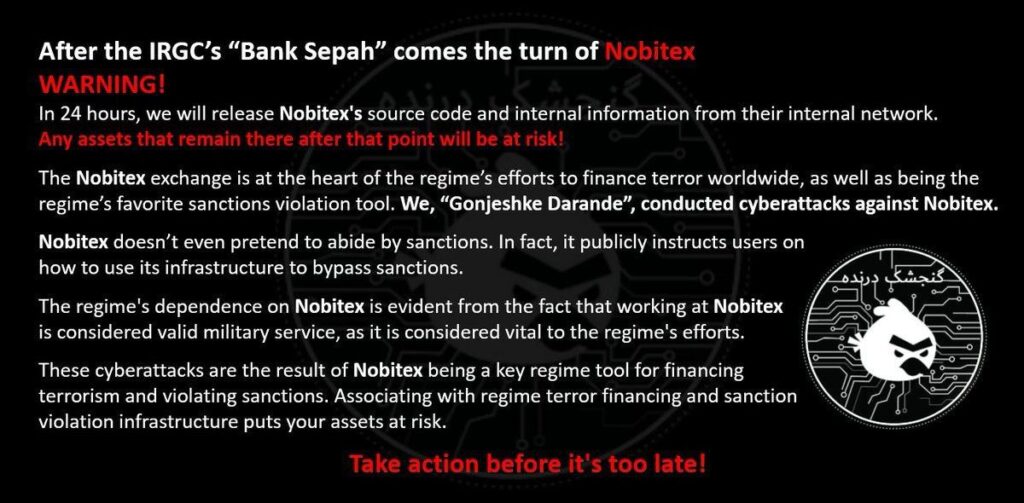
The cryptocurrency world has been rocked yet again, this time with the Nobitex exchange finding itself in the crosshairs of a sophisticated cyberattack. Reported earlier today, the Iranian crypto platform suffered a massive $81.7 million loss due to a hack claimed by the group “Gonjeshke Darande”, allegedly linked to Israel, which claims affiliation with Israel and accuses Nobitex of aiding Iran’s regime in terrorism financing and sanctions evasion. The exchange confirmed the breach affected only its hot wallets, prompting an immediate suspension of operations and a promise to compensate users, though cold storage assets remain secure.
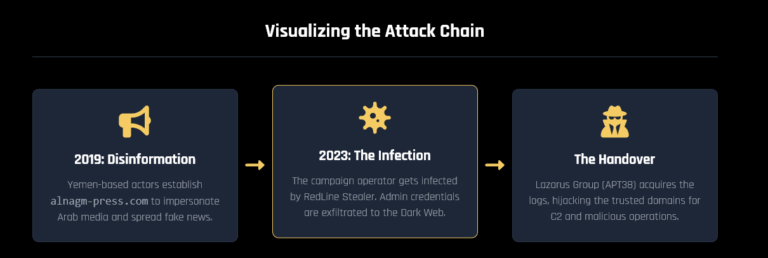
But beneath the surface of this high profile breach lies an overlooked detail: two critical Nobitex employees were compromised by infostealers, granting attackers a potential foothold into the exchange’s internal systems.
Hudson Rock researchers uncovered these infections, shedding light on how Infostealer malware may have paved the way for this hack.
The Infostealer Connection
Hudson Rock researchers’ analysis, based on logs extracted from over 30,000,000 infected machines worldwide, reveals that two Nobitex employees both with significant server access fell victim to Infostealer campaigns. This malicious malware, designed to siphon sensitive data like credentials, browsing history, and cookies, have become a go-to weapon for cybercriminals. The logs show a treasure trove of compromised data relating to Nobitex, including:
- Webmail credentials for Nobitex’s email server (bitex-mail.nobitex.net/owa/)
- Administrative credentials to Nobitex’s internal systems (admin.nxbo.ir)
- Testnet corporate credentials (testnet.nobitex.ir)
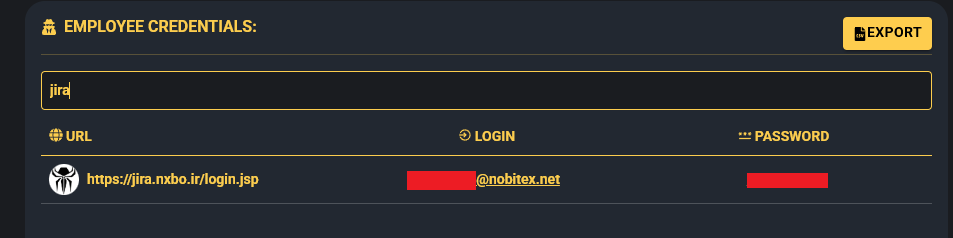
- JIRA corporate credentials for Nobitex (jira.nxbo.ir/login.jsp)
- Various cookies for internal Nobitex systems
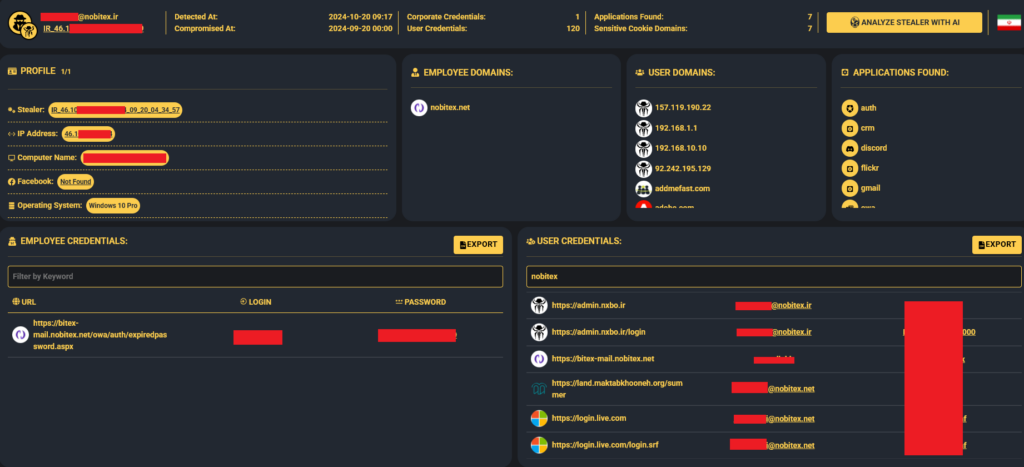
Infected employee #1 –
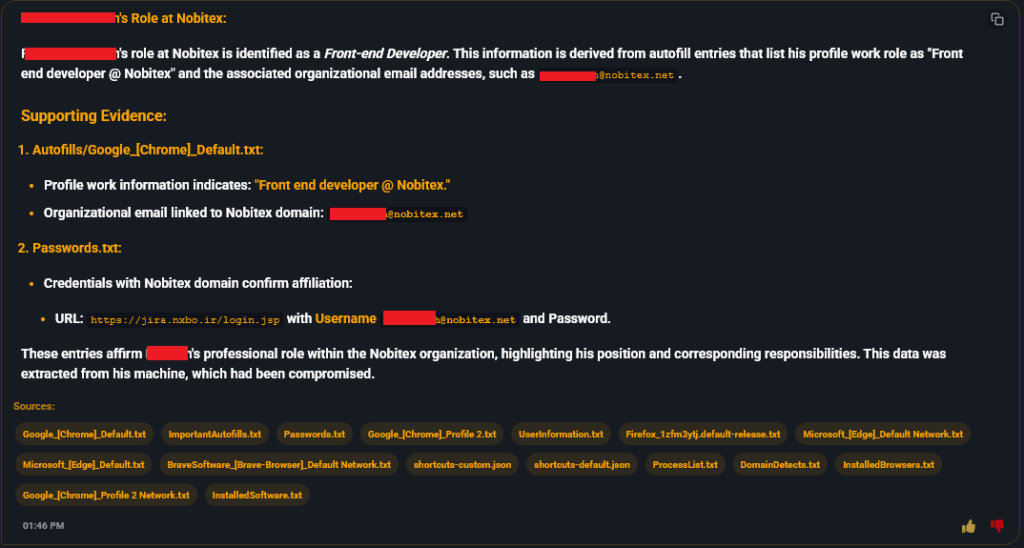
On September 20, 2024, an Iranian computer was infected by a StealC Infostealer. Based on exfiltrated data, the computer appears to belong to a developer in the company, and corporate credentials from the machine demonstrate sensitive access to the company’s infrastructure:
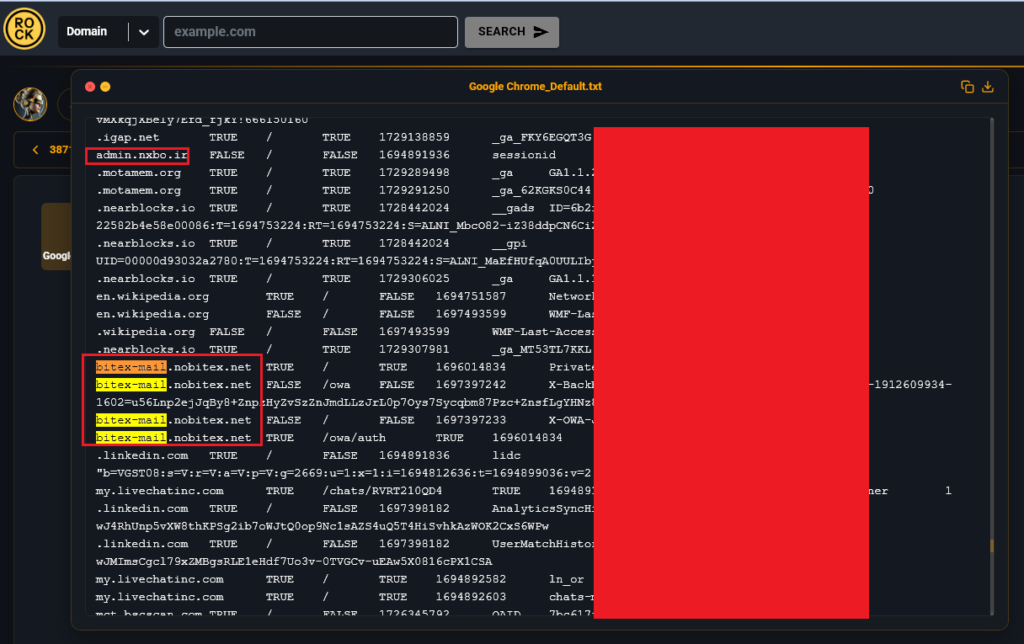
Additionally, cookies for various Nobitex systems were identified on the infected machine:
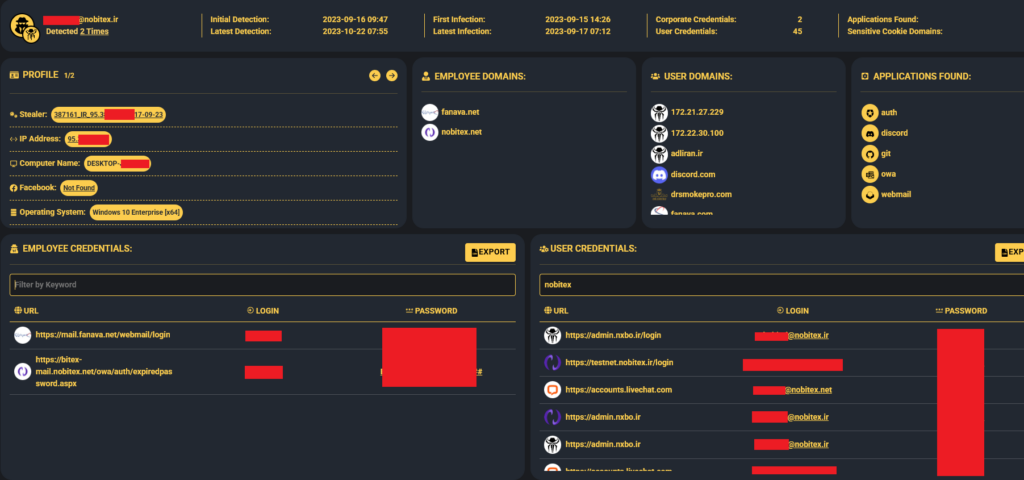
Infected employee #2 –
On September 15, 2023, an Iranian computer was infected by a Redline Infostealer, based on exfiltrated data, the computer appears to belong to a Nobitex employee with corporate credentials relating to the company’s internal network.
Notably, Jira credentials for the company’s servers may have aided hackers in the intrusion, Hudson Rock researchers have previously highlighted the use of Jira credentials from Infostealer infections to carry out hacks against Jaguar Land Rover, Telefonica, Schneider Electric, and other companies
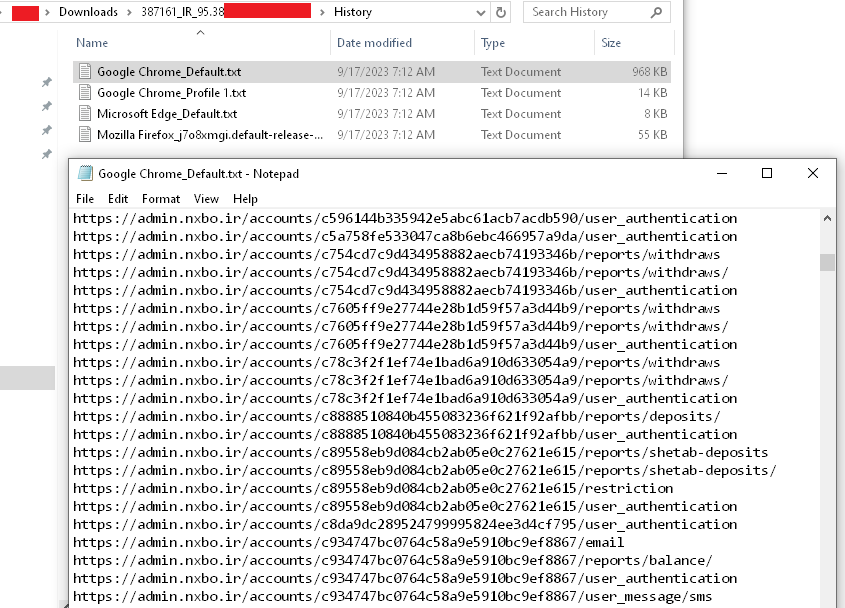
The browsing history of the infected employee demonstrates intensive involvement in the company’s operations
What This Means for Crypto Exchanges
The Nobitex hack is a stark reminder: infostealers are the silent precursors to headline grabbing attacks. With over $2.1 billion lost to crypto hacks in 2025 alone, exchanges can’t afford to ignore the threat lurking in employee endpoints. Nobitex has suspended operations and promised compensation, but the damage is done. The release of source code threatened by the hackers could expose even more vulnerabilities if not contained.
For the crypto community, this is a wake up call. Two compromised employees, armed with admin access, turned a targeted strike into a financial catastrophe. Hudson Rock researchers’ work highlights the need for robust endpoint security, regular credential audits, and employee training to spot phishing attempts the likely entry point for these infostealers.
Conclusion
Infostealers are a real and growing threat, enabling hackers to execute significant breaches across major organizations. By exploiting weak points like webmail and VPNs, they gain access to sensitive data and systems, as seen in recent attacks on major companies.
To combat this, organizations must strengthen their cybersecurity measures, such as implementing multi-factor authentication and educating employees about safe practices. Utilizing Hudson Rock’s threat intelligence can provide invaluable insights into compromised credentials and real-time notifications, helping companies proactively address vulnerabilities before they lead to breaches.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock