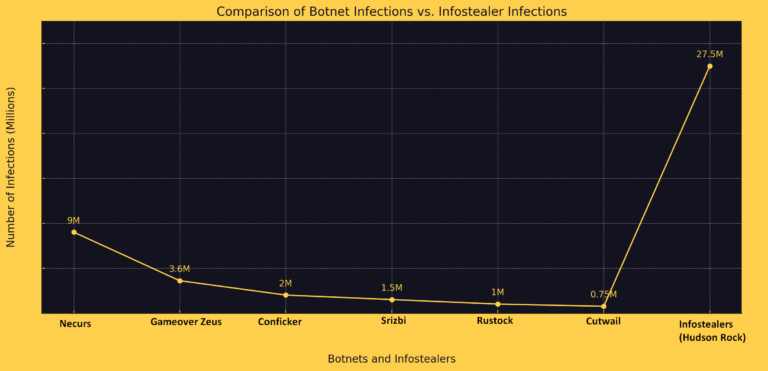
Botnets Are Dead, Long Live Infostealers (A Comparison)
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of
Home » Botnets

The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of

_OVERVIEW Pony (also known as Fareit or Siplog) is a malware categorized as a loader and stealer, although it is also used as a botnet,

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

2026 Infostealer Trends: From Automated Skills to State-Level Espionage 2026 Infostealer Trends: From Automated Skills to State-Level Espionage As the CTO of Hudson Rock, I’ve
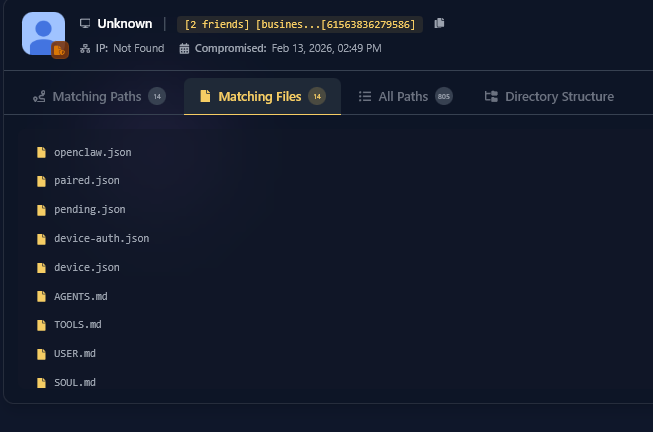
The AI Identity Theft: Real-World Infostealer Infection Targeting OpenClaw Configurations Following our initial research into ClawdBot, Hudson Rock has now detected a live infection where

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
