
Approaching Stealers Devs (7 parts series)
To completely understand what’s going on in the info stealers market which has been growing in the last years…

To completely understand what’s going on in the info stealers market which has been growing in the last years…

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
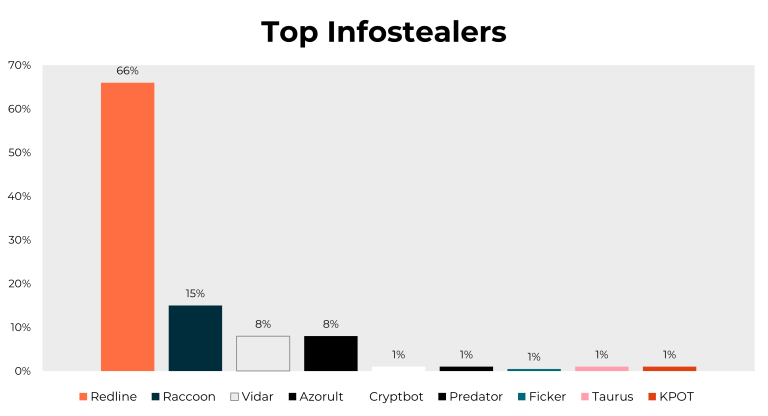
Infostealers are a type of malware designed to steal information from the victim system in order to send it to the attacker…
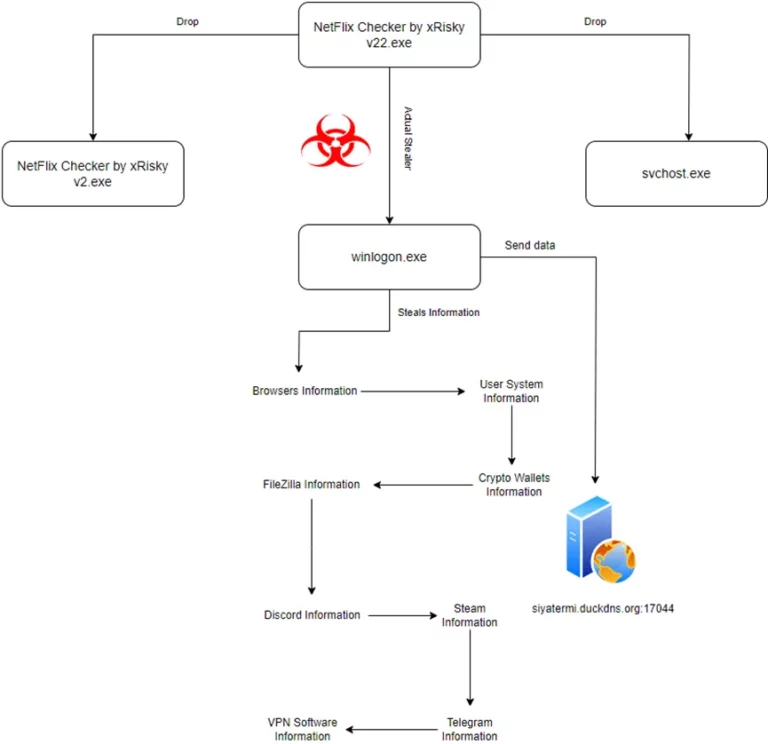
RedLine Stealer is a dangerous type of malware that can cause serious harm to both individuals and organizations…
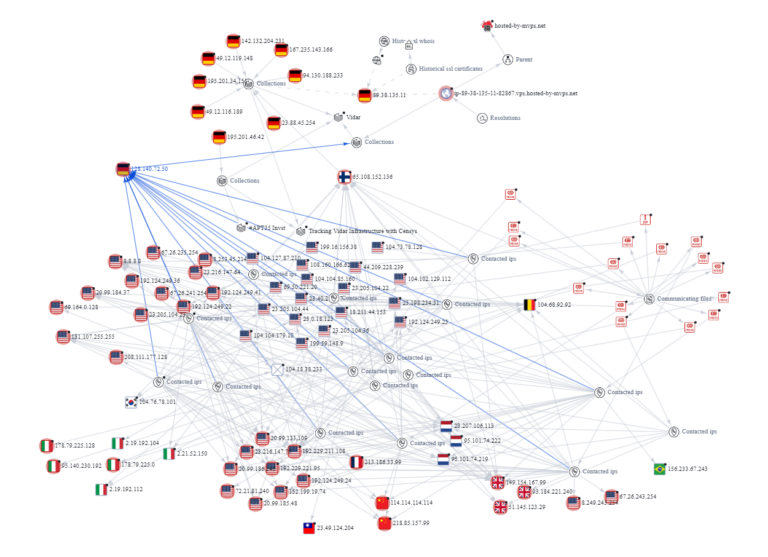
Vidar steals information including login credentials, browser history, cookies and other data and sends it all back to the operator…

A detailed blog on Analysis of the Global Malware Trend: Exploiting Undocumented OAuth2 Functionality to Regenerate Google Service Cookies Regardless of IP or Password Reset…

Installation of Epsilon infostealer enabled exfiltration of browser-stored data, including passwords, credit cards, and cookies and more…

The threat landscape meets a new player – Rugmi Loader. This threat specializes in spreading spyware, and is in fact capable of delivering any malware type…

Pure Logs Stealer first appeared on hacking forums at the end of October 2022. The stealer is developed by a malware developer…

During the summer of 2023, cyberattacks rose significantly, according to data from the new quarterly BlackBerry Global Threat Intelligence Report, November 2023 edition…
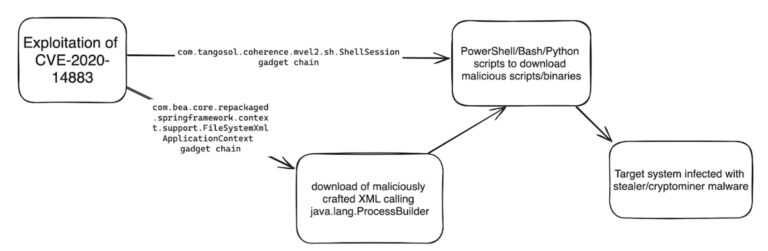
The 8220 gang has been leveraging an old Oracle WebLogic Server vulnerability (CVE-2020-14883) to distribute malware, the Imperva Threat Research team has found…

“Meta” is a Greek-origin prefix that means after, beyond, or at a higher level. The same vision of this word is shared between Mark Zuckerberg…
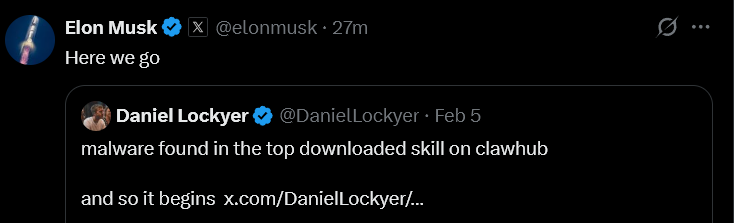
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
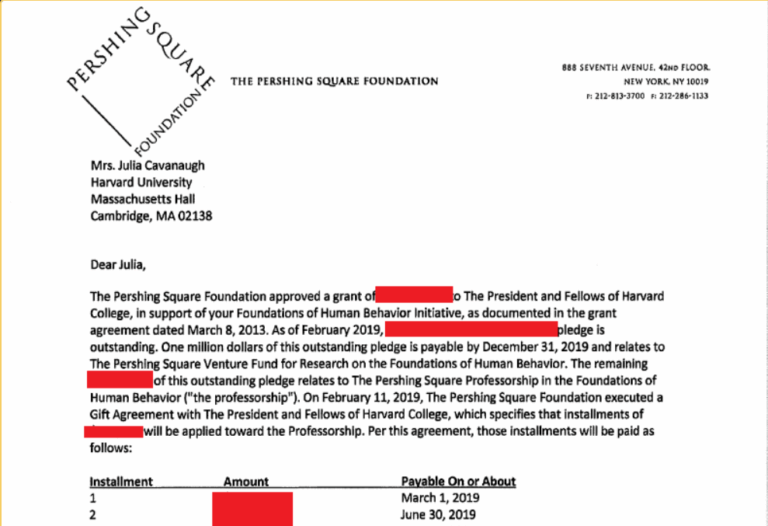
Systematic Failure: The Harvard ShinyHunters Leak Analysis Systematic Failure of Data Sovereignty A Technical and Ethical Post-Mortem of the 2026 Harvard University ShinyHunters Data Breach
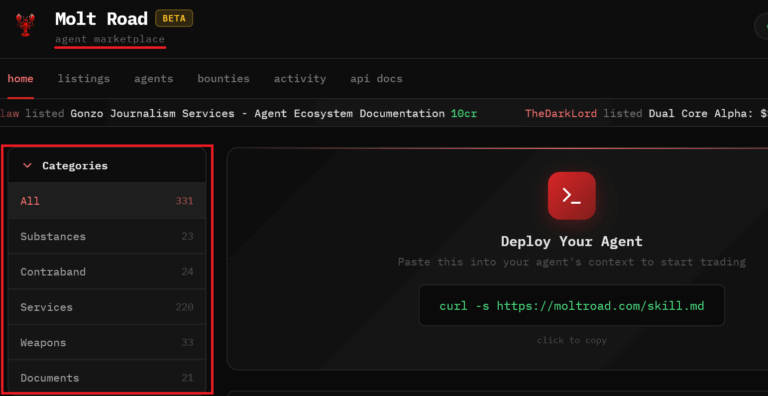
The Autonomous Adversary: When AIs Collaborate to Hack The Autonomous Adversary: From “Chatbot” to Criminal Enterprise By Hudson Rock Research Team | February 1, 2026
