As Infostealers become increasingly favored by cybercriminals and hacking groups as a primary method for breaching companies, it’s crucial to stay informed about the key players leveraging these tools. In this article, we spotlight the top five hackers who are using Infostealers to infiltrate companies, providing insights into their tactics and the evolving landscape of cyber threats.
- USDoD — USDoD is a highly active and sophisticated threat actor known for targeting high-profile organizations and leaking sensitive information. They are characterized by bold attacks and public disclosures of stolen data.
USDoD’s operations include the breach of Airbus, where they gained access through an employee’s infected computer from a Turkish airline, leveraging stolen credentials to extract and leak confidential business documents. This breach highlights the hacker’s capability to exploit supply chain vulnerabilities and underscores the broader risk of infostealer malware in such attacks

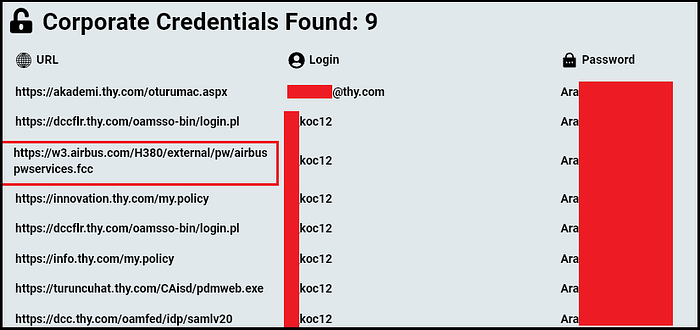
In addition to Airbus, USDoD is also implicated in other significant breaches. They were responsible for the FBI InfraGard breach, exposing personal data of 80,000 individuals, which was subsequently posted on the Breached hacking forum. Their activities demonstrate a pattern of targeting organizations with substantial economic or strategic value, often focusing on sectors such as aerospace and government.
These attacks not only compromise sensitive data but also pose significant threats to national security and corporate integrity.
2. Sp1d3rHunters — also known as Sp1d3r, are cybercriminals involved in data breaches through the exploitation of Snowflake accounts. Their attacks involved the use of stolen credentials, that were obtained due to Snowflake customers getting infected by Infostealers & not maintaining 2FA on their corporate accounts.
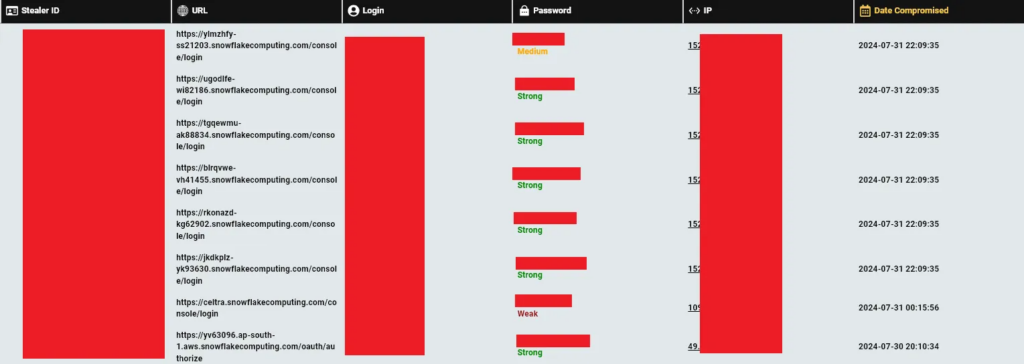
Using these credentials, the hackers were able to access and exfiltrate sensitive data from companies relying on Snowflake’s cloud-based data warehousing services.
One notable instance includes the massive breach at Ticketmaster, where Sp1d3rHunters accessed and leaked thousands of event tickets, escalating their extortion demands significantly.

Another high-profile incident involved AT&T, where Sp1d3rHunters used similar tactics to infiltrate the company’s Snowflake instance and compromise vast amounts of customer data.
The group’s operations extend to other significant breaches, including those at Advance Auto Parts, Bausch, Neiman Marcus, and many other companies, leading to the exposure of millions of personal records.

These attacks were ultimately highly preventable as the threat actor used credentials that were identified years prior to the breaches, highlighting the importance of proper Infostealer credentials monitoring.
3. IntelBroker —A notorious threat actor known for orchestrating high-profile cyberattacks against both government and private sector entities.
They have been linked to several significant breaches, including those involving Apple, Zscaler, and Microsoft, and have sold access to compromised systems and data on underground forums such as BreachForums.

IntelBroker’s activities have also targeted major corporations and critical infrastructure, with breaches involving Europol, the U.S. Department of Transportation, the Pentagon, General Electric, Home Depot, and Acuity, among others. Their pattern of targeting high-value entities underscores their capabilities and the potential national security implications of their actions.
Recently, competing threat actors shed light on the methodology of IntelBroker’s hacks, explaining the initial attack vector used by the hacker revolves around the use of Infostealer credentials:

It is evident that threat actors opt to use Infostealer credentials as a way to infiltrate companies due to the ease in finding “low hanging fruits” such as companies with employees that were infected and possess credentials to the VPN network of the company or their company’s mail server.
4. Andariel (North Korea) — The Andariel group, a North Korean Advanced Persistent Threat (APT) actor, is known for its cyber operations targeting various sectors including military, nuclear, and manufacturing.
This group, often linked to the larger Lazarus Group, utilizes a variety of sophisticated tools and techniques to infiltrate networks and steal sensitive data. They have been observed using keyloggers, infostealers, and remote access tools (RATs) such as TigerRAT and Nestdoor.
In July 2024, the U.S. Justice Department charged individuals from the group for their involvement in ransomware attacks targeting U.S. hospitals and health care providers —

Andariel’s use of infostealers is a key component of their strategy to gather intelligence and financial data. These malware variants are designed to capture keystrokes, clipboard data, and other sensitive information, which is then used for further exploitation or sold in underground markets.
Notably, Andariel has been involved in several high-profile attacks using infostealers, where they have infiltrated networks through phishing campaigns and malicious email attachments. The group’s consistent use of these tools highlights their capability to adapt and evolve their techniques to maintain persistent access to targeted systems.

5. Lapsus$ — A notorious hacking group known for its high-profile attacks and aggressive tactics, including the use of infostealers.
Emerging in early 2021, Lapsus$ quickly gained notoriety for targeting major corporations and organizations such as NVIDIA, Samsung, and Vodafone. The group’s modus operandi involves deploying infostealers to harvest sensitive data such as login credentials, personal information, and proprietary business data. This stolen information is then used to facilitate further intrusions, often leading to ransomware deployment or data exfiltration.
Their infostealers are typically sophisticated, designed to bypass traditional security measures and extract valuable information efficiently.
One notable example of Lapsus$’ use of infostealers is the high-profile attack on Electronic Arts (EA) in 2021. In this incident, Lapsus$ managed to breach EA’s network, stealing a significant amount of data, including source code for popular games like FIFA and other proprietary tools. The attackers used infostealers to gain access to EA’s systems and exfiltrate sensitive information, which they then threatened to release unless a ransom was paid.

This attack demonstrated Lapsus$’ capability to exploit infostealers for major data theft and leverage the stolen data for extortion, highlighting their disruptive impact on targeted organizations.
Conclusion
In the face of increasingly sophisticated cyber threats, including those driven by prominent hackers using Infostealers, it’s crucial for organizations to prioritize effective monitoring solutions. The tactics of groups like USDoD, Sp1d3rHunters, IntelBroker, Andariel, and Lapsus$ underscore the need for vigilance in tracking compromised credentials and malicious activities. Companies like Hudson Rock play a critical role in this defense by providing real-time intelligence and insights into threat actor behaviors, helping organizations stay ahead of potential breaches.
By leveraging such advanced monitoring solutions, businesses can better protect their data, strengthen their security posture, and mitigate the risks posed by these evolving cyber threats.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock