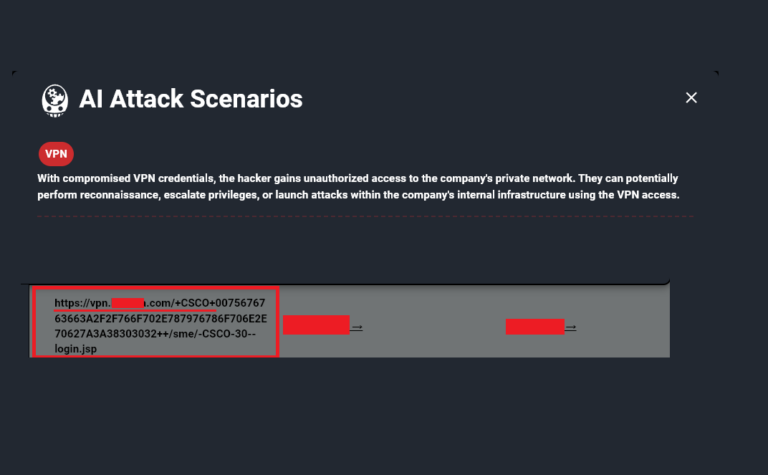
How Hackers Really Used Infostealers for the Biggest Recent Cyber Breaches
We are now at a point where numerous cyberattacks have been carried out using compromised Infostealer data. Major companies such as AT&T, Ticketmaster, Orange, Airbus,
Home » Hackers

We are now at a point where numerous cyberattacks have been carried out using compromised Infostealer data. Major companies such as AT&T, Ticketmaster, Orange, Airbus,
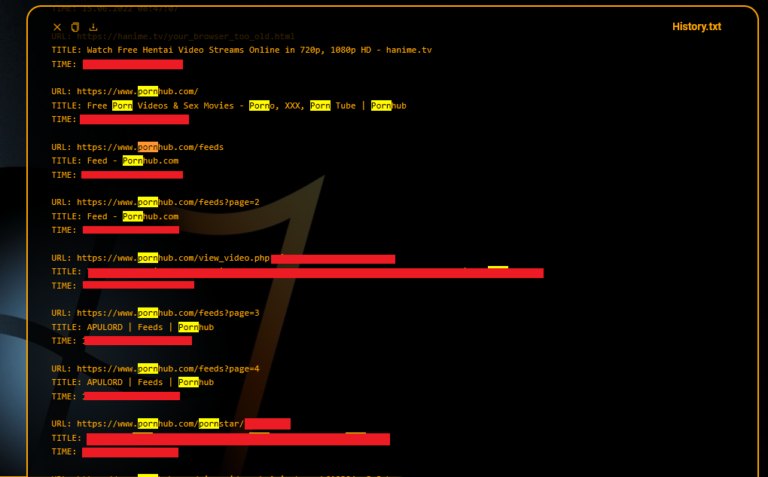
Sextortion schemes are about to take a much darker turn. With the rise of Infostealer malware, the game is changing. Hackers will no longer rely

What do Andrew Tate, a Pro-Palestine hacking group, and AnyDesk all have in common? For a while now, Infostealer credentials data has been used as
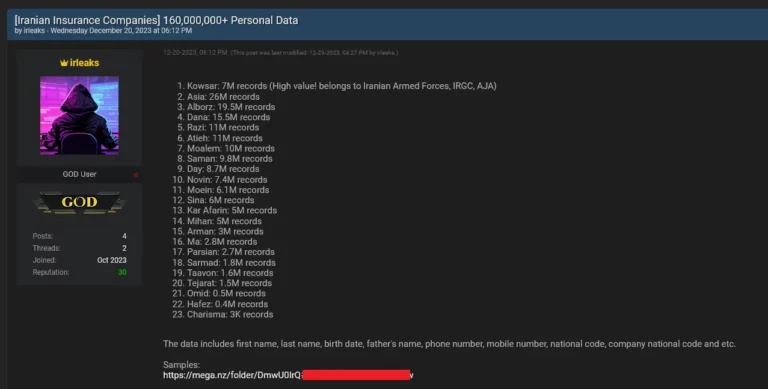
A hacker who goes by the username “irleaks” posted a thread in which they attempt to sell over 160,000,000 records of Iranians…

During the summer of 2023, cyberattacks rose significantly, according to data from the new quarterly BlackBerry Global Threat Intelligence Report, November 2023 edition…

Windows and macOS systems have been subjected to attacks leveraging the novel Go-based information-stealing malware JaskaGO, reports The Hacker News…
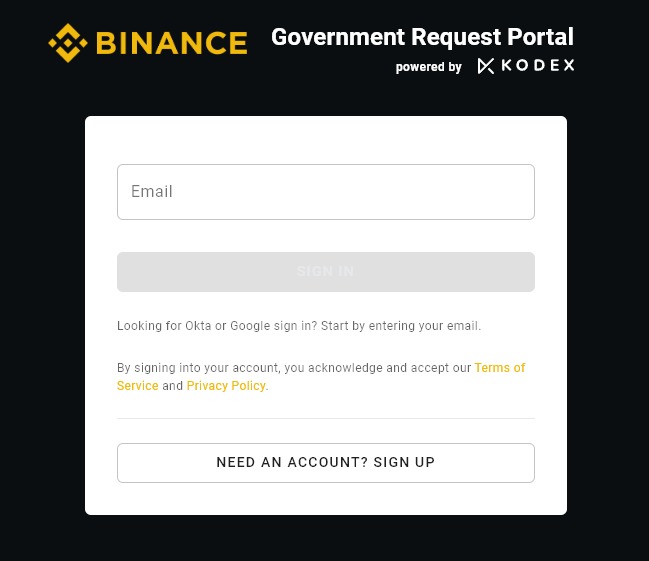
A threat actor attempts to sell access to a sensitive area of Binance — the major cryptocurrency exchange’s…
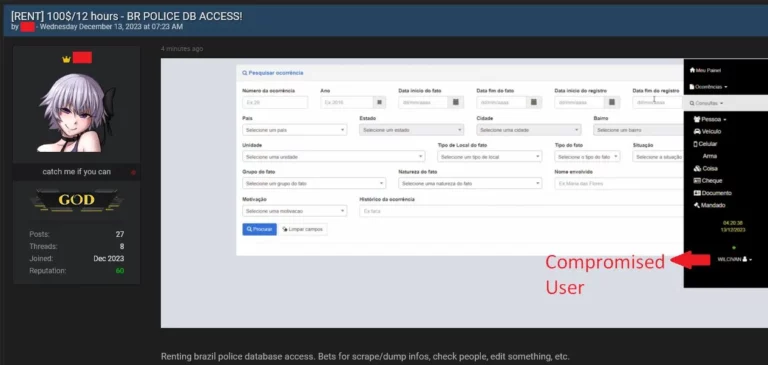
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…
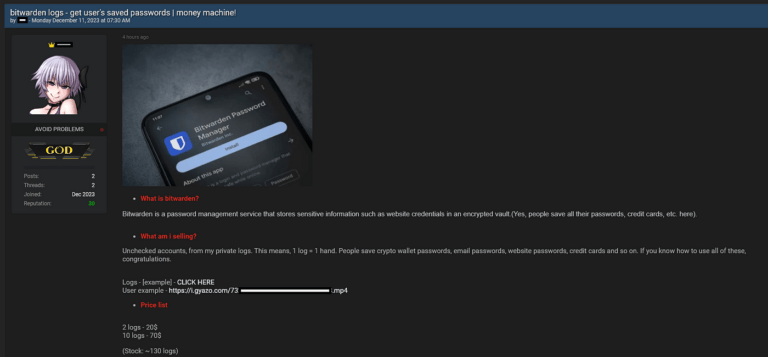
In today’s digital landscape, the reliance on password managers has become commonplace, providing users with a sense of security…
In a significant development, the creators of the well-known Infostealer group, Lumma, have reportedly made a groundbreaking discovery…

Using Hudson Rock’s cybercrime intelligence database, which consists of over 14,500,000 computers infected by info-stealing malware…

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
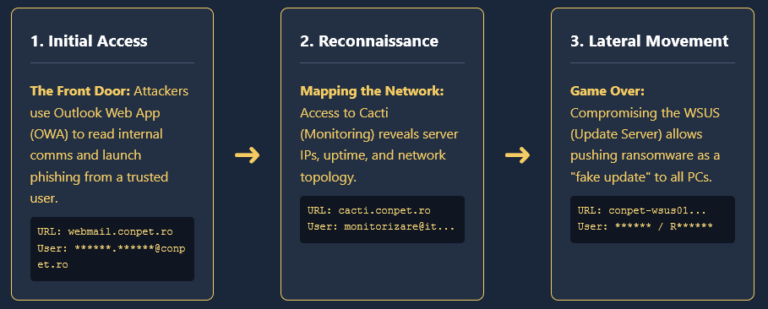
Conpet Hacked: Infostealer Analysis Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack February 2026 – The Romanian
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
