
Infostealers Webinar – Hudson Rock
Learn about Infostealers with actual real life breaches caused by Infostealer infections with Leonid Rozenberg, Hudson Rock’s Head of Partnerships & Integrations. To discover how
Home » Infostealers » Page 2

Learn about Infostealers with actual real life breaches caused by Infostealer infections with Leonid Rozenberg, Hudson Rock’s Head of Partnerships & Integrations. To discover how

Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on
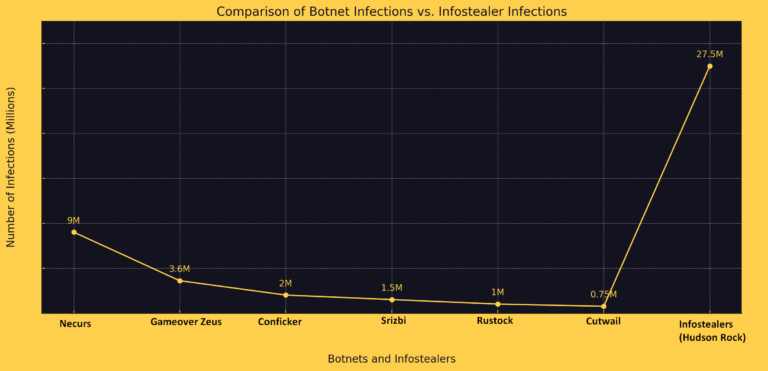
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of
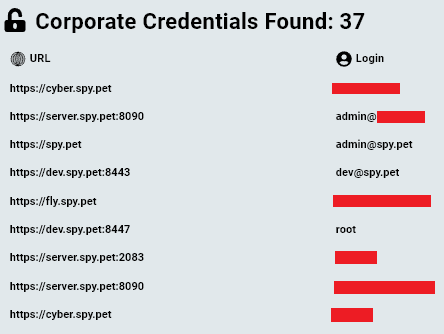
This article aims to shed light on the identity behind a massive Discord spying tool and raise concerns about the possibility of private Discord data
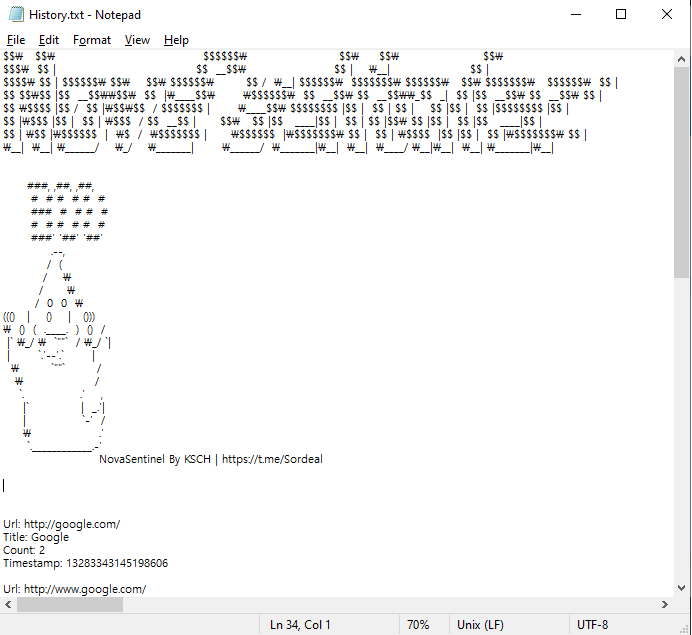
AhnLab SEcurity intelligence Center (ASEC) has discovered an Infostealer strain made with Electron. Electron is a framework that allows one to develop apps using JavaScript,

Group-IB discovers new information stealer targeting Vietnam with rare functionality to filter out Facebook accounts with advertising credits…

What do Andrew Tate, a Pro-Palestine hacking group, and AnyDesk all have in common? For a while now, Infostealer credentials data has been used as

Executive Summary Unit 42 researchers recently discovered activity attributed to Mispadu Stealer, a stealthy infostealer first reported in 2019. We found this activity as part

_OVERVIEW Pony (also known as Fareit or Siplog) is a malware categorized as a loader and stealer, although it is also used as a botnet,

Edit 03/02/24 – ‘Tamagami’ reveals they also possess access to Kodex which enables EDR / Subpoena requests for services such as LinkedIn, Discord, Tinder, Binance,

Affected platforms: All platforms where PyPI packages can be installedImpacted parties: Any individuals or institutions that have these malicious packages installedImpact: Leak of credentials, sensitive information, etc.Severity level: High

The rise of infostealer malware has become a serious challenge for organizations worldwide. These sophisticated malware types are designed to stealthily infiltrate systems, extract sensitive

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
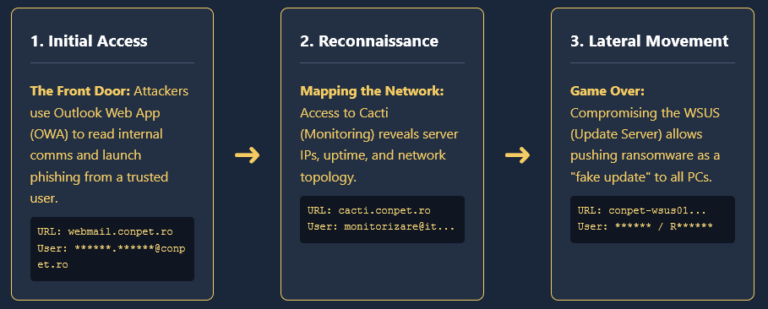
Conpet Hacked: Infostealer Analysis Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack February 2026 – The Romanian
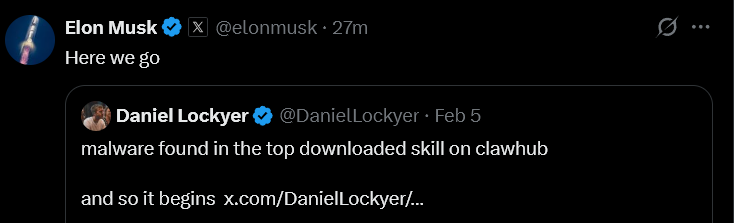
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
