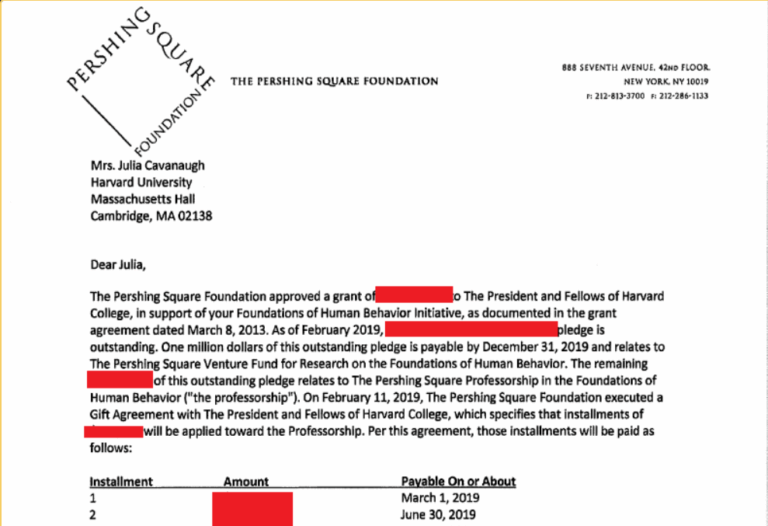
Over 17,000 employees and partners now face the fallout from a breach that started with a single infostealer infection on a Japanese computer in August 2025, ultimately handing attackers the keys to Nikkei’s Slack at nikkeidevs.slack.com.

Hudson Rock‘s deep dive into stolen credential logs reveals the mechanics behind this intrusion, the incident spotlights how Infostealers are turning collaborative tools into major data breaches, much like the credential thefts that fueled ransomware rampages against retail giants earlier this year.
Disclosed on November 4, 2025, Nikkei’s breach confession arrives at a critical moment for enterprise communication platforms, with infostealers harvesting over 270,000 Slack credentials worldwide in recent years alone.
What began as a routine malware compromise escalated into a full-blown data breach, pulling names, emails, and chat histories from the company’s developer channels.
For a media titan like Nikkei, publisher of Asia’s most-read business daily and steward of the Financial Times, this isn’t just a leak – it’s a potential blueprint for targeted phishing, insider threats, and competitive sabotage as we highlighted in a previous research – AI’s Role in Turning Massive Data Leaks into Hacker Paydays: A Look at the Orange Breach
The Nikkei Slack Intrusion: Malware’s Path from Personal PC to Data Leak
Hudson Rock‘s investigation traces the root cause to August 2025: a Japanese endpoint, likely an employee’s personal computer, was infected by an Infostealer. These malware types, often disguised as cracked software or phishing lures, quietly collect browser-stored tokens, browsing history, cookies, and credentials, before exfiltrating them to underground markets. In this case, the theft included valid Slack login details, allowing the attacker to access the workspace undetected and review its contents.


According to the official report, the exposed data included chat logs, user profiles, and metadata from 17,368 registered accounts, encompassing a large portion of Nikkei’s staff
“No leakage of information related to sources or reporting activities has been confirmed,” the company stated in its disclosure, a small mercy. Still, those developer channels likely contain details such as code snippets, secret keys, project timelines, vendor pitches, and strategic discussions that have proven be useful to attackers before.
Infostealers: The Credential Kleptomaniacs Powering 2025’s Shadow Economy
At their core, Infostealers are malware designed to collect credentials, session cookies, API keys, and OAuth tokens from infected endpoints. Strains like RedLine, Vidar, and Lumma are prevalent, with Hudson Rock’s log repository capturing millions of such thefts monthly. The Nikkei vector followed a common pattern: the malware likely arrived via a malicious download or email attachment, then extracted Slack’s browser-based authentication before sending it to a command-and-control server.
The statistics highlight the scale: Slack credentials number in the hundreds of thousands, often bundled with corporate email or VPN access for low prices. For organizations, mitigation involves multi-factor authentication enforcement, endpoint detection tuned for Infostealer indicators, and regular credential monitoring.


Investigations into the breach continue, with Hudson Rock monitoring related logs. This case serves as a reminder: in 2025, overlooked endpoint security can expose even the most secure communications.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock