Mandiant has exposed a sophisticated campaign using voice phishing to gain access to Salesforce accounts. Attackers impersonated IT support staff over the phone to trick victims into providing multi-factor authentication codes, allowing access to sensitive Salesforce environments. Once inside, the actors exfiltrated data and used it for extortion purposes.
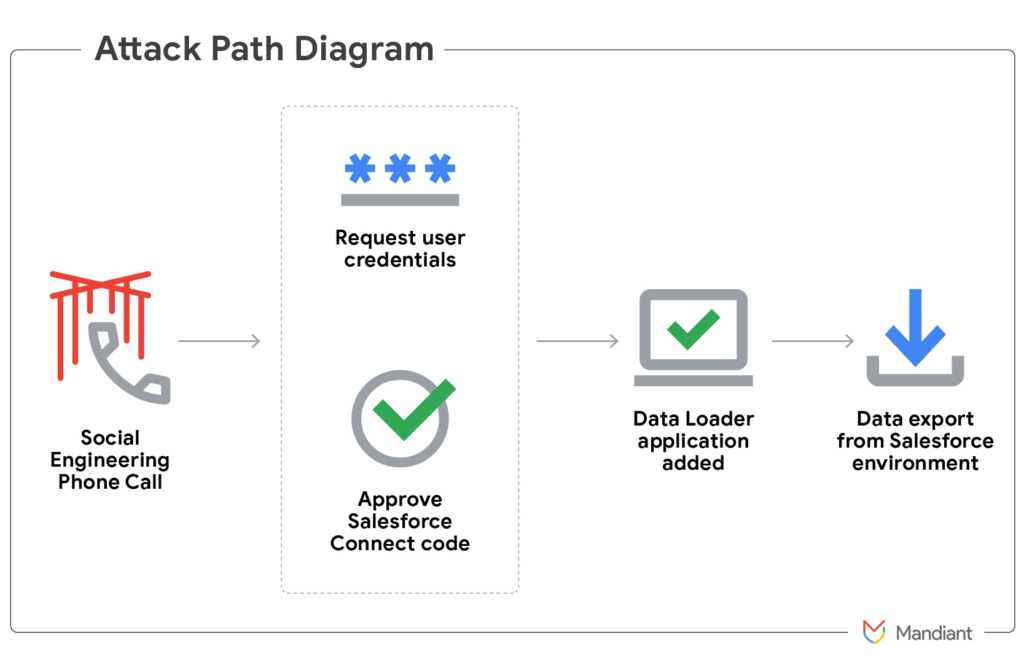
This operation highlights a growing trend among threat actors: targeting cloud CRM platforms like Salesforce as high-value entry points. While Mandiant’s focus was on real-time phishing, Hudson Rock’s research shows that Infostealer malware offers attackers a quieter but comparable alternative. Infostealers don’t need to trick victims in real time, they harvest credentials and session cookies from infected machines, often enabling access long after the initial infection.
Hudson Rock has identified thousands of companies with compromised corporate credentials to Salesforce in its cybercrime intelligence database. These credentials, harvested by Infostealer infections, include both usernames and active session cookies, providing immediate access to internal Salesforce instances in many cases.
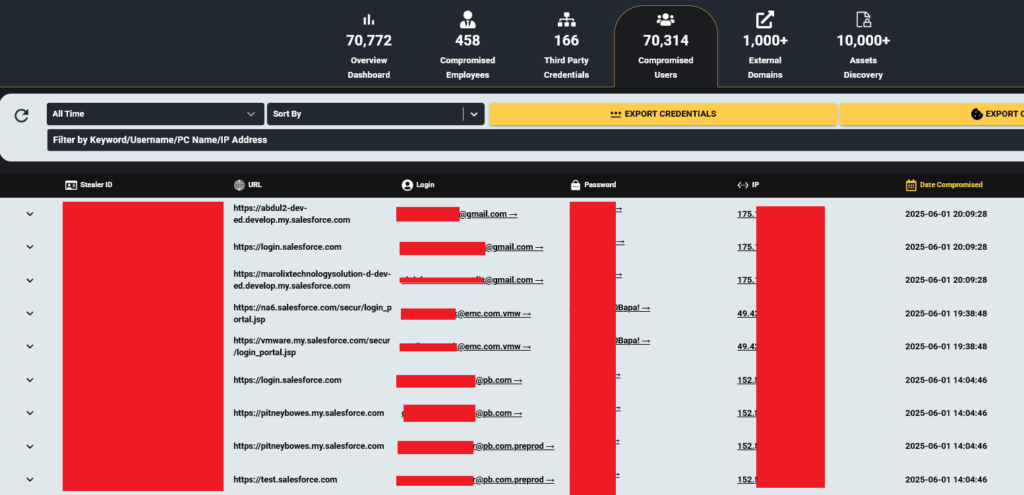
Coca-Cola breach suggests Infostealer logs may have played a role
On May 8, 2025, the Gehenna group claimed responsibility for breaching Coca-Cola Europacific Partners (CCEP), allegedly stealing 64 gigabytes of data including customer records, contact details, and internal Salesforce case files.

Screenshots shared by the threat actor appear to show full access to the Salesforce dashboard.
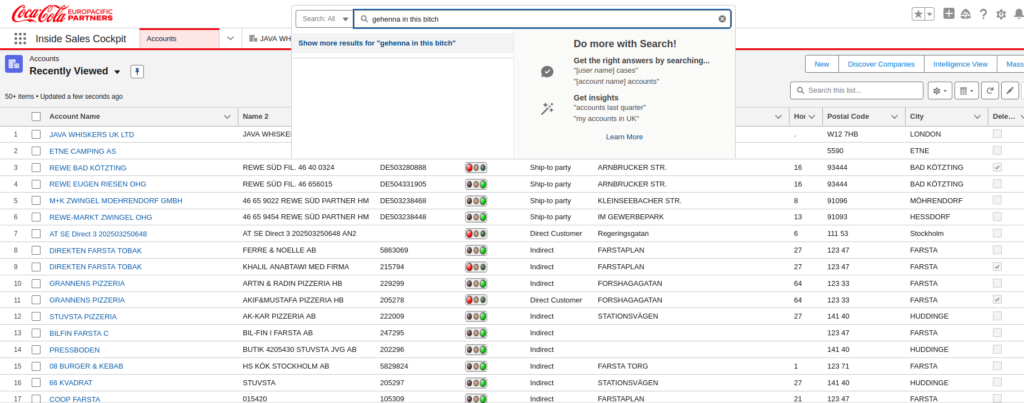
Hudson Rock identified an Azorult Infostealer infection dating back to August 30, 2020. The malware harvested credentials tied to ccep.my.salesforce.com. While Coca-Cola has not confirmed the method of compromise, the group behind the attack has a history of using credentials sourced from Infostealer logs in other breaches, including high-profile incidents involving Samsung and Royal Mail where JIRA credentials were used as the initial access.
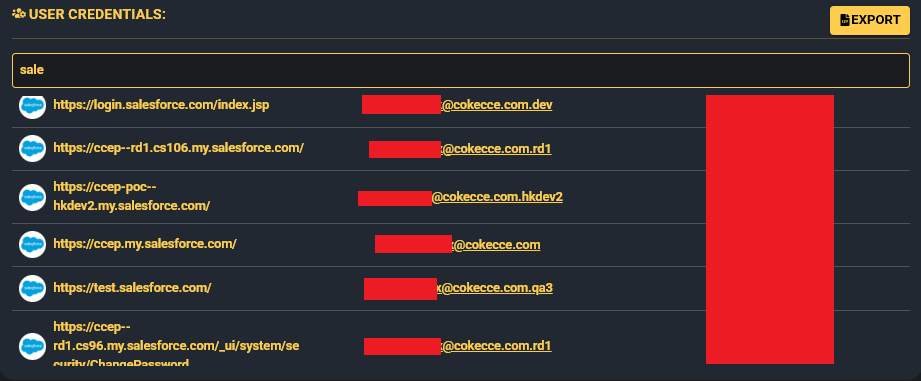
This pattern strengthens the likelihood that stolen credentials from the 2020 infection were used to facilitate the 2025 breach. The long dwell time, combined with Gehenna’s documented tactics, makes this scenario plausible and concerning.
Tiffany and Adidas incidents show a similar risk, though the connection remains speculative
On May 26, 2025, Tiffany & Co. disclosed a breach affecting customers in South Korea. The company cited unauthorized access to a “third-party platform used for customer data management”, likely Salesforce Commerce Cloud.
Hudson Rock’s analysis uncovered that an employee at OSF Digital, a known Salesforce partner working with Tiffany, had been infected with Lumma Infostealer in August 2024. The infection compromised a large amount of Tiffany Salesforce credentials and cookies. Browser history on the infected device revealed over 7,000 visits to Tiffany-related Salesforce URLs, suggesting deep involvement in the brand’s Salesforce infrastructure.
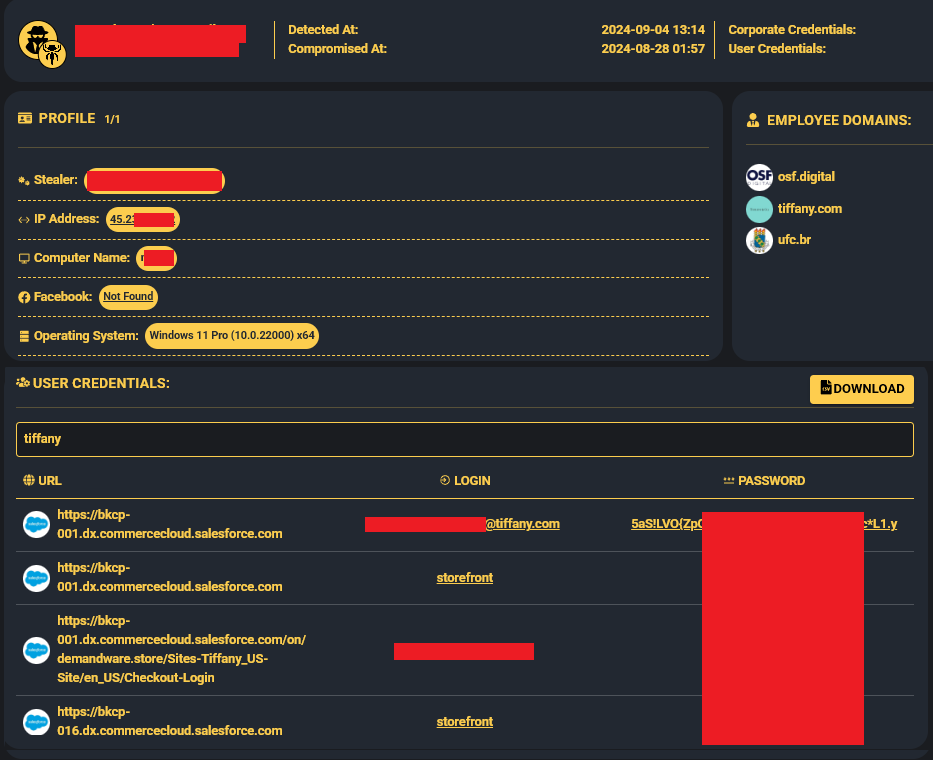
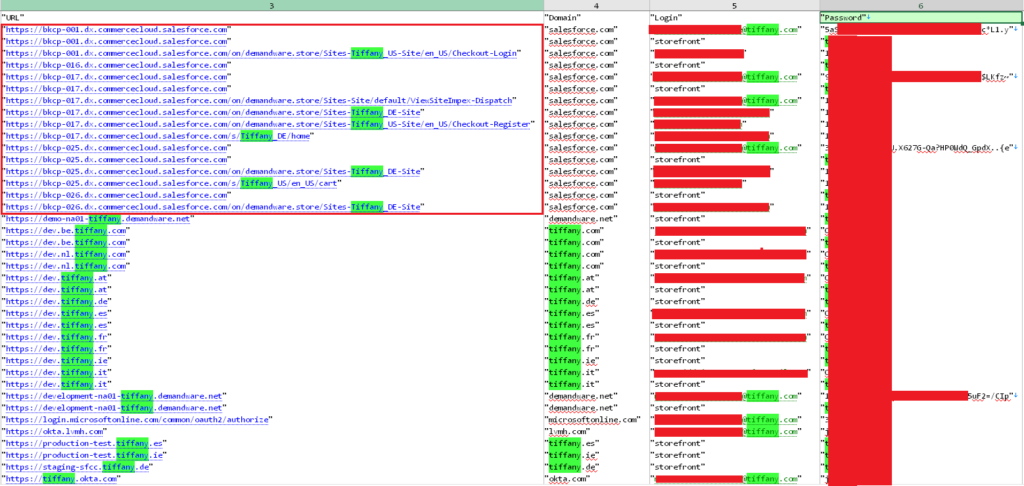
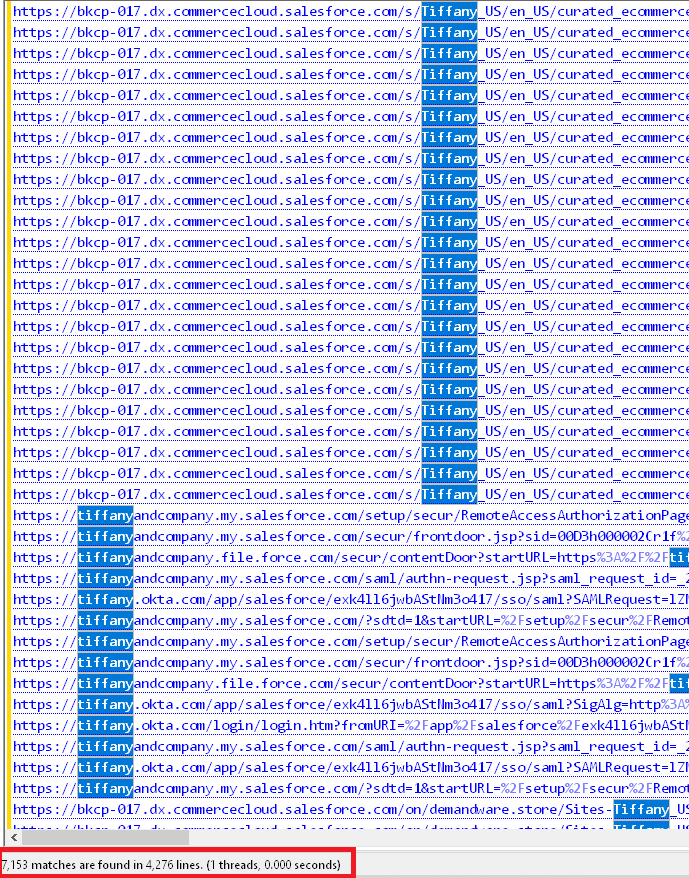
Although Tiffany has not confirmed whether stolen credentials were involved in the breach, the infection adds weight to the possibility that Infostealer data may have provided an access path. Still, there is no direct link tying the infection to the attack.
The Adidas breach, disclosed in May 2025, was attributed to a vendor compromise. While few details have been released, Hudson Rock identified 88 compromised corporate credentials associated with adidas.my.salesforce.com in Infostealer logs.
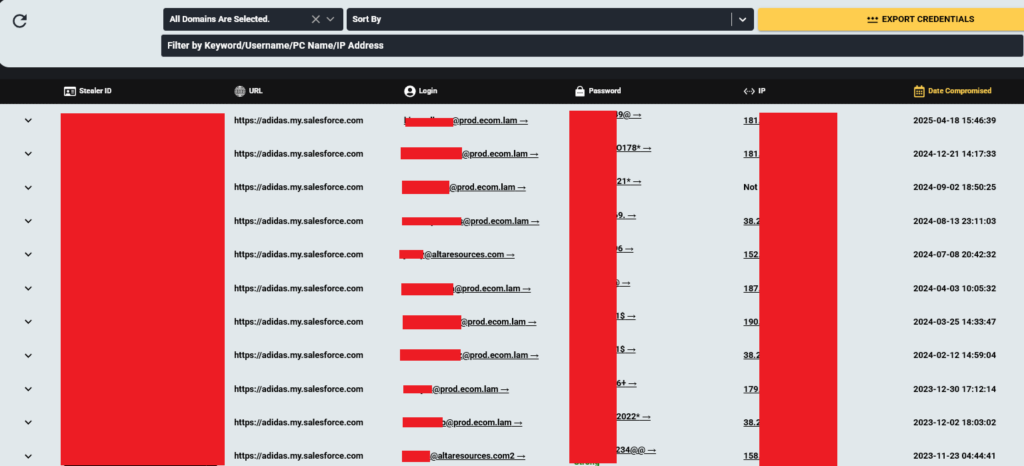
Adidas has not confirmed any Salesforce involvement, but the overlap raises questions about the potential for similar risk exposure.
Infostealers offer attackers a quieter, scalable route
The Mandiant campaign showed how attackers used social engineering to bypass multi-factor authentication and gain access to live Salesforce sessions. Infostealers like Azorult and Lumma follow a different path. These malware variants harvest login credentials, cookies, and session data from infected endpoints. This information is often resold on cybercrime marketplaces, allowing attackers to impersonate users and access internal systems long after the initial infection.
As CRMs such as Salesforce become more central to business operations, they are becoming increasingly attractive to threat actors. These platforms hold sensitive customer data, sales pipelines, and business logic. Attackers no longer need to rely solely on phishing or zero-days when Infostealer logs already contain a steady supply of valid CRM credentials. These credentials represent low-hanging fruit that often require little effort to weaponize.
The Coca-Cola case shows how a years-old infection can resurface with serious consequences. The Tiffany and Adidas cases demonstrate that even when the intrusion vector is not publicly confirmed, Infostealer infections in the vendor or employee ecosystem introduce significant risk.The Coca-Cola case demonstrates how long-forgotten infections can resurface as access points years later. The Tiffany and Adidas examples show how even if not confirmed as the source of compromise, Infostealer infections among vendors and employees create persistent risk.
Recommendations for protecting Salesforce environments
Organizations using Salesforce or similar cloud platforms should adopt a multi-layered defense strategy:
• Enforce phishing-resistant multi-factor authentication using physical security keys
• Monitor for leaked credentials and session data associated with corporate domains
• Deploy endpoint detection and response systems to detect and block Infostealer malware
• Rotate credentials regularly to reduce the lifespan of stolen data
• Train internal teams and vendors on social engineering and malware threats
• Audit third-party access and limit privileges to reduce exposure
Conclusion
The campaign described by Mandiant confirms that attackers are aggressively targeting Salesforce environments through social engineering. In parallel, Hudson Rock’s data shows that Infostealer malware continues to provide attackers with another viable route to the same result. In the Coca-Cola breach, the alignment between historical infections and the attacker’s known tactics points strongly to Infostealers as the likely source of access. In the Tiffany and Adidas cases, the infection data does not confirm involvement but serves as a reminder that attackers can reach Salesforce not only through vishing but also through stolen credentials circulating quietly online.
Organizations must treat both access paths, social engineering and malware infections, with equal seriousness. The cost of underestimating either route is now measured in millions of leaked records.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Follow us on LinkedIn for the latest breach research and cybercrime insights.