
Hudson Rock Announces First Comprehensive Infostealers AI Bot: CavalierGPT
Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data
Home » You searched for hudson rock

Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data
We scrambled to launch BlackBastaGPT super fast after the latest Black Basta leak hit to get you immediate value. Find it here – www.hudsonrock.com/blackbastagpt This

Hudson Rock has been the go-to source for all things cybersecurity and infosec updates. Be it offering dark web intelligence or finding one’s own data

December 10, 2024 – Hudson Rock, a leader in cybercrime intelligence, is proud to announce the official launch of CavalierGPT, the industry’s first AI-powered bot
We’re excited to announce a game-changing addition to Hudson Rock’s capabilities: our innovative AI agent, Enki, engineered to transform how you tackle Infostealer infections. With
🔊 *Hudson Rock* is back with a new podcast episode! In this episode, Leonid Rozenberg, cybercrime and threat intelligence researcher, speaks with Kevin Poireault from

Hudson Rock’s data exploration capabilities allow for seamless analysis of massive amounts of assets associated with Infostealer infections. In this example, we analyze all domains

Hudson Rock’s Infostealer Investigation Module provides cybersecurity professionals the ability to investigate all the data captured from an Infostealer infection of employees and customers at

Hudson Rock’s database, with tens of millions of computers infected worldwide, enables cybersecurity and law enforcement customers to investigate suspicious infected computers that are using

Learn about Infostealers with actual real life breaches caused by Infostealer infections with Leonid Rozenberg, Hudson Rock’s Head of Partnerships & Integrations. To discover how

In this Help Net Security interview, Alon Gal, CTO at Hudson Rock, discusses integrating cybercrime intelligence into existing security infrastructures. Our discussion will cover a range

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
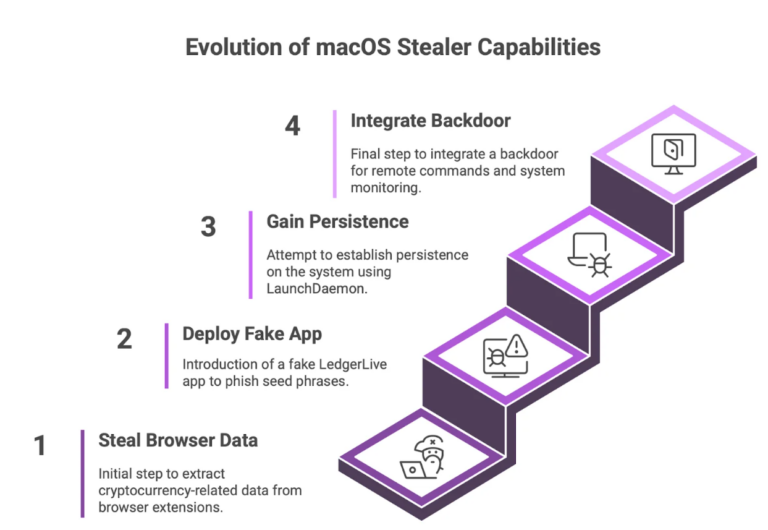
Atomic macOS Stealer (AMOS), a popular piece of stealer malware for macOS, has just received a major update. For the first time, it’s being deployed

At SINCON 2025 in Singapore, Leonid Rozenberg sat down with cyber journalist Jane Lo for a brief but powerful 15-minute interview that catches you up

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
