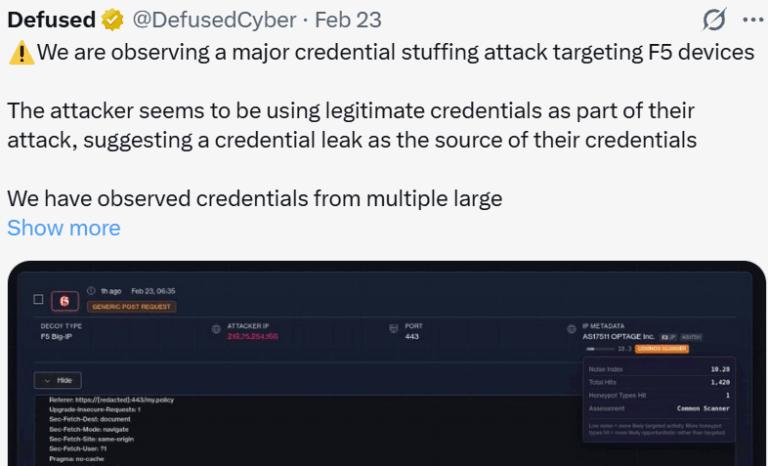
In a cybersecurity catastrophe that’s rocked Paraguay to its core, a staggering 7.4 million citizen records, nearly the entire population’s personally identifiable information (PII), have been leaked on the dark web. Evidence for the initial access which enabled this hack point to an Infostealer infection that compromised a government employee’s credentials, granting cybercriminals access to sensitive systems.
This breach, orchestrated by the threat actor group Brigada Cyber PMC, marks one of the most audacious cyberattacks in Paraguay’s history. Our analysis, powered by Hudson Rock’s threat intelligence database, ties this massive data dump to an Infostealer infection we detected on the compromised domain rve.mspbs.gov.py. Here’s how it went down.
Brigada Cyber PMC’s Dark Web Extortion Scheme
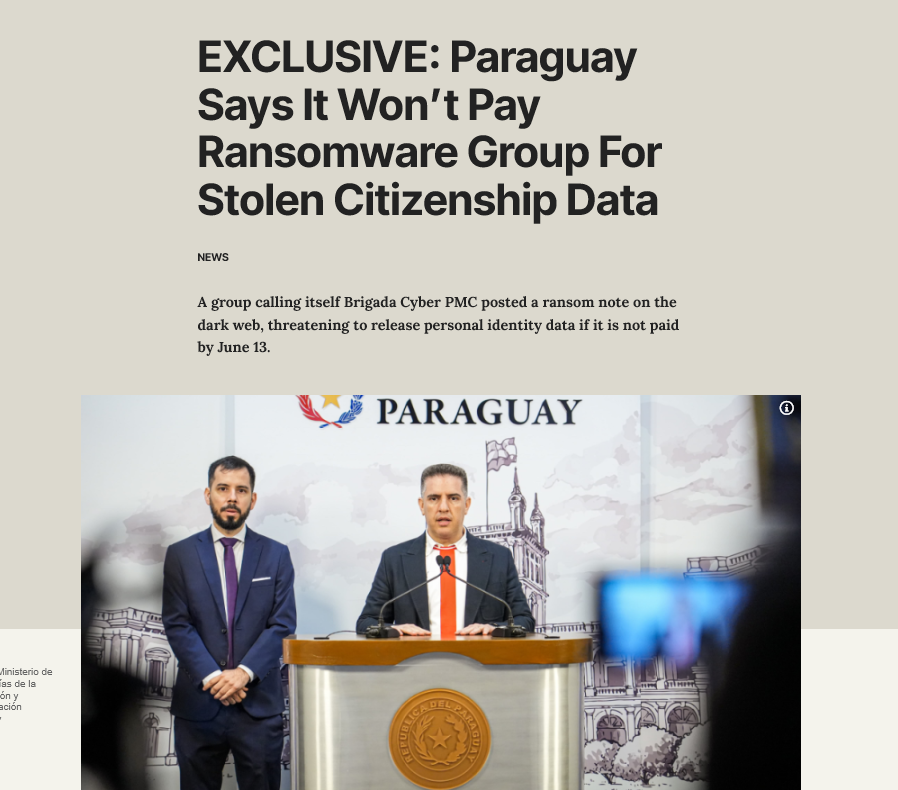
On June 12, 2025, Resecurity, a leading cybersecurity firm, reported that Brigada Cyber PMC posted a ransom note on a dark web forum, demanding $7.4 million, $1 per Paraguayan citizen, to withhold the release of 7.4 million stolen records. The group gave Paraguay’s government until June 13 to comply, even including a countdown timer to ramp up the pressure.
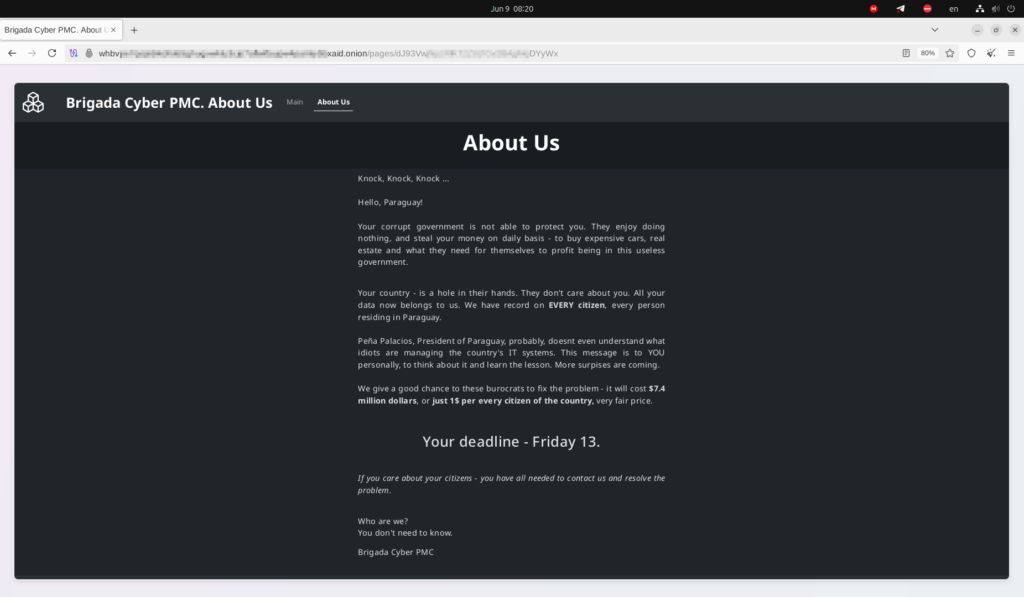
When the government refused to pay, the hackers made good on their threat, dumping the data for all to access via torrent files, a tactic reminiscent of notorious ransomware gangs like LockBit 3.0.
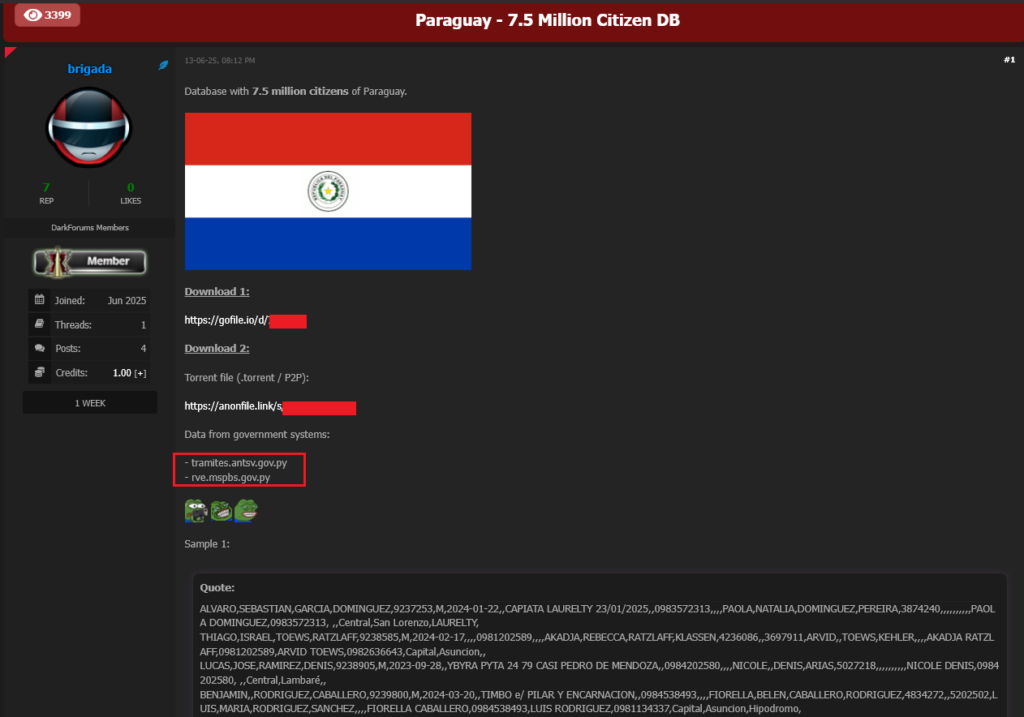
The leaked data is a goldmine for cybercriminals, containing sensitive PII such as names, ID card numbers, dates of birth, nationalities, professions, and marital statuses. Resecurity’s investigation revealed that the data was likely exfiltrated from at least three government systems, with samples pointing to agencies like the Superior Tribunal of Electoral Justice (TSJE). The scale is unprecedented – Paraguay’s population is roughly 6.8-7 million, meaning this breach impacts virtually every citizen, including duplicates, deceased individuals, and migrants.
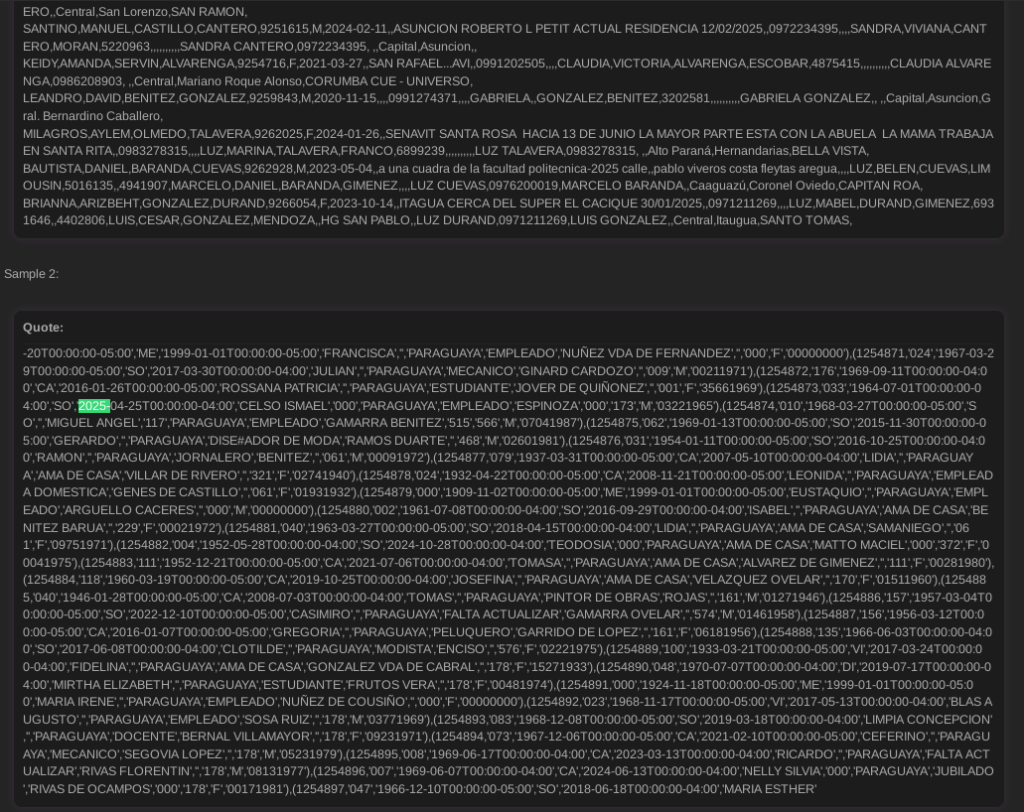
Infostealers: The Silent Culprit Behind the Breach
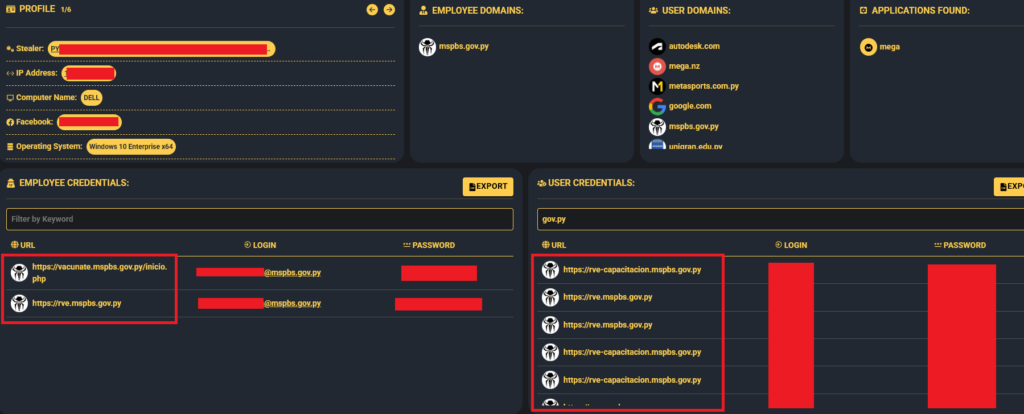
Hudson Rock researchers dug deeper into the root cause of this breach using it’s own Cavalier Infostealer intelligence platform, which tracks Infostealer infections worldwide. Our findings pinpoint an Infostealer infection on a government employee’s device with corporate access to the domain rve.mspbs.gov.py, a system tied to Paraguay’s Ministry of Public Health and Social Welfare. This infected employee’s credentials were harvested by Redline Infotealer all the way back in April 2023. Armed with these stolen credentials, Brigada Cyber PMC gained unauthorized access to critical systems, enabling them to siphon off the massive dataset.
The evidence for the breach likely originating from an Infostealer infection is further supported by Resecurity’s cyber threat intelligence team
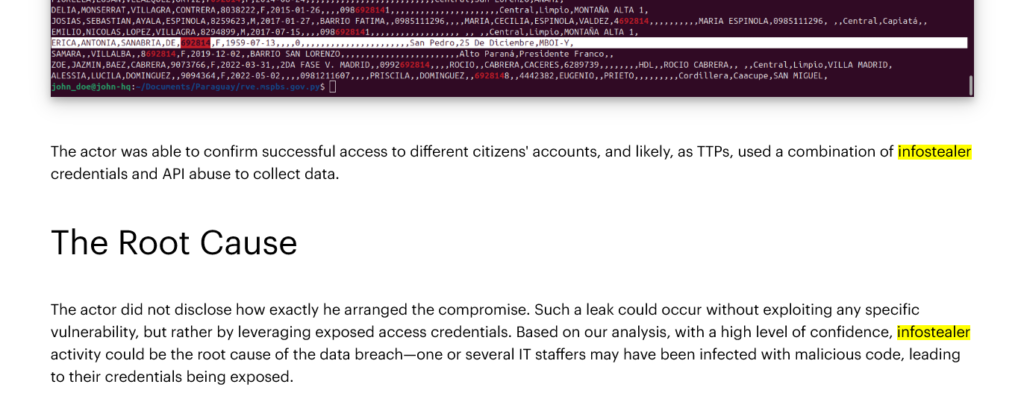
Infostealers are stealthy, often spreading through phishing emails, malicious downloads, or compromised websites. They quietly collect login credentials, cookies, and other sensitive data from infected devices, which are then sold or exploited on the dark web. In this case, the compromised credentials provided a backdoor to Paraguay’s government infrastructure, highlighting the devastating potential of infostealers when they infiltrate high-privilege accounts.
A National Crisis with Global Implications
The fallout from this breach is bad. With 7.4 million records now circulating on the dark web, Paraguayan citizens face unprecedented risks of identity theft, financial fraud, and targeted phishing campaigns. The torrent-based distribution method ensures the data spreads rapidly, as anyone downloading the files becomes a peer distributor, amplifying the damage.
Resecurity notes that this incident could be “one of the most significant cybersecurity incidents in the nation’s history,” and we agree – this is a wake-up call for governments worldwide.
Paraguay’s refusal to pay the ransom, while principled, has left its citizens vulnerable. Cybersecurity expert Luis Benítez told OCCRP, “We are completely and utterly defenseless,” emphasizing the government’s struggle to manage the crisis. The leaked data can now be cross-referenced with social media and other databases, enabling cybercriminals to build detailed profiles for scams, extortion, or even nation-state espionage.
Infostealers: The Growing Threat to National Security
This breach underscores a chilling reality: Infostealers are no longer just a tool for petty cybercriminals – they’re a weapon for large-scale, nation-level attacks. Brigada Cyber PMC’s motives remain murky, with Resecurity suggesting possible ties to foreign state actors masking espionage as cybercrime. Regardless of the intent, the method is clear: Infostealers provided the key to unlock Paraguay’s most sensitive data.
Our data from Hudson Rock shows a surge in Infostealer infections targeting government and healthcare sectors across Latin America, with Paraguay being a prime target due to its rapid digitization and geopolitical significance. The infection on rve.mspbs.gov.py is just one of many, but its impact is unparalleled. Governments must prioritize Infostealer monitoring, endpoint security, multi-factor authentication, and employee training to combat this growing threat.
Credit Where Credit’s Due
This article draws heavily from Resecurity’s groundbreaking research, published on June 13, 2025, which first exposed Brigada Cyber PMC’s ransom note and the scale of the breach. Their detailed analysis of the dark web activity and data samples was instrumental in understanding the incident. For the full report, check out their blog: Paraguay is Being Targeted by Cybercriminals – 7.4 Million Citizen Records for Sale.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock