
Almost every cyber attack begins at a key ingredient: an Infostealer
Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on
Home » Recorded Future

Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on

2026 Infostealer Trends: From Automated Skills to State-Level Espionage 2026 Infostealer Trends: From Automated Skills to State-Level Espionage As the CTO of Hudson Rock, I’ve
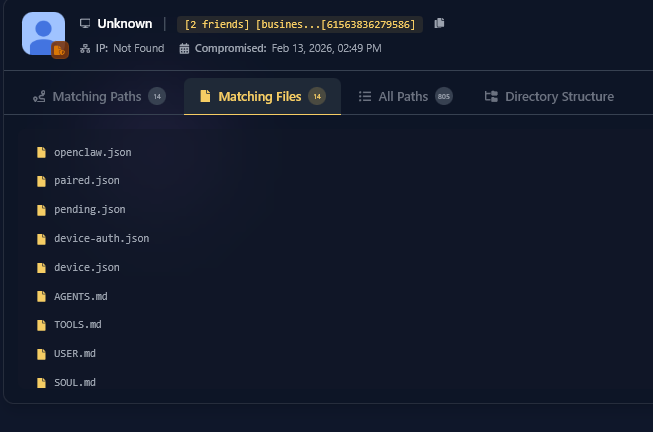
The AI Identity Theft: Real-World Infostealer Infection Targeting OpenClaw Configurations Following our initial research into ClawdBot, Hudson Rock has now detected a live infection where

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
