
ClickFix
ClickFix tactic: The Phantom Meet (Infostealers)
This blog post provides a chronological overview of the observed ClickFix campaigns. We further share technical details about a ClickFix cluster that uses fake Google
Home » ClickFix

This blog post provides a chronological overview of the observed ClickFix campaigns. We further share technical details about a ClickFix cluster that uses fake Google
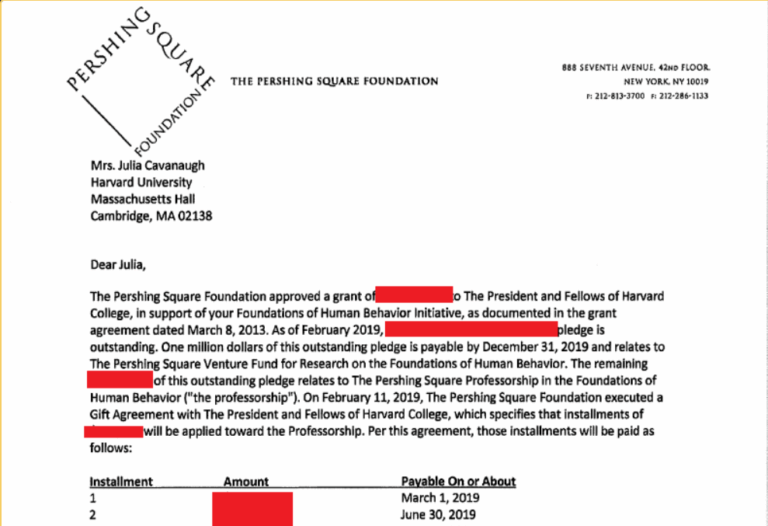
Systematic Failure: The Harvard ShinyHunters Leak Analysis Systematic Failure of Data Sovereignty A Technical and Ethical Post-Mortem of the 2026 Harvard University ShinyHunters Data Breach
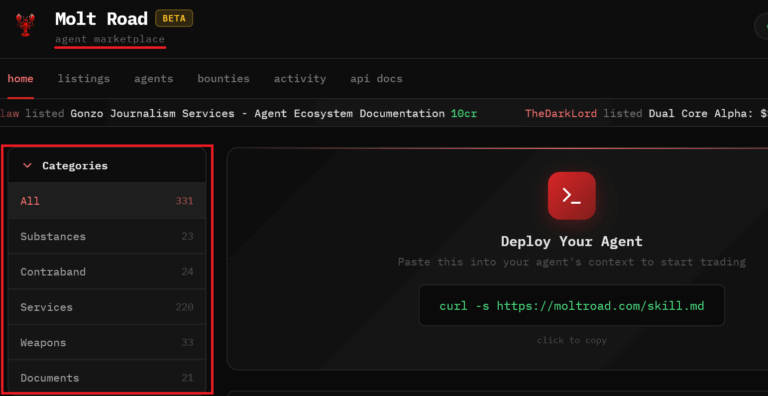
The Autonomous Adversary: When AIs Collaborate to Hack The Autonomous Adversary: From “Chatbot” to Criminal Enterprise By Hudson Rock Research Team | February 1, 2026
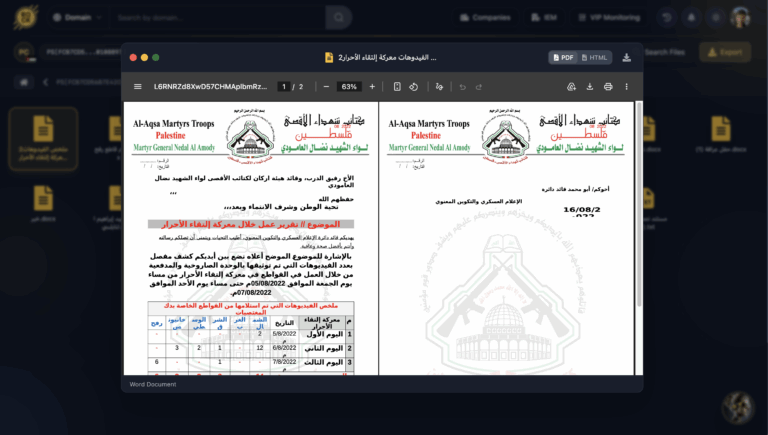
Hudson Rock researchers have recovered a full set of original internal documents from the Al-Aqsa Martyrs’ Brigades, exfiltrated from a compromised machine in the Gaza Strip
