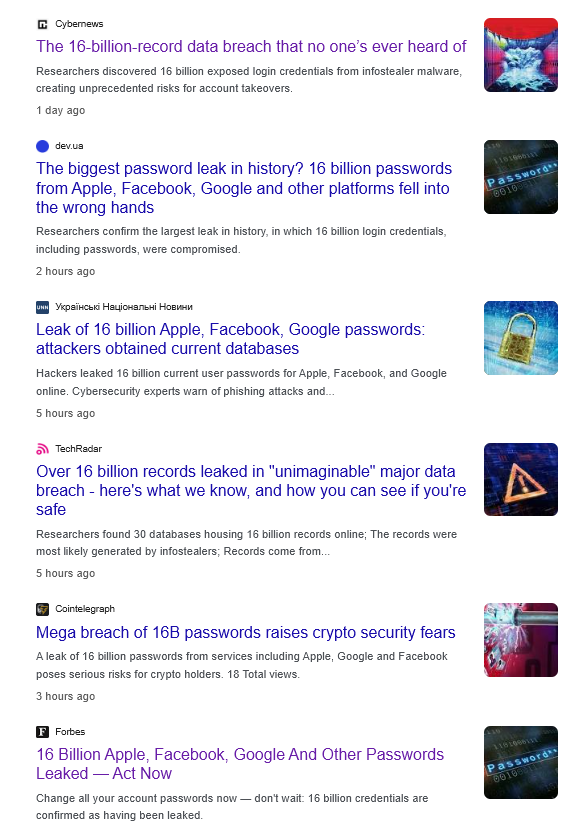
Recent reports of a 16 billion credentials leak have sparked widespread concern, with claims it’s one of the largest breaches ever. However, Hudson Rock’s analysis shows this “leak” is far less significant than suggested, consisting of recycled, outdated, and potentially fabricated data rather than a new breach. Here’s a clear breakdown of the incident and why infostealers remain a critical threat despite the exaggeration.
What’s Behind the 16 Billion Credentials Claim?
The leak was initially presented as a massive collection of stolen credentials, supposedly harvested by infostealer malware. But a closer look reveals a different story. According to BleepingComputer, the 16 billion credentials are a compilation of previously leaked data, including old infostealer logs and database breaches. The dataset also likely contains manipulated or fabricated entries, similar to the ALIEN TXTBASE leak, where credentials were altered (e.g., minor changes to usernames or passwords) for brute-forcing purposes.
The Numbers Don’t Add Up
Consider this: Hudson Rock’s data shows that the average number of credentials stolen per infostealer-infected computer is about 50. For a leak to reach 16 billion credentials, it would require 320 million compromised devices, a figure that’s unrealistic given global infection trends. This suggests the dataset is padded with redundant, outdated, or artificially generated data.
The inclusion of legacy infostealer credentials and old database leaks further reduces the leak’s impact. Many of these credentials are likely years old, already circulating on the dark web, and no longer valid. Fabricated data, a common tactic in large-scale leaks, also means parts of the dataset may be useless to attackers, created to inflate its perceived value.
Why This Leak Isn’t a Major Threat
Despite the alarming 16 billion figure, here’s why this leak is more noise than substance:
- Recycled Data: The dataset combines old infostealer logs and database breaches, much of which has been exposed before. Affected organizations and individuals have likely already addressed these exposures through password resets.
- Fabricated Credentials: Like the ALIEN TXTBASE leak, this dataset probably includes manipulated or fake credential pairs, often used for brute-forcing or to exaggerate the leak’s scale.
- No Evidence of Mass Infection: Hudson Rock’s monitoring of over 30 million infostealer-infected devices shows no recent surge in activity to support claims of 320 million compromised systems.
- Lack of Focus: Unlike targeted breaches, such as the Nobitex hack where infostealers exposed specific employee credentials, this leak is a disorganized data dump with little strategic value.
Infostealers: The Real and Ongoing Threat
While the 16 billion credentials leak is overhyped, it highlights the persistent danger of infostealers. These malware strains quietly steal credentials, session cookies, cryptocurrency wallets, and more, often undetected. In 2024, infostealers were linked to hundreds of millions of stolen credentials, driving ransomware, data breaches, and account takeovers.
Recent incidents underscore their impact. The Nobitex breach saw two employees’ credentials compromised by Redline infostealer, leading to an $81.7 million loss. Similarly, the Hot Topic breach exposed 350 million customers’ data after an employee’s infostealer infection provided access to sensitive cloud systems.
Steps to Protect Your Organization
The 16 billion credentials leak shouldn’t distract from the real threat of infostealers. Organizations can take these steps to stay secure:
- Monitor Compromised Credentials: Use threat intelligence tools like Hudson Rock’s Cavalier to detect infostealer infections among employees, partners, and users in real time, preventing breaches early.
- Implement Multi-Factor Authentication (MFA): MFA is a key defense against stolen credentials, as seen in the Snowflake attacks where its absence allowed attackers to exploit infostealer logs.
- Enhance Endpoint Security: Deploy endpoint detection and response (EDR) systems to identify and block infostealers, which often infiltrate via phishing or malicious downloads.
- Train Employees: Regular training on spotting phishing and avoiding risky downloads can reduce infostealer infections. Security awareness programs can cut cyber risks by up to 60%.
- Audit Access Points: Routinely review and rotate credentials for critical systems like VPNs, webmail, and Jira, which infostealers frequently target.
How Hudson Rock Helps Fight Infostealers
Hudson Rock leads in infostealer threat intelligence, tracking over 30 million infected devices and delivering actionable insights to organizations globally. Our platform enables businesses to identify compromised credentials, assess risks, and prevent intrusions before they escalate. To see how Hudson Rock can protect your organization from infostealer threats, schedule a demo: https://www.hudsonrock.com/schedule-demo.
Final Takeaway
The 16 billion credentials leak is less a groundbreaking breach and more a recycled, inflated dataset designed to generate fear. While it’s not the crisis it’s been made out to be, it serves as a reminder of the ongoing threat posed by infostealers. By prioritizing robust monitoring, strong security practices, and real-time threat intelligence, organizations can protect their assets and stay ahead of cybercriminals.
Stay updated with our Infostealers weekly report for the latest trends and data on info-stealing activities.
Learn more about us: https://en.wikipedia.org/wiki/Hudson_Rock