
Botnets & Info-Stealers (Part Ⅲ)
In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…
Home » Cyrus

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
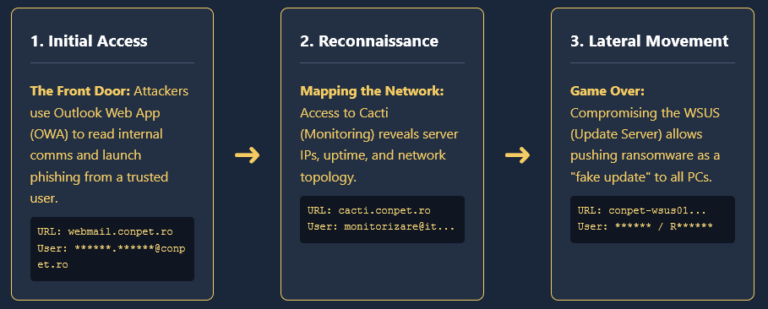
Conpet Hacked: Infostealer Analysis Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack February 2026 – The Romanian
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
