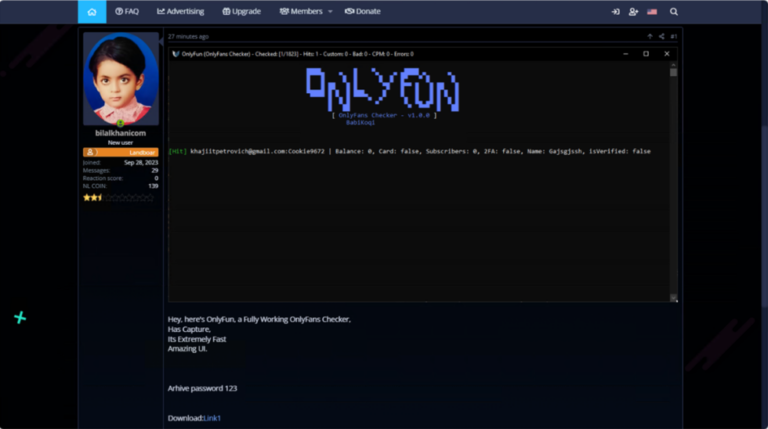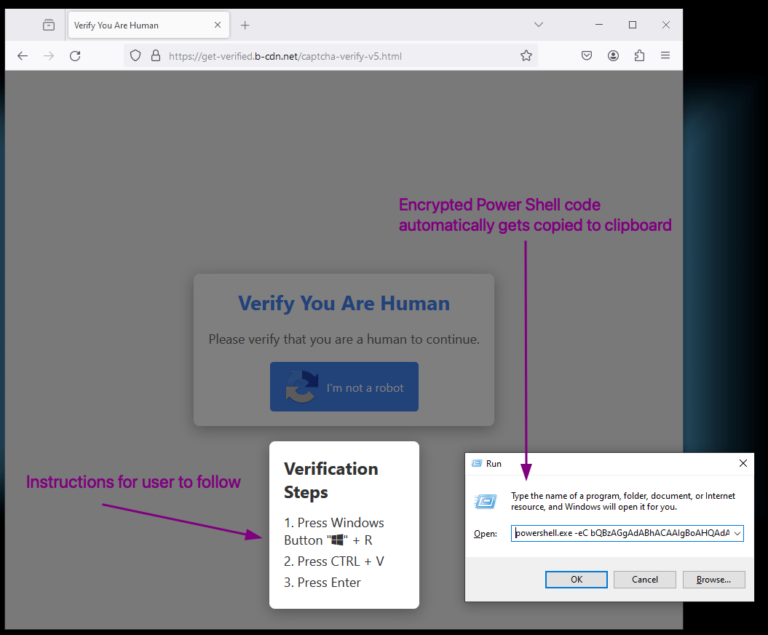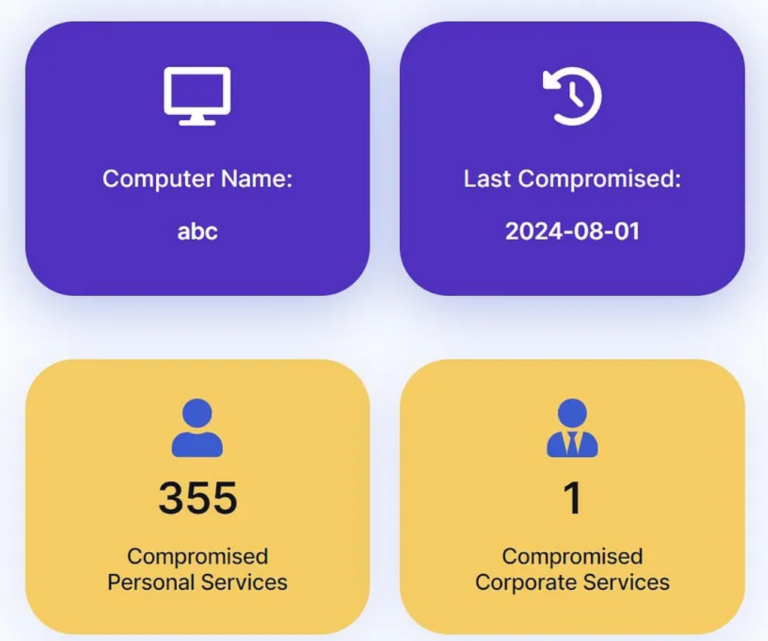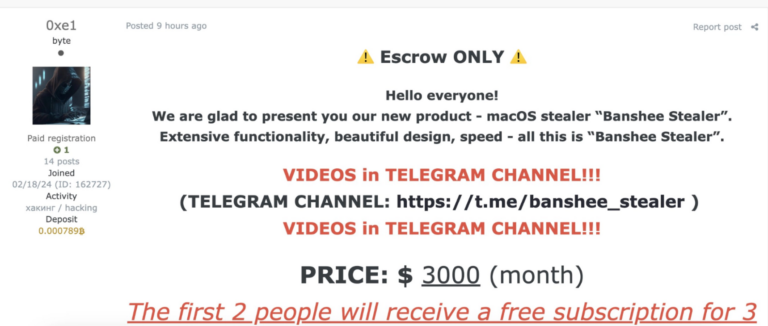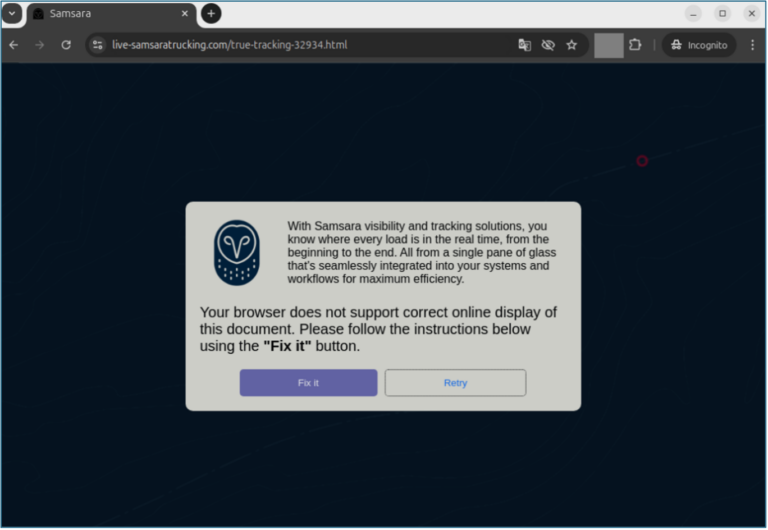
Actor Uses Compromised Accounts, Customized Social Engineering to Target Transport and Logistics Firms with Malware
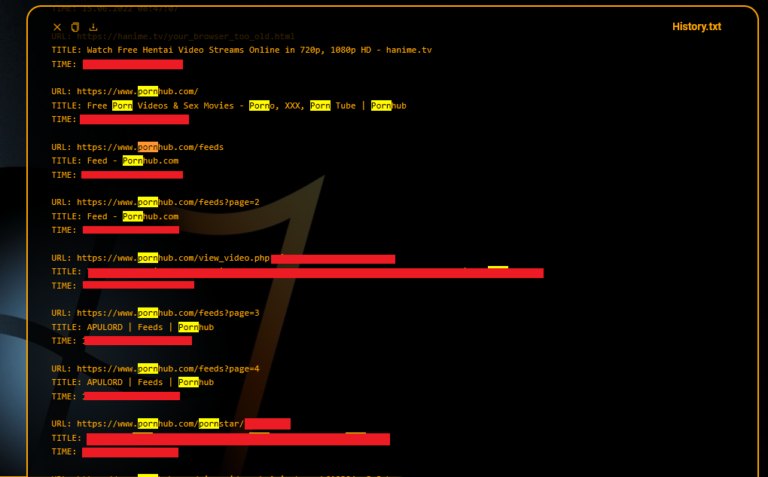
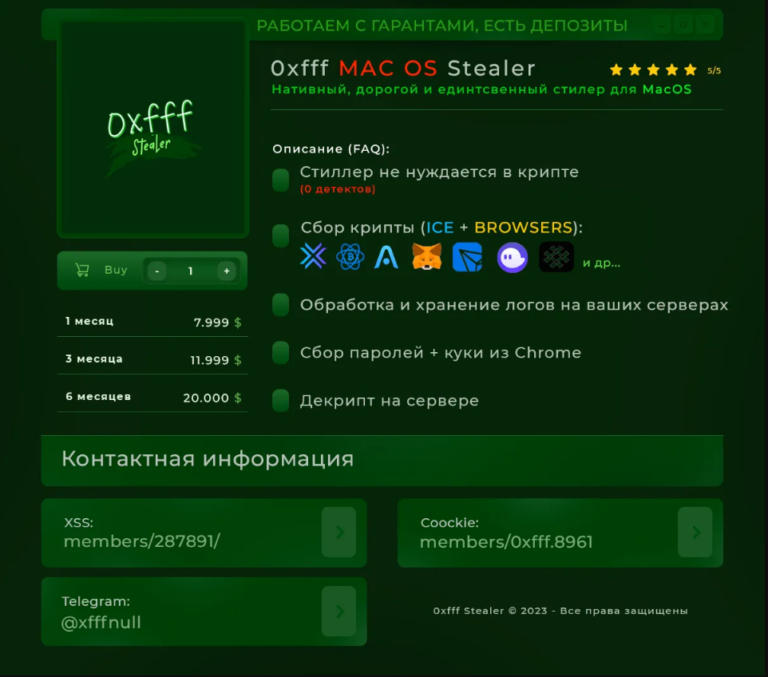
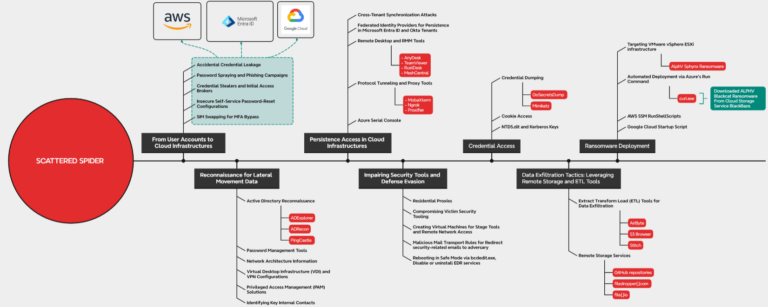
What happened Proofpoint researchers are tracking a cluster of activity targeting transportation and logistics companies in North America to deliver a variety of different malware