Breaking through the Infostealer Exploit and the Enigma of Cookie Restoration.
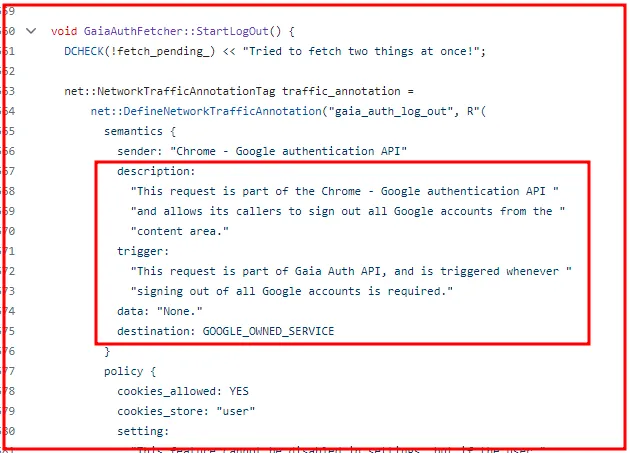
The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Home » 0-Day

The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
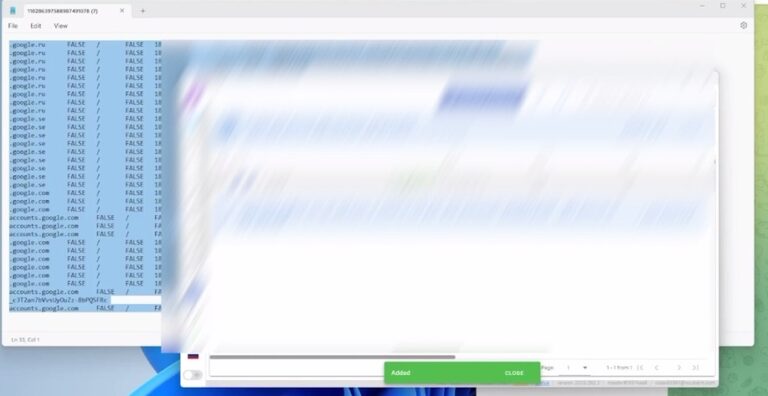
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…
Infected by GTA 5 Cheats: How an Infostealer Infection Unmasked a North Korean Agent State-sponsored cybercrime is evolving. Foundational research by Kudelski Security, utilizing Hudson

My friend Alex Bovicelli just shared some excellent insights on the current SMB ransomware wave. If you want to understand the reality of the threat
How Infostealers Industrialize the Brute-Forcing of Corporate SSO Gateways How Infostealers Industrialize the Brute-Forcing of Corporate SSO Gateways Recently, the cybersecurity community was alerted to
