Part 1 of a 3 Part Series in Collaboration with Cyrus: Info-Stealers
The following post, a first of a three part series, is presented in collaboration with Cyrus.
Intro
When somebody offers you something that is too good to be true, you should always think twice. As the old saying goes, “There is no such thing as a free lunch,” and that couldn’t be more relevant today in light of emerging threats to personal cybersecurity.
Simply downloading a pirated version of Photoshop to edit your photos, opening an email with a PDF file that invites you to a free vacation in the Maldives, or even clicking on a link for additional COVID-19-related benefits, can turn an apparent freebie (the “free lunch”) into a costly compromise of your device.
Cyrus and Hudson Rock, both founded by cybersecurity experts, partnered together to bring state-of-the-art cybercrime intelligence to the consumer sector which until now was only available to major corporations and government agencies.
In this first of a three-part blog post series, Cyrus and Hudson Rock will explain what an info-stealer is, as well as provide steps and tips on how to protect yourself against this threat.

A user downloads a pirated version of Photoshop merged with an info-stealer.
What is an “info-stealer”?
An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data. These include:
- Credentials: Info-stealers collect login links, usernames, and passwords stored in browsers like Google Chrome.
- Cookies: These enable malicious actors to access a logged-in user’s session and bypass traditional security measures like two-factor authentication (2FA).
- Documents and text files: Info-stealers know to discover and target high-risk ones with financial information, corporate data, secret keys, 2FA backup codes, server passwords, crypto private keys, etc.
- Machine-specific properties: This captured data is more technical, such as the name of the computer, the operating system, the IP address, the date and pathway of infection, as well as existing antivirus and installed applications.
Through its partnership with Hudson Rock, Cyrus is able to access a database of over 5,200,000 computers, which were compromised through global info-stealer campaigns performed by hackers.
How is this possible? I have the latest antivirus software.
Cyrus & Hudson Rock’s joint analysis revealed that when a user clicks and launches an infected file (thereby authorizing the action) antiviruses are rendered useless in preventing infections. That’s why both built-in defenses like Windows Defender and paid antivirus software from major vendors like Norton and Kaspersky struggle to prevent these types of attacks.
The fact of the matter is that antiviruses cannot provide 100% protection due to human error.
According to a recent analysis of 100,000 compromised devices, 88% of the devices had different antivirus software that the info-stealer managed to bypass.

An info-stealer that managed to bypass Kaspersky’s antivirus software
Your password is clearly exposed. Always.
Although companies and websites have started storing an encrypted version of credentials in order to fight against data breaches and increase cybersecurity protection, this is by no means a panacea. — even encrypted passwords can be cracked as a result of users recycling the same password across multiple accounts.
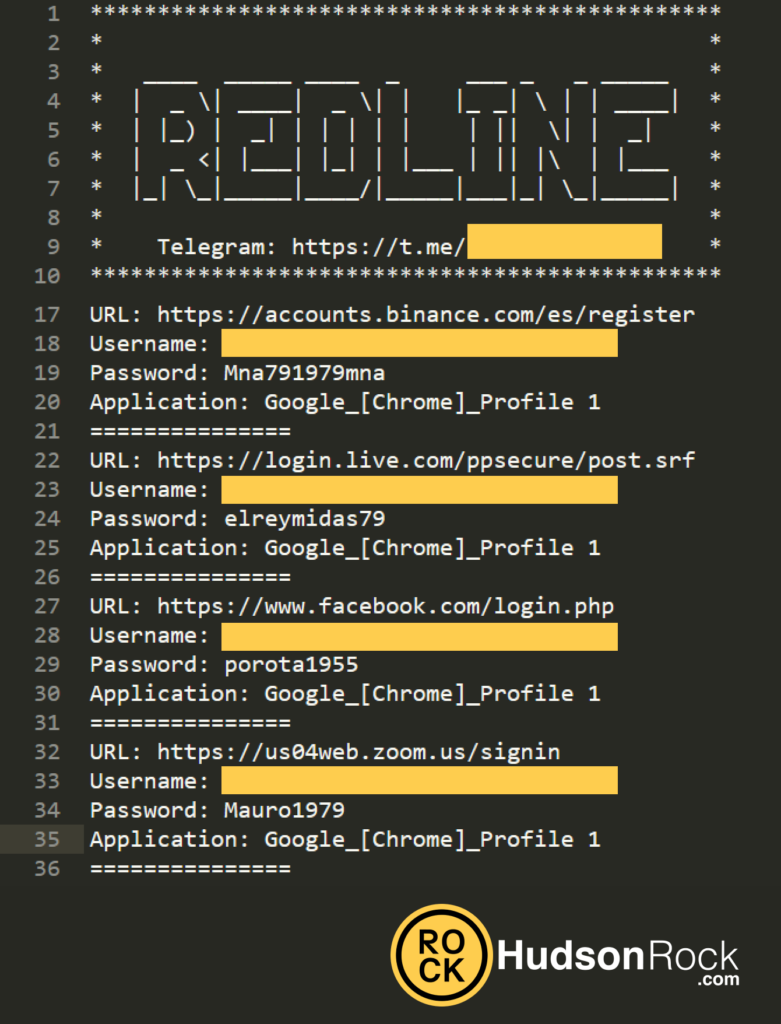
Info-stealers capture passwords which users allow to be automatically saved in browsers when they sign in to websites. The passwords are then decoded, which is why they are always in plaintext rather than in encrypted form. This enables threat actors to effortlessly hack into user accounts and corporate networks as even the most complex passwords are presented clearly with the corresponding login details and login links.
For example, Cyrus personally handled an incident in which a user’s device had been fully compromised, exposing over 400 credentials tied to various financial institutions and online portals.
Unlike a third-party breach, which compromises you along with millions of other individuals, an info-stealer infection turns your personal device into an entire private breach.

But I have a password manager…
Password managers can be very useful in generating long and complex passwords that we don’t need to remember. This helps us not reuse the same password across different accounts. However, they become irrelevant when credentials are stored in a browser and are vulnerable to info-stealer attacks.

Summary
The average person manages more than 100 online accounts, making them more inclined to rely on in-browser password managers. This inspires cybercriminals to develop the most advanced tools and malicious software that will reach and steal their most valuable information.
The odds of falling prey to an info-stealer attack have increased dramatically as a result of the relative ease of access to info-stealers on the Dark Web, and the option to either merge them with pirated content or attach them to a variety of infected spam emails.
It is crucial for individuals to adopt proper cyber hygiene practices and exercise caution when handling links and software, including avoiding those from an unknown source.
Stay tuned for the second installment in the series which will cover how the info-stealer affects the US market and how the “work-from-home” era has increased this type of attack.