On December 20th, a hacker who goes by the username “irleaks” posted a thread in which they attempt to sell over 160,000,000 records of Iranians from 23 of Iran’s leading insurance companies.
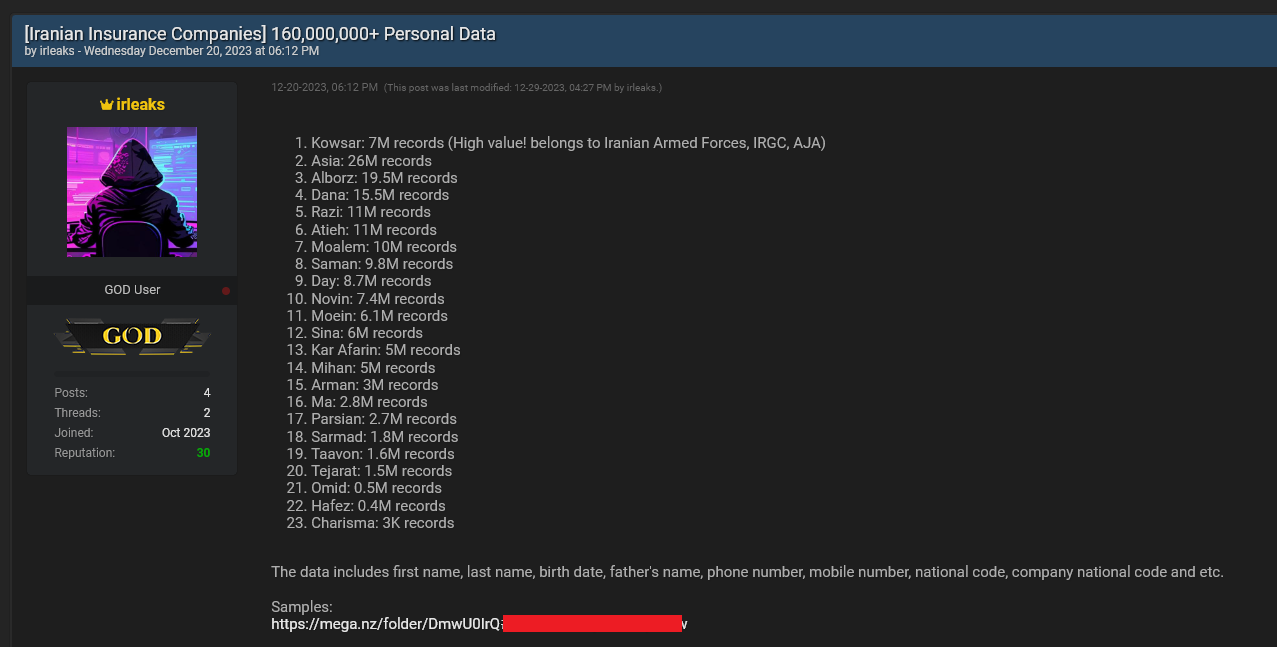
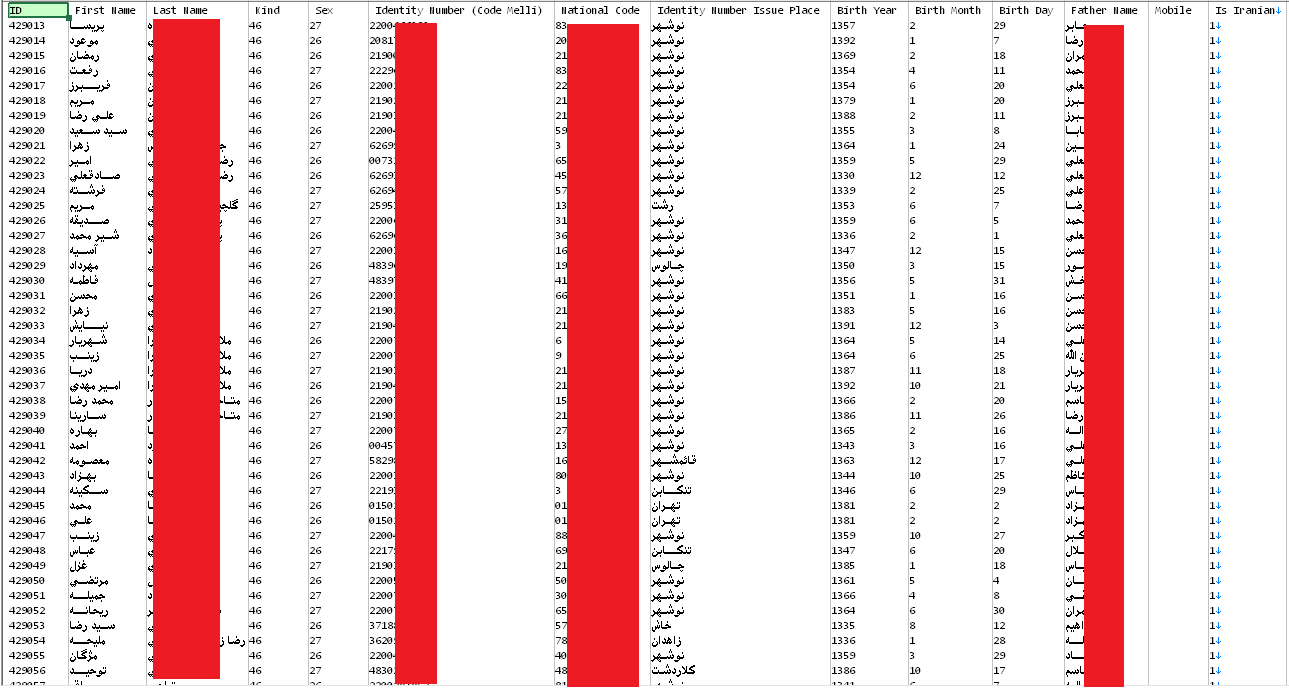
The data includes fields such as names, phones, identity numbers, addresses, passport numbers, and other sensitive details.
Hudson Rock researchers confirm that the data appears to be genuine and note that pulling off an attack against this many insurance companies is wildly difficult.
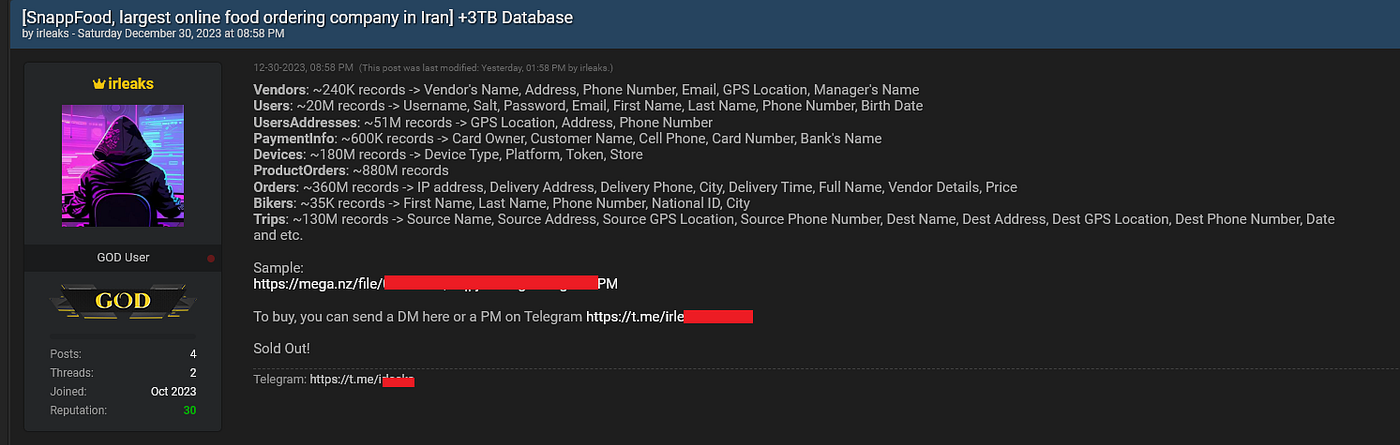
But this breach wasn’t enough for “irleaks”, and on December 30th the threat actor posted another thread in which they claim to have hacked Iran’s largest online food ordering company, SnappFood.
The data that was apparently exfiltrated from the company amounts to a staggering 3 Terabytes, and includes incredibly sensitive details such as
- 20,000,000 users data (emails, passwords, phone numbers)
- 51,000,000 user addresses
- 600,000 credit cards data
- 180,000,000 device related information
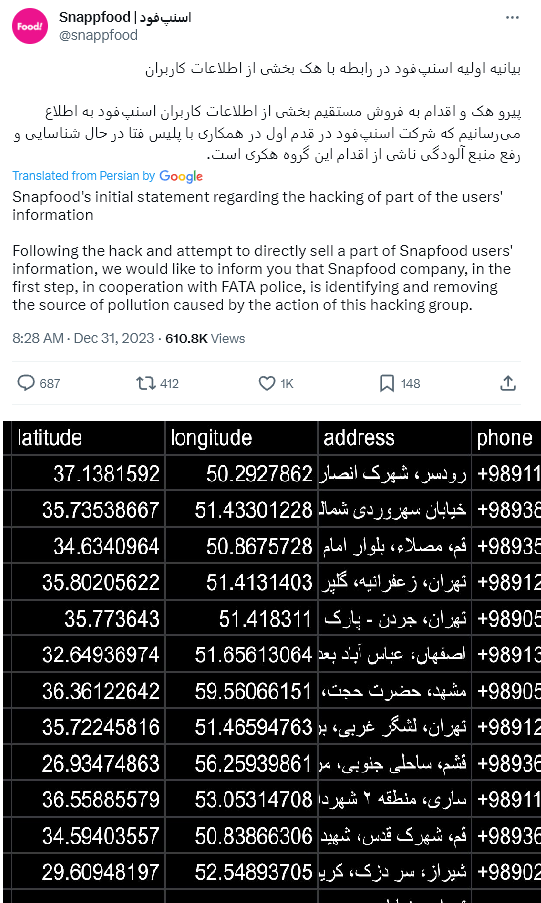
SnappFood has taken notice to the breach and promptly issued a statement claiming they are investigating the attack.
It is worth noting that although the origin of the breach is unknown, Hudson Rock researchers identified a recently compromised employee of SnappFood who had their computer infected with a StealC infostealer.
The infection of this employee’s computer resulted in many sensitive credentials of the organization being accessible to some hackers and may have been used as an initial attack vector against the company.
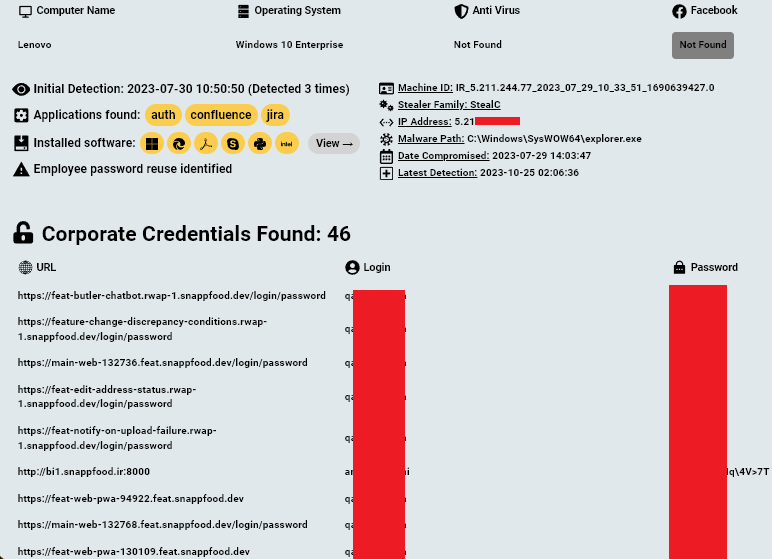
Some of the data includes login details to the company’s Confluence server, Jira server, and other development related URLs.

The combination of sophisticated attacks launched by a single threat actor against industry leading companies in Iran raises the question if this was a state-sponsored attack.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock