
Key Learnings from Files Present on the C2 Server of an Infamous Infostealer Malware
This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
Home » VirusTotal

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
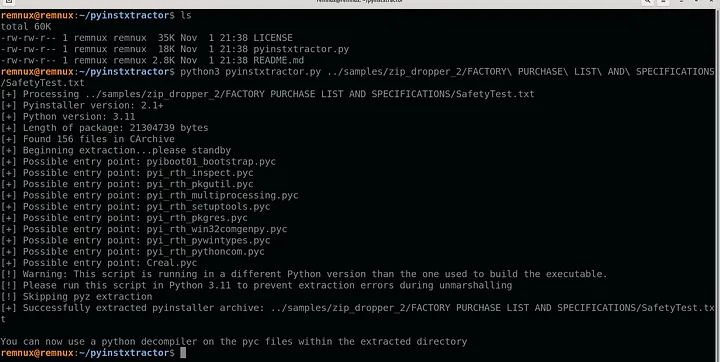
A ZIP/LNK payload and, with some luck, we will end up identifying the infostealer that is being dropped and its source code…
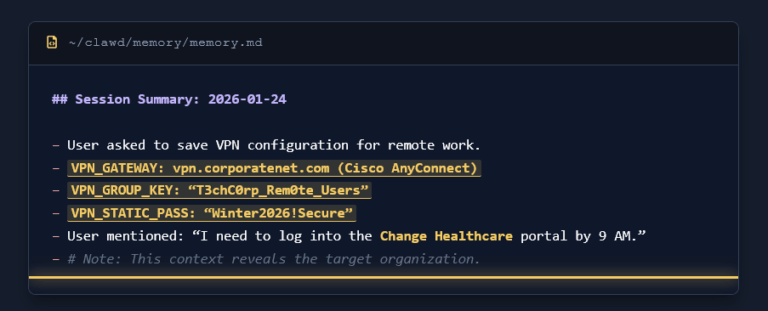
ClawdBot Analysis – Hudson Rock ClawdBot: The New Primary Target for Infostealers in the AI Era January 26, 2026 Hudson Rock Research The rise of

Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns A recent cybersecurity incident involving
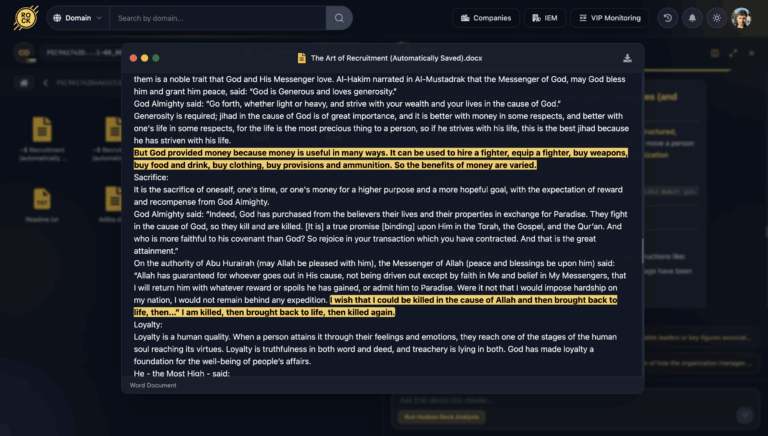
A comprehensive investigation conducted by the Hudson Rock team has identified a sophisticated Jihadist recruitment guide stored on an infostealer-compromised machine.
