Executive Summary
A comprehensive investigation conducted by the Hudson Rock team has identified a sophisticated Jihadist recruitment guide stored on an infostealer-compromised machine. Utilizing Hudson Rock Cavalier intelligence platform and Enki AI, the compromised machine revealed a step-by-step manual outlining how to identify, radicalize, and recruit individuals into jihadist cells.
The Discovery: Identifying the Recruitment Guide
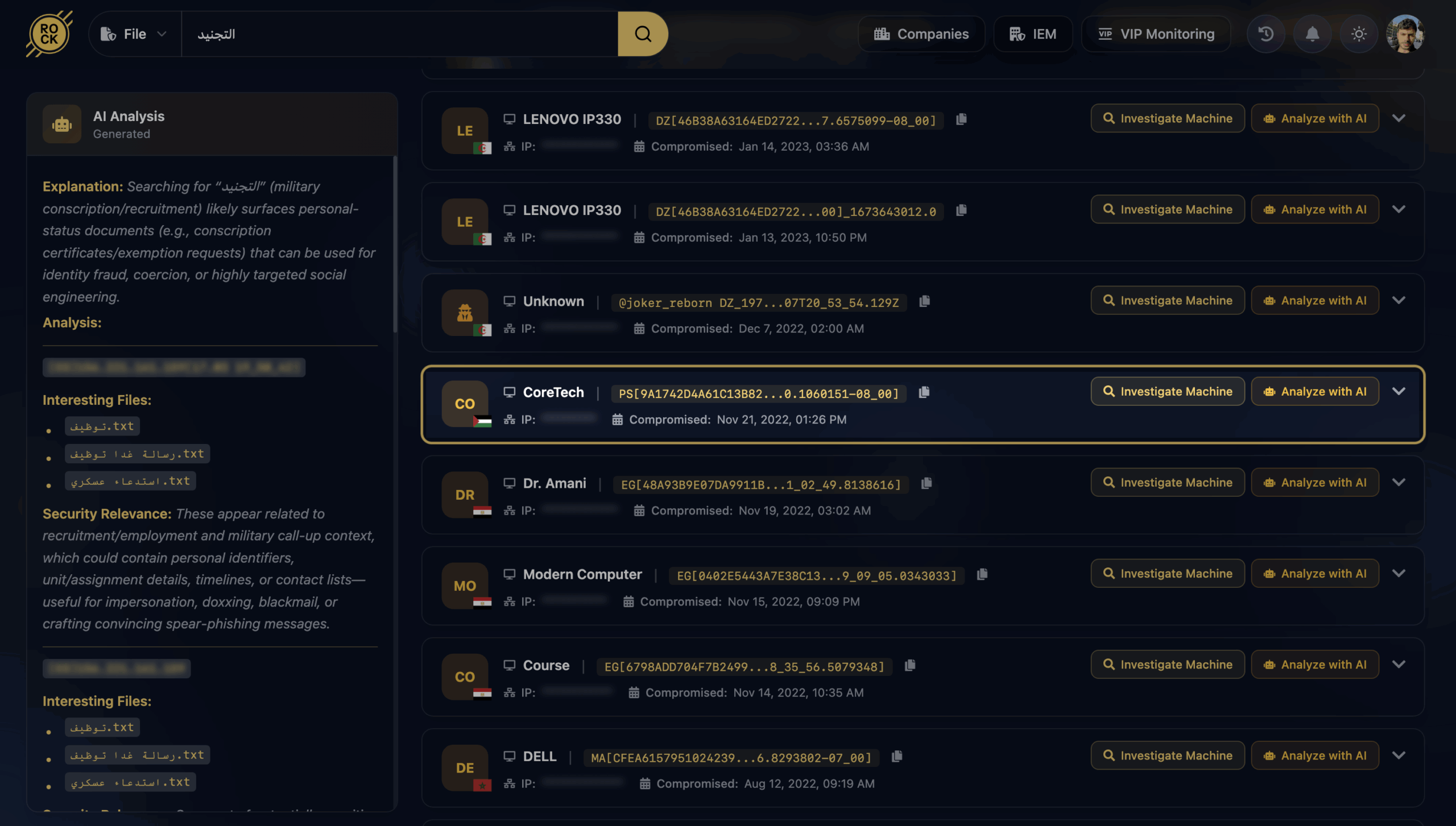
The investigation started with a simple filename search in Cavalier platform, using the Arabic term “التجنيد” (Recruitment). On its own, this is a totally normal word and is often used in HR or organizational documents.
But filename searches are powerful because they also reveal things that don’t quite belong. In this case, Hudson Rock researchers spotted a document that stood out from the rest of the files on the compromised machine. Instead of a routine administrative file, it turned out to be a detailed jihadist recruitment manual.
It’s a good example of how even innocent-looking keywords can lead to high-risk discoveries when you look at them in the right context – especially when analyzing data recovered from infostealer-infected systems.
AI Analysis Engine: Enki AI Investigator
Manually going through logs and foreign-language files doesn’t scale. To quickly understand what we were looking at, we used Enki – Hudson Rock’s AI Investigator – to analyze the contents of the compromised machine.
Enki doesn’t just translate files. It helps researchers navigate inside an infostealer-compromised machine, understand what each file is about, and see how it fits into the bigger picture. In this case, Enki broke down the document’s intent, highlighted key terminology, and flagged patterns tied to jihadist recruitment – turning a complex file into something immediately understandable.
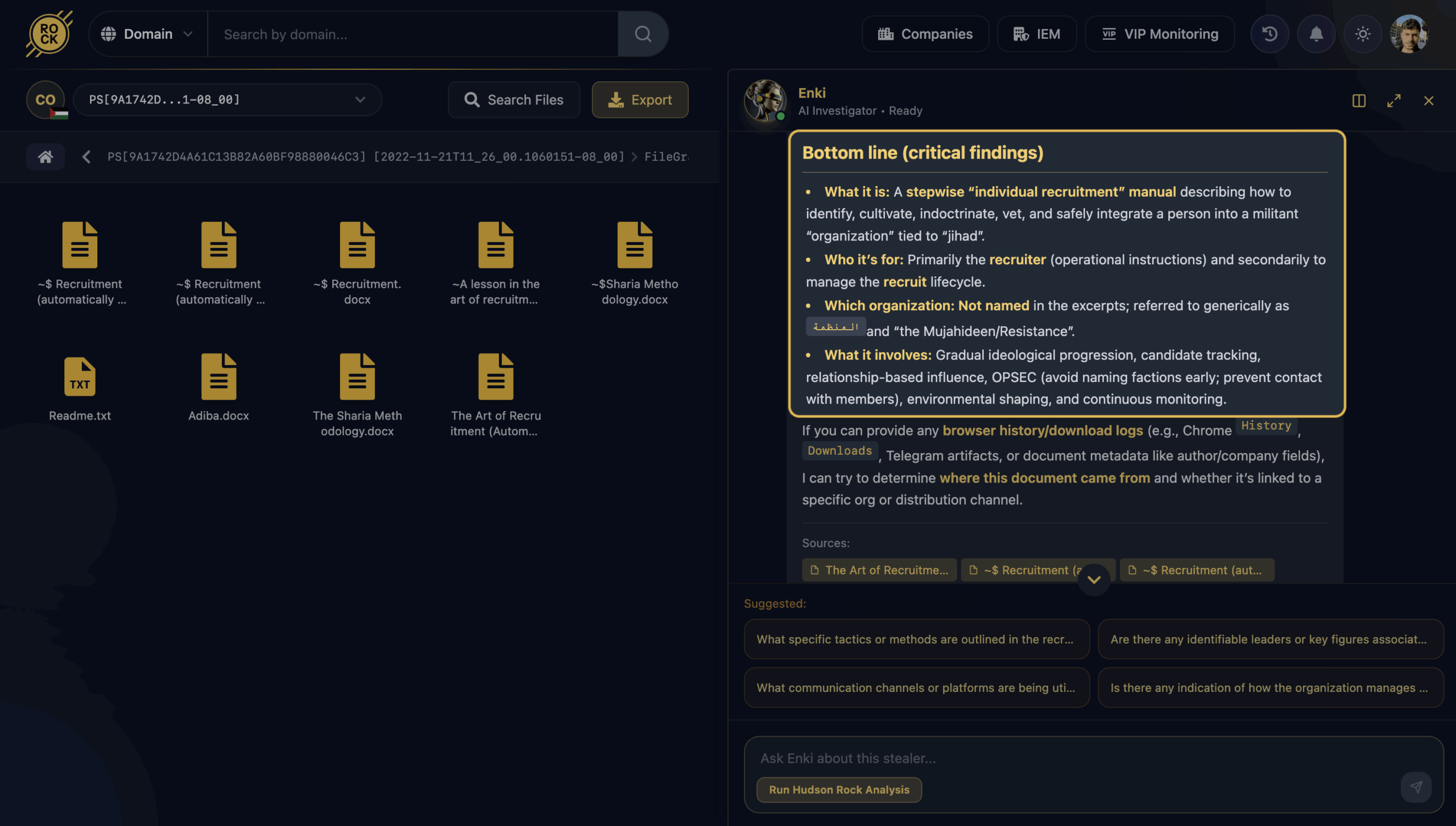
The Bottom Line: What Enki Found
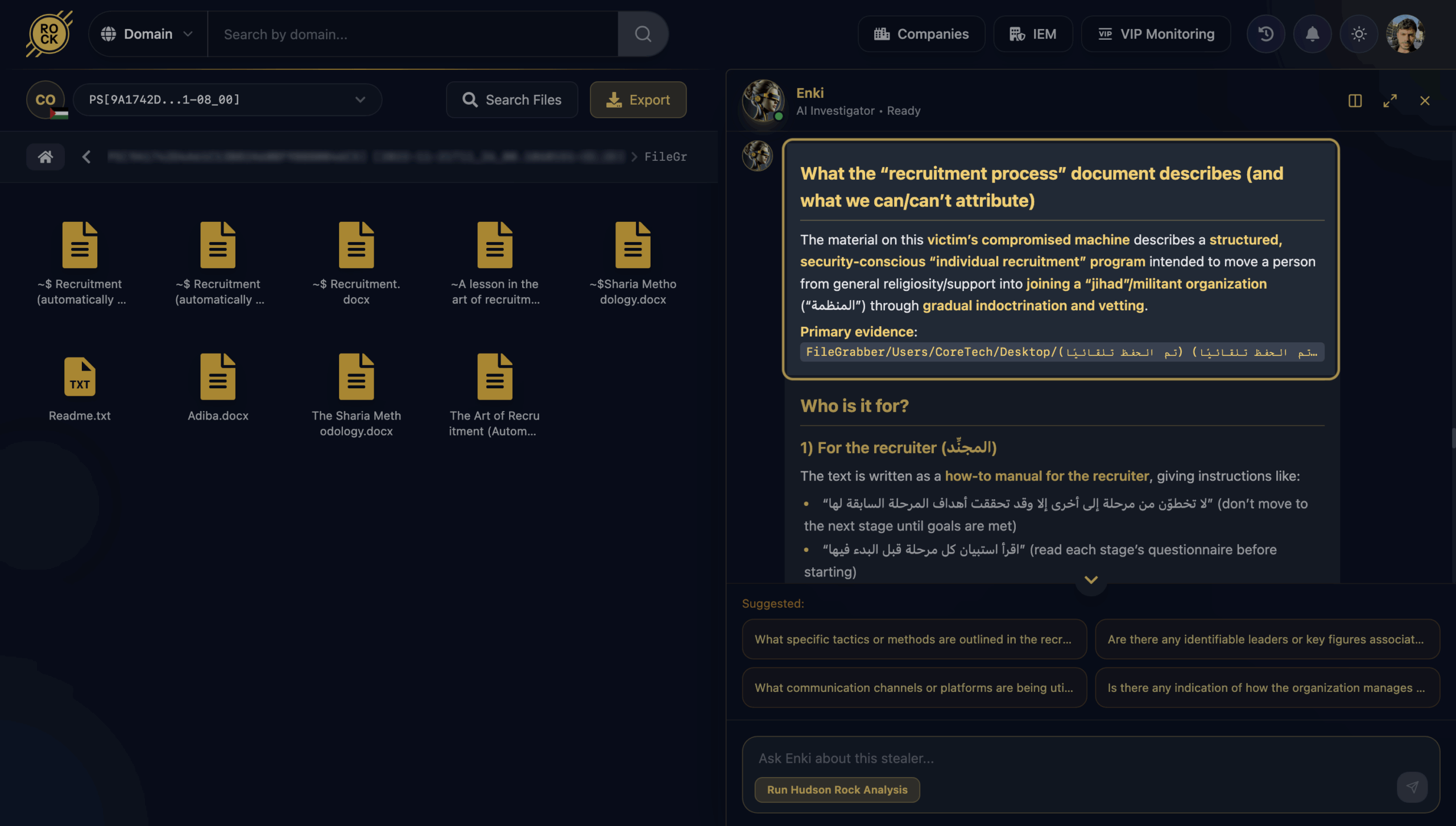
Once Enki finished analyzing the file, the picture became very clear. This wasn’t just ideological content – it was a practical, step-by-step recruitment manual focused on building people into jihadist cells.
What it is: A structured “individual recruitment” guide that walks a recruiter through every stage of the process – from identifying a potential candidate, to cultivating and indoctrinating them, vetting their reliability, and eventually integrating them into a militant organization tied to jihad.
Who it’s for: The document is written mainly for the recruiter, providing operational instructions, and secondarily as a way to manage the recruit lifecycle over time.
What it involves: The guide outlines a gradual ideological progression, candidate tracking, and relationship-based influence, with strong emphasis on OPSEC – avoiding early exposure to factions, limiting contact with members, shaping the recruit’s environment, and maintaining continuous control throughout the process.
Extracted Guide Content
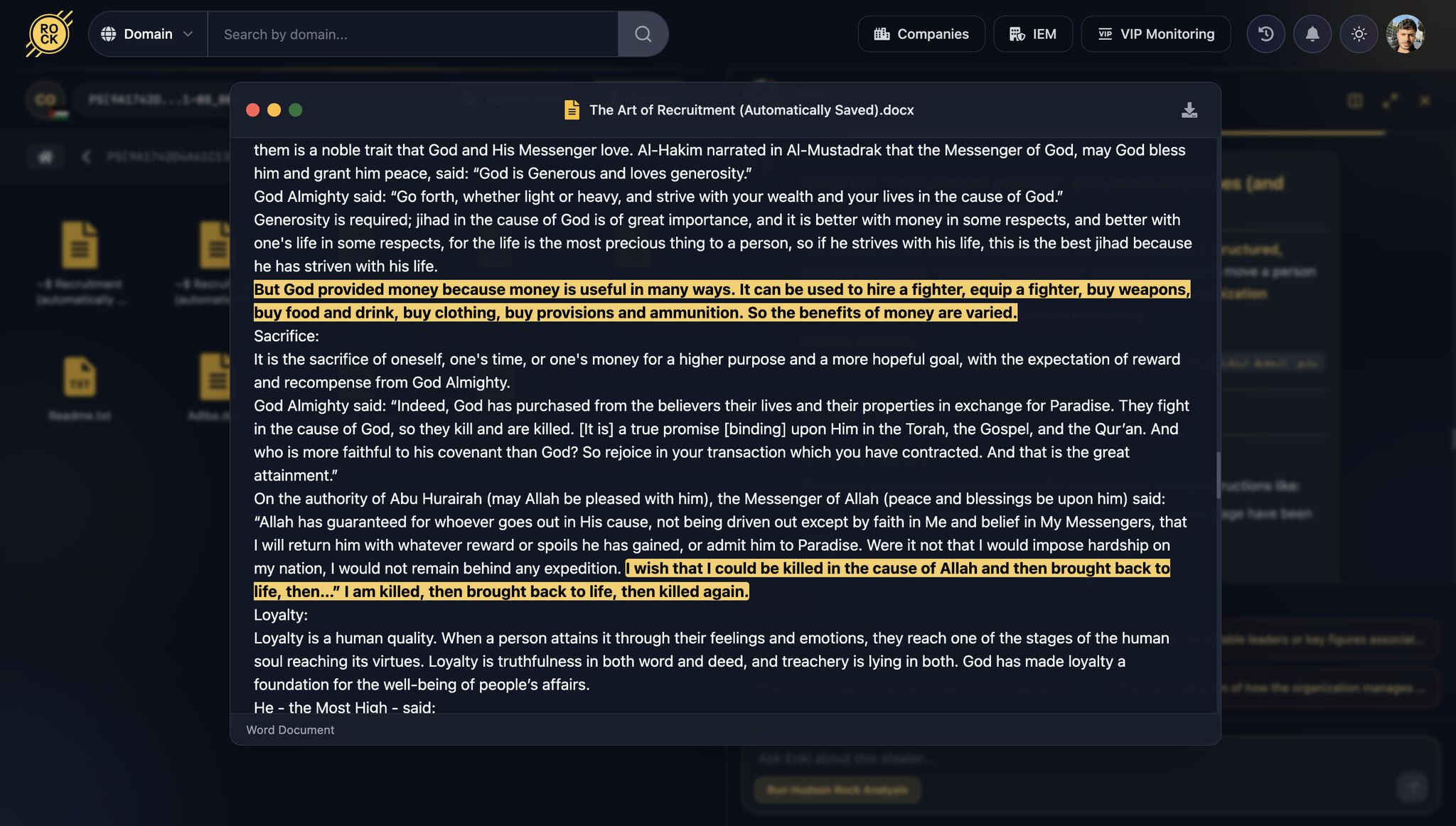
Beyond filenames and metadata, the content of the guide itself made its purpose unmistakable. Using Enki’s linguistic analysis, we extracted and reviewed key passages that show how recruitment, secrecy, and violence are framed inside the document.
These excerpts help bridge the gap between technical data recovery and human intelligence – showing not just that the file exists, but exactly how it’s meant to be used.
Operational secrecy and caution
Financing, logistics, and preparation for violence
Glorification of death and martyrdom
“I wish that I could be killed in the cause of Allah, then brought back to life, then killed again.”
Conclusion & Outlook
This investigation shows that the real value of infostealer intelligence isn’t just identifying exposed accounts – it’s the ability to move from identity exposure to operational understanding. With the combination of Cavalier’s search capabilities and Enki’s analysis, a single file on a compromised machine can turn into actionable intelligence.
For counter-terror and security researchers, infostealer-exfiltrated data provides rare visibility into real-world activity that would otherwise remain hidden. Platforms like Hudson Rock Cavalier make it possible to search, analyze, and understand this data at scale – connecting technical artifacts to human intent.
To learn more about how Hudson Rock supports investigations and intelligence work, visit hudsonrock.com.