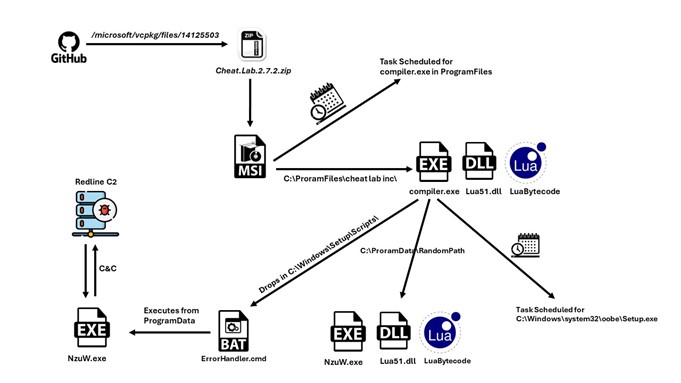
Redline Stealer: A Novel Approach
A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this
Home » C2 Servers

A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this
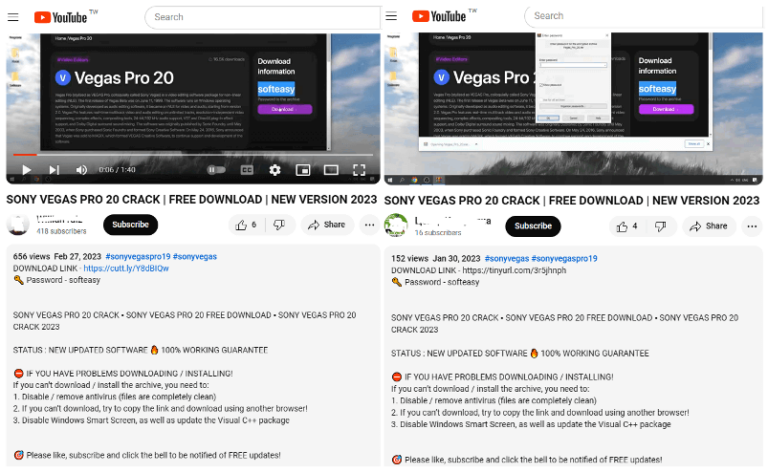
FortiGuard Labs recently discovered a threat group using YouTube channels to distribute a Lumma Stealer variant…

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…

Recordbreaker is also the first User Agent found on Raccoon V2 builds in order to communicate to C2 servers…
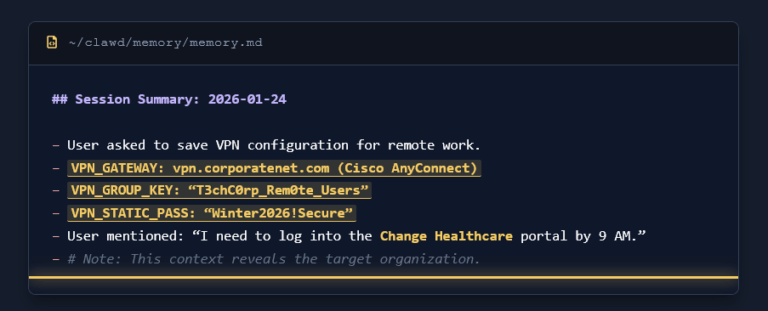
ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of

Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns A recent cybersecurity incident involving
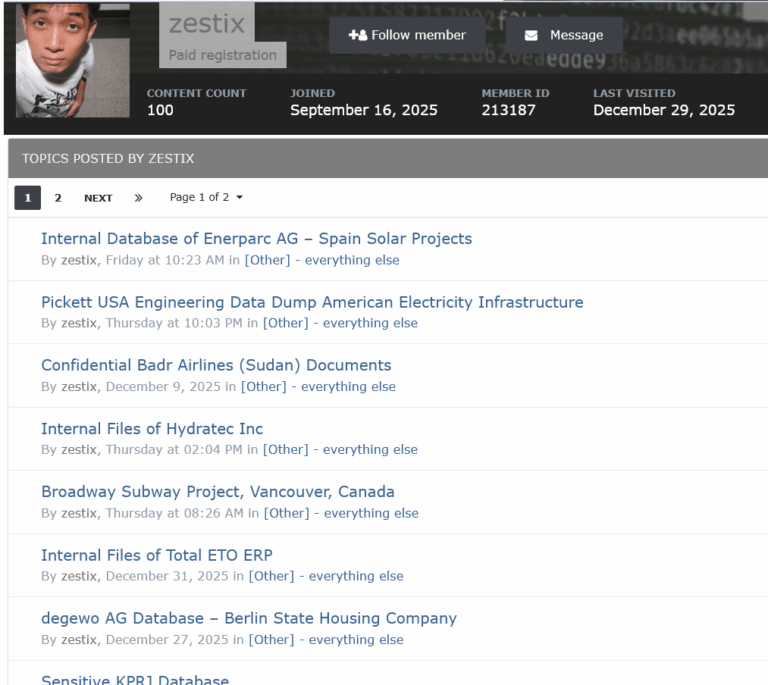
Dozens of Global Companies Hacked via Cloud Credentials from Infostealer Infections & More at Risk Dozens of Global Companies Hacked via Cloud Credentials from Infostealer
