
Nikkei Breached: Infostealer Infection Grants Access to 17K+ Employee Slack Chat Histories
Over 17,000 employees and partners now face the fallout from a breach that started with a single infostealer infection on a Japanese computer in August

Over 17,000 employees and partners now face the fallout from a breach that started with a single infostealer infection on a Japanese computer in August

To completely understand what’s going on in a market that has been growing in the last years I found mandatory to know which players are

In a swift operation that underscores Russia’s growing crackdown on domestic cyber threats, the Ministry of Internal Affairs (MВД) has arrested a group of young
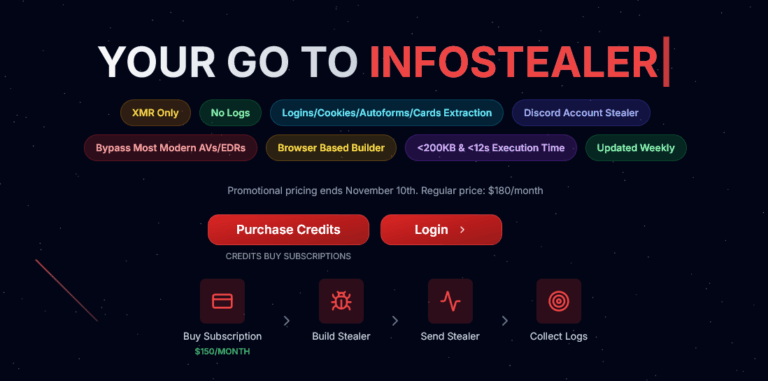
In the ever-evolving landscape of cyber threats, Hudson Rock‘s research team has uncovered a potent new Infostealer builder: Logins(.)zip. Marketed as the “go-to infostealer” on
It is human nature to be competitive, to try your best when competing against others. It is no different when it comes to video games.
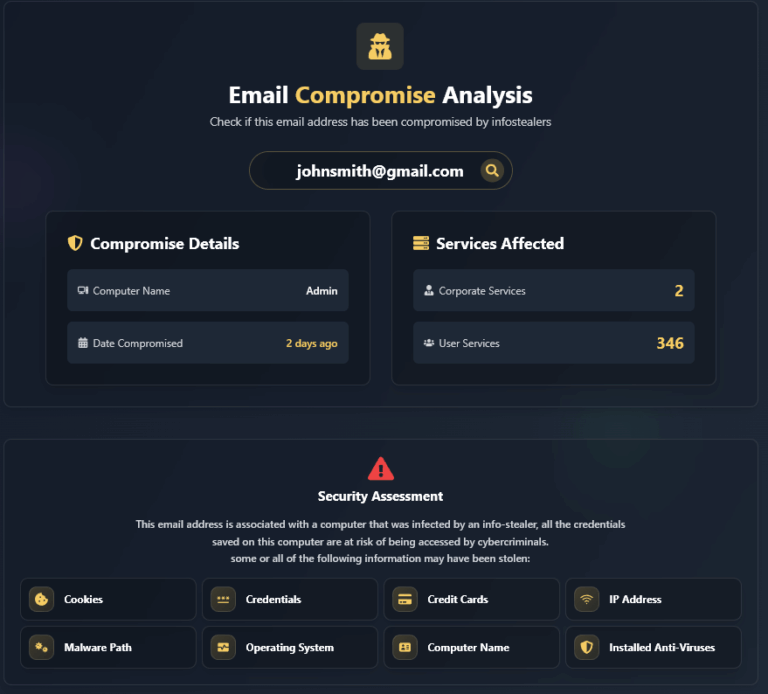
How to Check if an Email Address Has Been Compromised To determine if an email address has been affected by an Infostealer infection and has
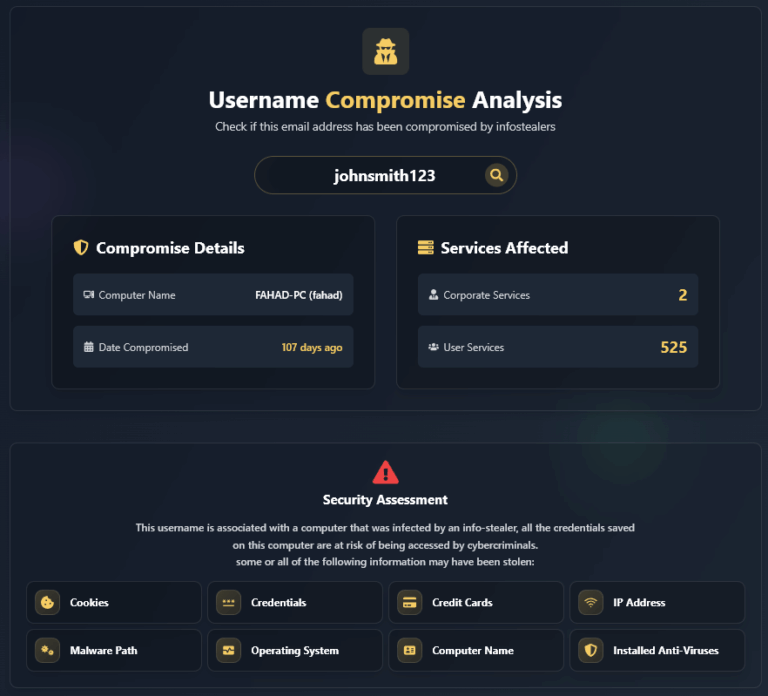
How to Check if a Username Has Been Compromised To determine if a username has been affected by an Infostealer infection and has leaked credentials
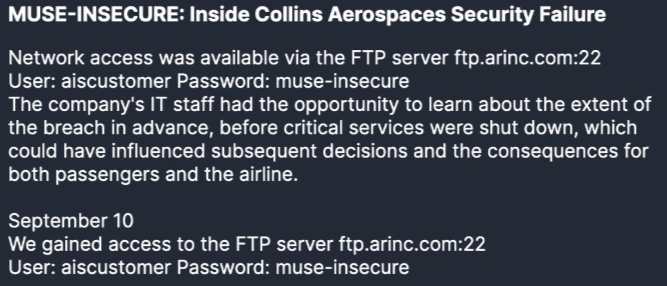
The Incident Breakdown At Hudson Rock, we’ve been closely analyzing the cyber incidents that struck Collins Aerospace, a subsidiary of RTX Corporation, during the week

To completely understand what’s going on in a market that has been growing in the last years I found mandatory to know which players are
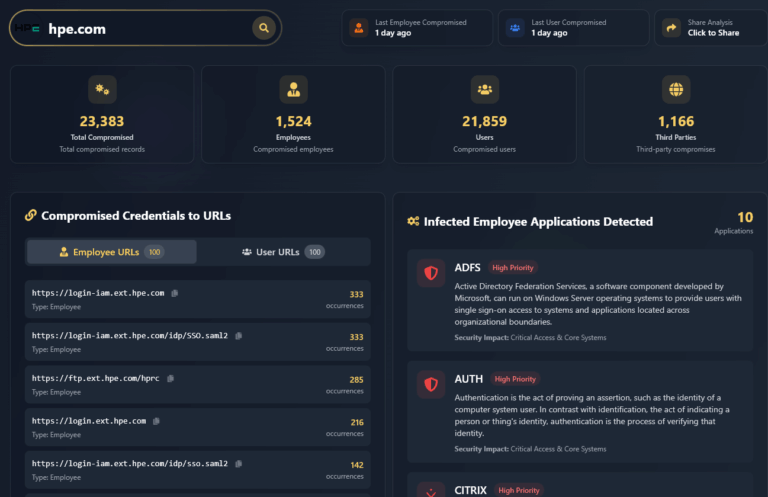
What is an Infostealer? An infostealer is a type of malware designed to stealthily extract sensitive information from infected devices. It operates in the background,
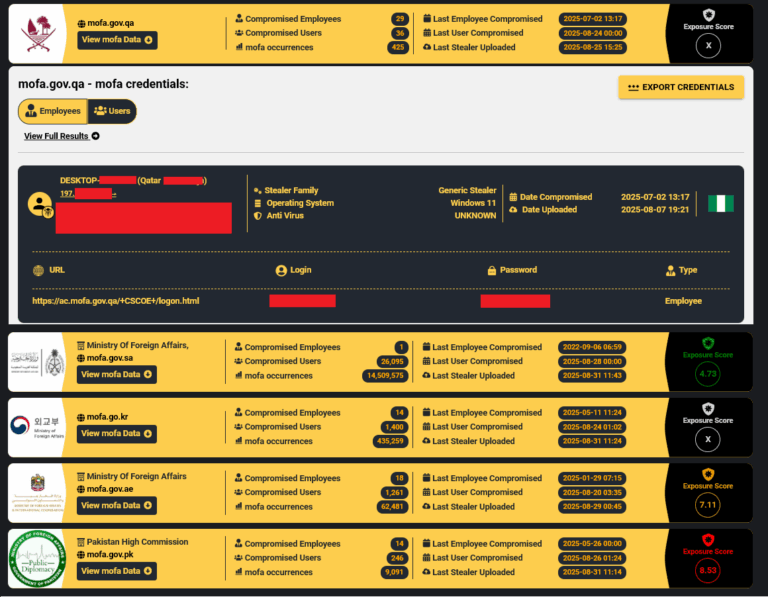
With cyber espionage on the rise, opportunistic Infostealer malware, designed to harvest credentials indiscriminately, is being repurposed by Advanced Persistent Threat (APT) groups to devastating
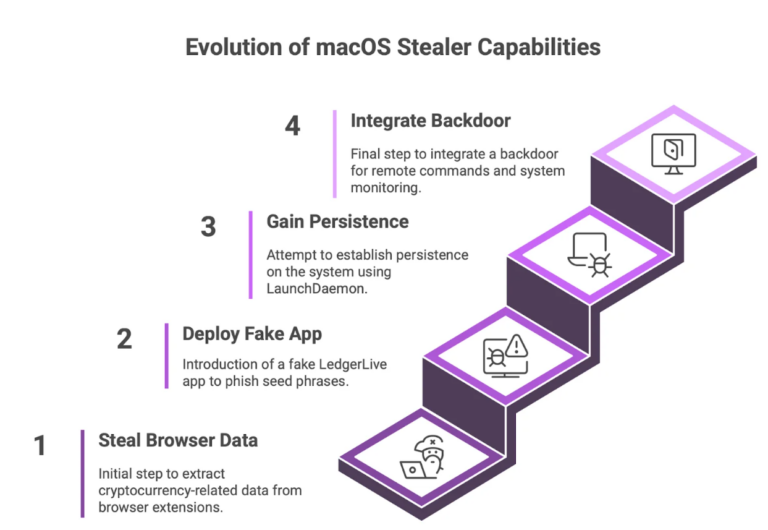
Atomic macOS Stealer (AMOS), a popular piece of stealer malware for macOS, has just received a major update. For the first time, it’s being deployed

At SINCON 2025 in Singapore, Leonid Rozenberg sat down with cyber journalist Jane Lo for a brief but powerful 15-minute interview that catches you up

In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis

The cryptocurrency world has been rocked yet again, this time with the Nobitex exchange finding itself in the crosshairs of a sophisticated cyberattack. Reported earlier
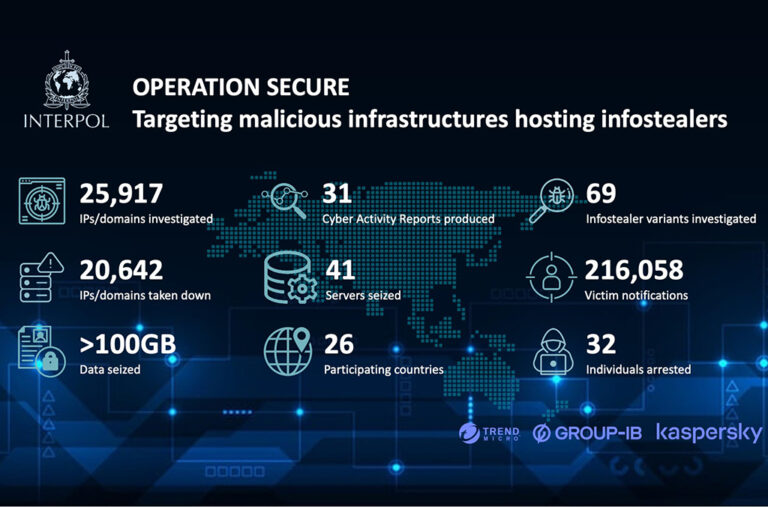
SINGAPORE – More than 20,000 malicious IP addresses or domains linked to information stealers have been taken down in an INTERPOL-coordinated operation against cybercriminal infrastructure.
