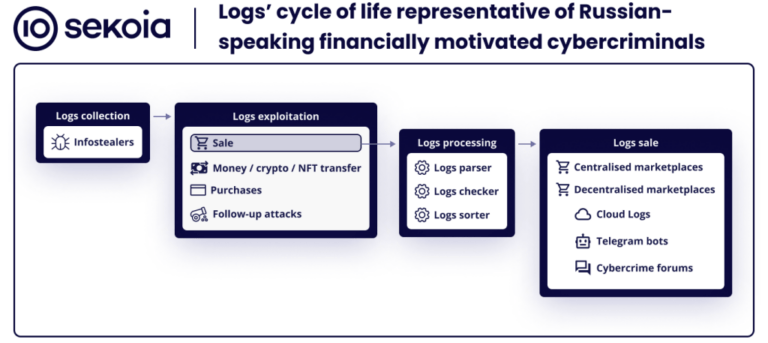
Overview of the Russian-speaking infostealer ecosystem: the logs.
This blog post aims at presenting the life cycle of logs, the cybercrime marketplaces dedicated to logs and the noticeable schemes…
Home » Cybercrime Marketplaces

This blog post aims at presenting the life cycle of logs, the cybercrime marketplaces dedicated to logs and the noticeable schemes…
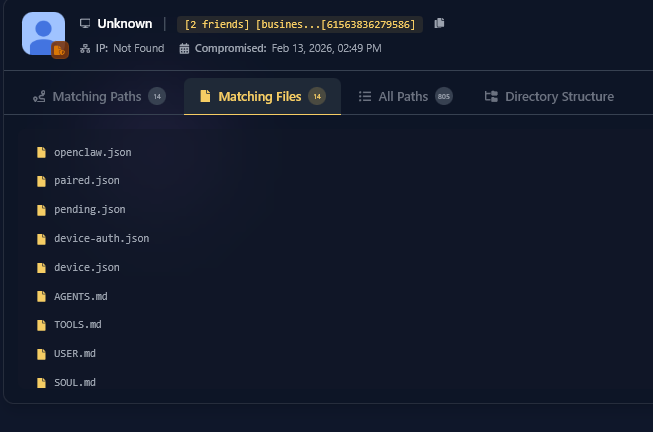
The AI Identity Theft: Real-World Infostealer Infection Targeting OpenClaw Configurations Following our initial research into ClawdBot, Hudson Rock has now detected a live infection where

A compromised machine in Lebanon, belonging to a local ISIS cell commander – contained a very rare collection of explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted.
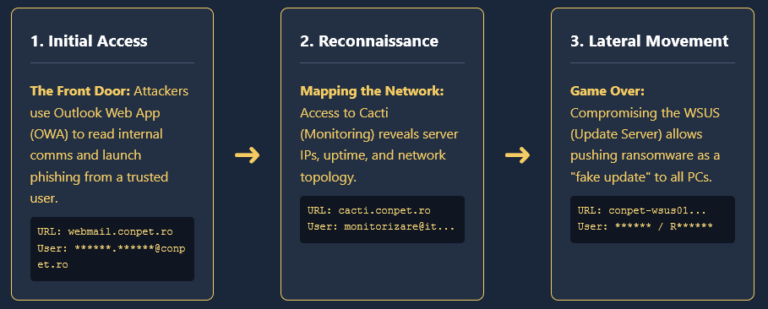
Conpet Hacked: Infostealer Analysis Romania’s Oil Pipeline Operator Hacked: How an Infostealer Infection Paved the Way for Qilin’s Ransomware Attack February 2026 – The Romanian
