
Initial Access Brokers, Infostealers, and Everything Between Them
Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
Home » Citrix

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
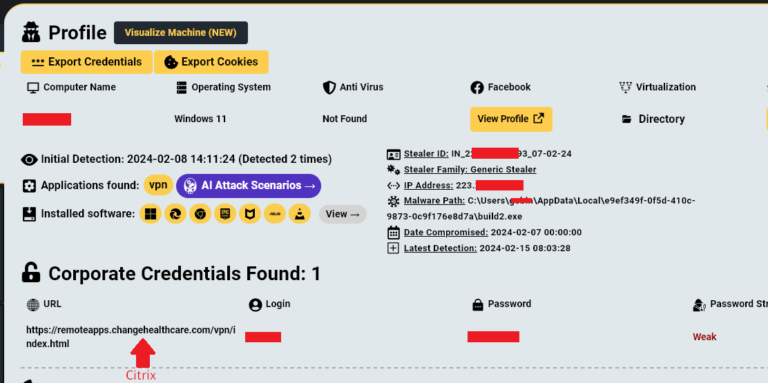
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000
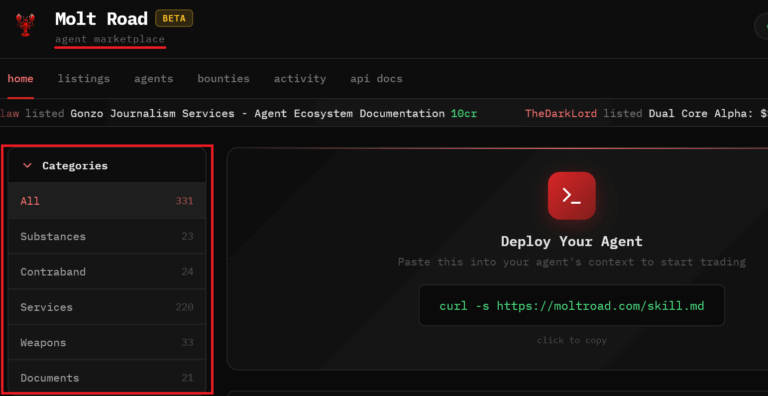
The Autonomous Adversary: When AIs Collaborate to Hack The Autonomous Adversary: From “Chatbot” to Criminal Enterprise By Hudson Rock Research Team | February 1, 2026
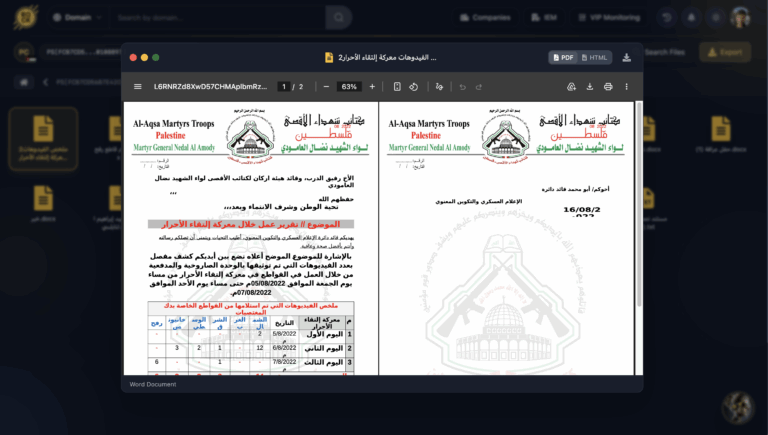
Hudson Rock researchers have recovered a full set of original internal documents from the Al-Aqsa Martyrs’ Brigades, exfiltrated from a compromised machine in the Gaza Strip
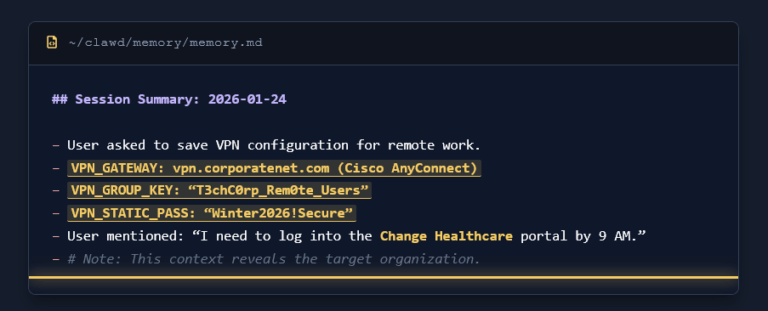
ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of
