Edit 03/02/24 – ‘Tamagami’ reveals they also possess access to Kodex which enables EDR / Subpoena requests for services such as LinkedIn, Discord, Tinder, Binance, Coinbase, Chainlink, SendGrid, and others

A worrying trend emerges as threat actors hack into the law enforcement systems of major organizations, gaining the ability to legally request personal details of users. This abuse often leads to identity thefts, extortion, and financial losses.
Just weeks ago we wrote about Binance and Brazil’s police suffering similar breaches due to Infostealer infections. Today, Google, TikTok, and Meta are also affected.
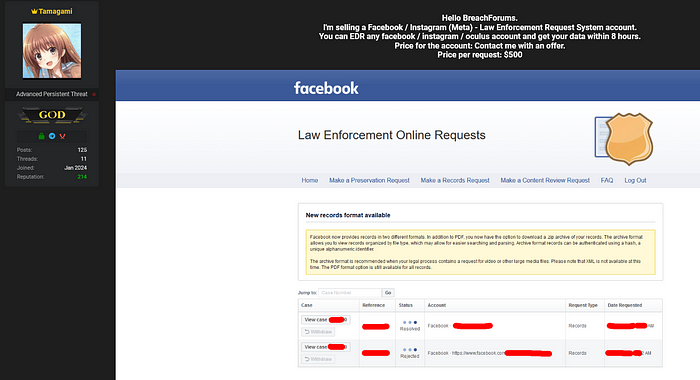
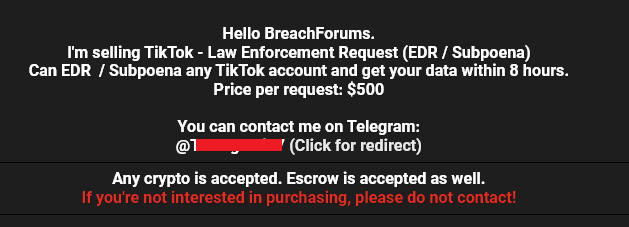
A threat actor who goes by the handle ‘Tamagami’ on a popular cybercrime forum has gained access to several law enforcement systems and is attempting to monetize the access in two ways:
- Selling full access to the account (price not mentioned)
- “Requests” — 1-time subpoena requests ($500)

In the past we have established that threat actors often gain access to law enforcement systems by exploiting credentials obtained from Infostealer Infections, typically those of real law enforcement officers who neglectfully have their computers compromised.
Today, Hudson Rock researchers identified over 50 different sets of credentials for Google’s law enforcement system from various Infostealer infections.
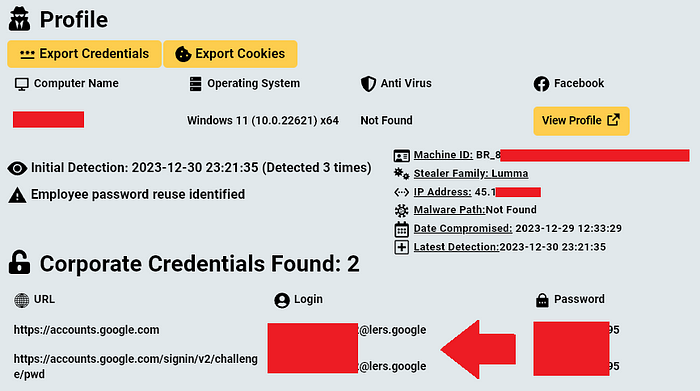
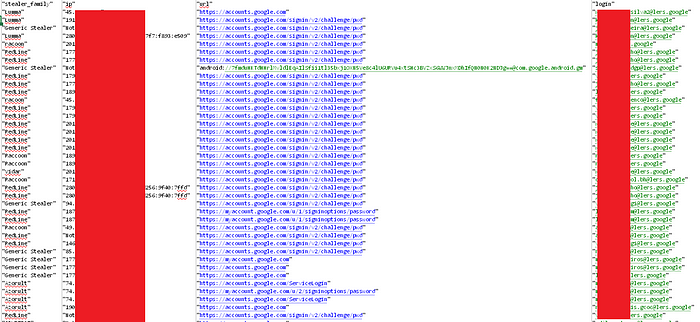
Some of these credentials are from computers we traced to infected employees at:
- Civil Police of Brazil
- Police of Arkansas (USA)
- GDF — Italian law enforcement agency under the authority of the Minister of Economy and Finance
- Government of Mexico City
- Court of Justice of the State of São Paulo
- Government of Tierra del Fuego in Argentina
- Government of the Indian state of Uttar Pradesh
- Center for Judicial Studies in Portugal
Hudson Rock estimates that it is very likely the hacker gained access to the systems using these types of credentials. Especially considering the threat actor’s posting history on the cybercrime forum, which mentions the hacker’s ability to take advantage of an allegedly legal service called IntelX. This service is intended for cybersecurity researchers to look up Infostealers related data, but it appears to be exploited by cybercriminals, potentially due to a lack of proper security management by the company.
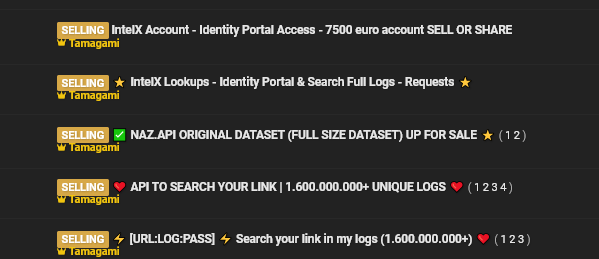
In other instances the threat actor’s posting specifically refer to their ability to “search links in logs” which refers to searching URLs within a database of Infostealers credentials datasets.
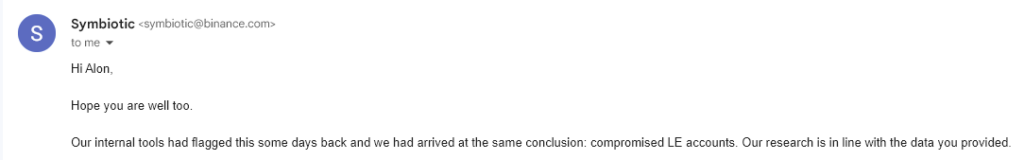
Please note that this investigation is in continuation to a similar investigation we published around a threat actor exploiting Kodex to sell access to Binance’s law enforcement panel – https://www.infostealers.com/article/hacker-sells-access-to-binances-law-enforcement-portal-cryptocurrency-holders-at-risk/
Although this was denied by Kodex and dismissed as a “scam” it is important to add that it was confirmed to us by Binance that they were aware of such access:
It is crucial for organizations to take notice of this trend and establish proper security protocols to ensure that only the legitimate owners of the accounts can access these law enforcement systems.
In order to help mitigate this issue, Hudson Rock will contact the relevant organizations and provide them with an ethical disclosure regarding the identified credentials.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock