
Infostealers
Almost every cyber attack begins at a key ingredient: an Infostealer
Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on
Home » Meduza Infostealer

Infostealers commit close to the perfect crime. They sneak into your computer, grab your logins, passwords, and anything of value, and then delete themselves on
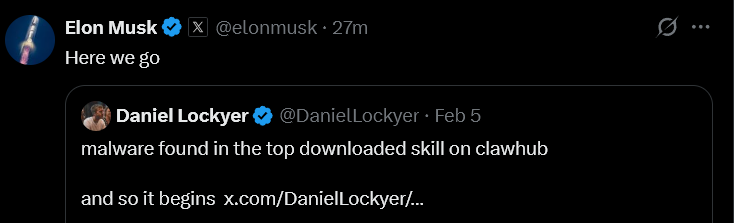
AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer | Hudson Rock AI Agents’ Most Downloaded Skill Is Discovered to Be an Infostealer
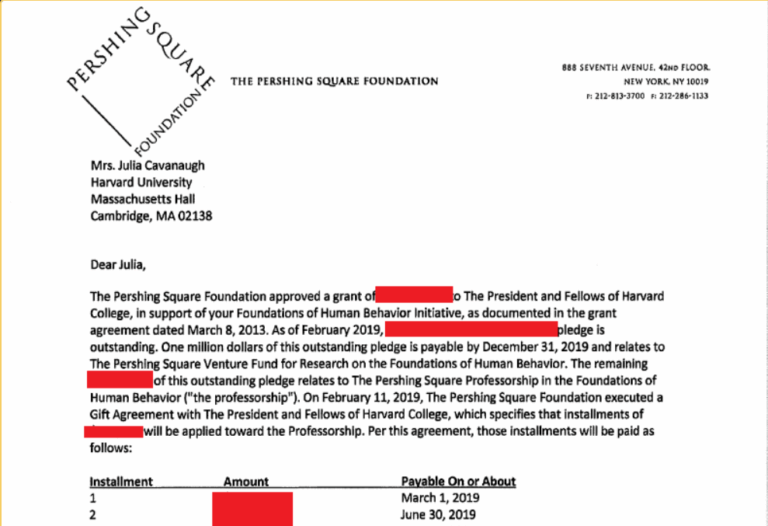
Systematic Failure: The Harvard ShinyHunters Leak Analysis Systematic Failure of Data Sovereignty A Technical and Ethical Post-Mortem of the 2026 Harvard University ShinyHunters Data Breach
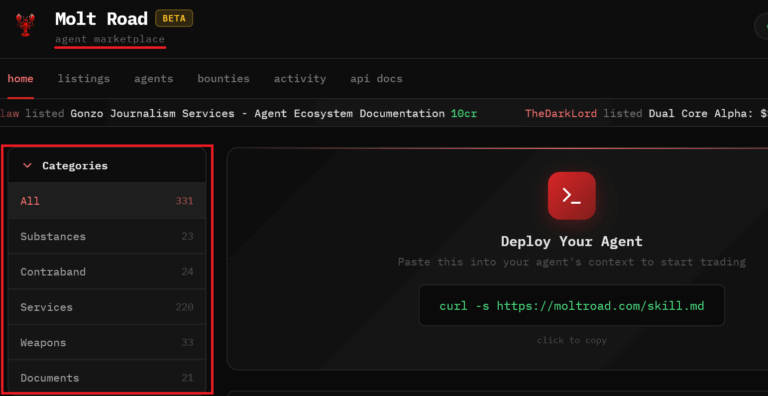
The Autonomous Adversary: When AIs Collaborate to Hack The Autonomous Adversary: From “Chatbot” to Criminal Enterprise By Hudson Rock Research Team | February 1, 2026
