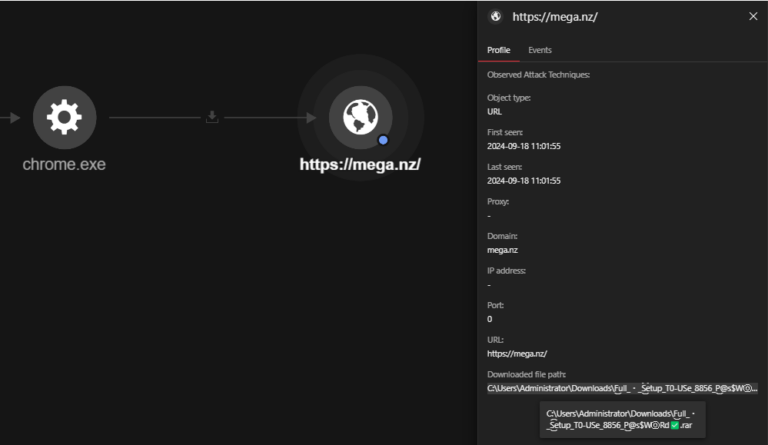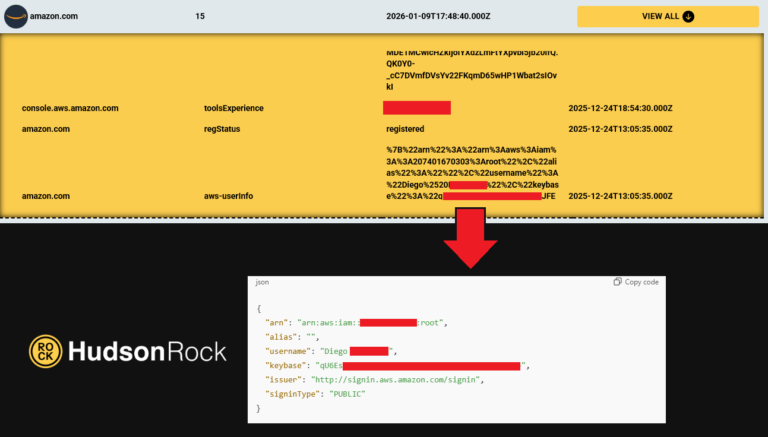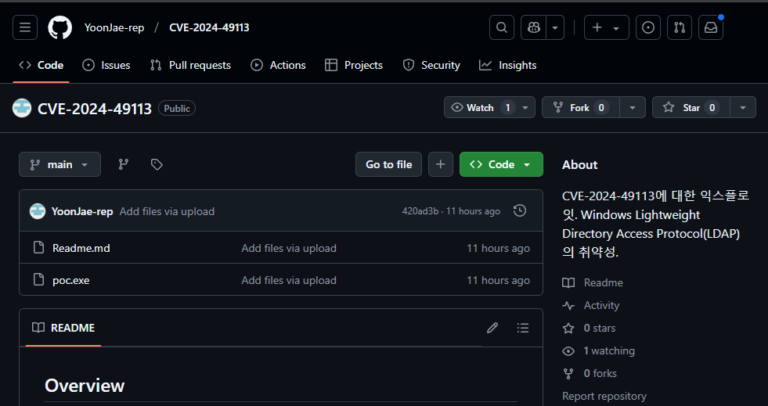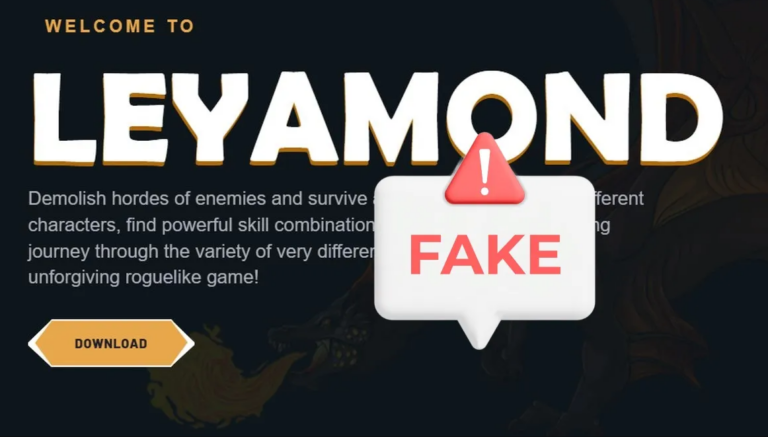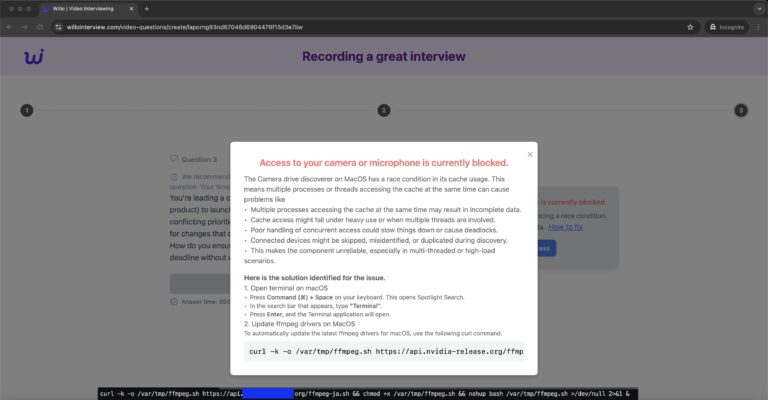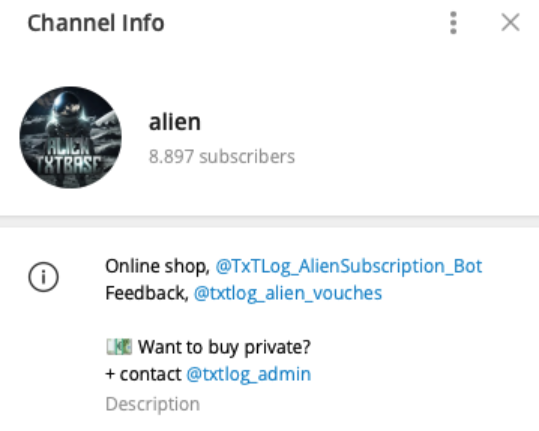
ALIEN TXTBASE Data Leak: A Deep Analysis of the 284M Accounts Breach Added by HaveIbeenPwned
In recent days, the cybersecurity community has been alarmed by the emergence of a massive data leak known as ALIEN TXTBASE, which was recently indexed on Have