Systematic Failure of Data Sovereignty
A Technical and Ethical Post-Mortem of the 2026 Harvard University ShinyHunters Data Breach
On February 4, 2026, the cybersecurity landscape of higher education was fundamentally altered. A breach attributed to the cybercriminal syndicate ShinyHunters – operating as part of the “Scattered LAPSUS$ Hunters” collective – exposed approximately 115,000 sensitive records from Harvard University’s Alumni Affairs and Development (AAD) department.
This incident is not merely a leak of names; it is a collapse of institutional data sovereignty. It exposes the private lives, financial liquidity, and intimate institutional strategies governing the world’s most influential academic donor base. The following analysis decomposes the technical origins of the breach and the problematic nature of the exposed “human infrastructure.”
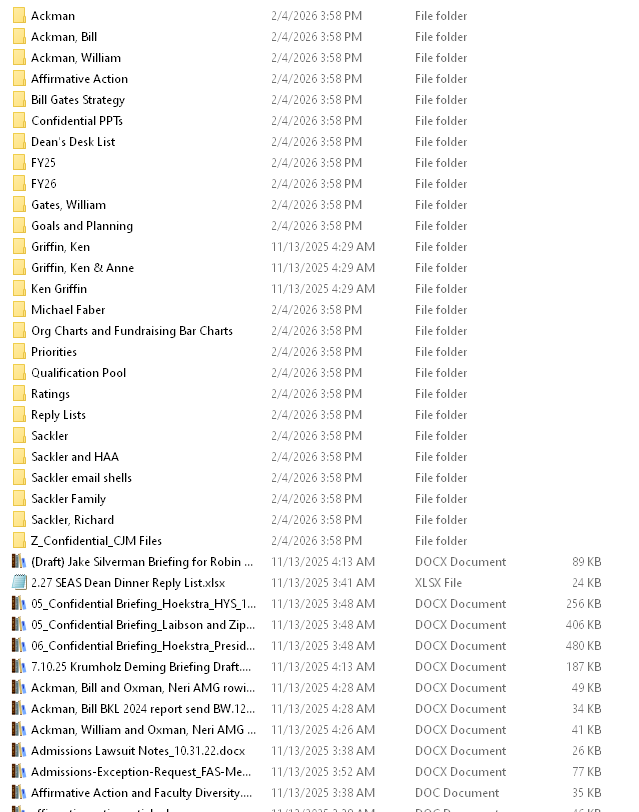
Figure 1: Overview of the file structure found in the leak, indicating a mass exfiltration of confidential stewardship data.
1. The Likely Attack Vector: Vishing and SSO Bypass
While the specific entry point for the Harvard breach has not been officially confirmed by university IT, security analysts point to the established modus operandi of the ShinyHunters collective in their recent campaigns. Unlike traditional network exploits that rely on unpatched servers, this group has exclusively weaponized the identity layer.
It is highly probable that the breach was executed through a sophisticated Voice-Phishing (Vishing) campaign targeting administrative staff, a tactic that has claimed dozens of corporate victims in the current wave of attacks.
Speculative Breakdown: The “Live Phishing Panel”
In this scenario, attackers – potentially using deepfake voice technology – impersonate IT support or identity vendors. Victims are directed to a typosquatted domain mimicking the institution’s Single Sign-On (SSO) portal. Using a Man-in-the-Middle (MitM) architecture, the attackers capture credentials in real-time and convince victims to approve MFA push notifications or read out OTPs. This allows the threat actors to hijack active session tokens, effectively bypassing the perimeter without tripping standard alarms.
Once inside, the group typically moves laterally across SaaS platforms like Microsoft 365, SharePoint, and Salesforce, programmatically searching for high-value terms like “confidential,” “stewardship,” and “proposal.”
2. The Data: A “Relationship Census” of 115,000
While headlines focus on billionaires, the 115,000 exfiltrated records represent a comprehensive census of the university’s human capital. The data structure reveals that the university tracks far more than just alumni.
The leak includes spouses, widows, parents, and specifically, current students. Entries such as 0000672498, Ms. Cristina [Redacted] appear with the status “Active, Other Individual,” indicating the tracking of people loosely connected to the university through executive education or specific programs. The data maps the “social graph” of these individuals, identifying family members, wealth bands, and domestic intimacy.
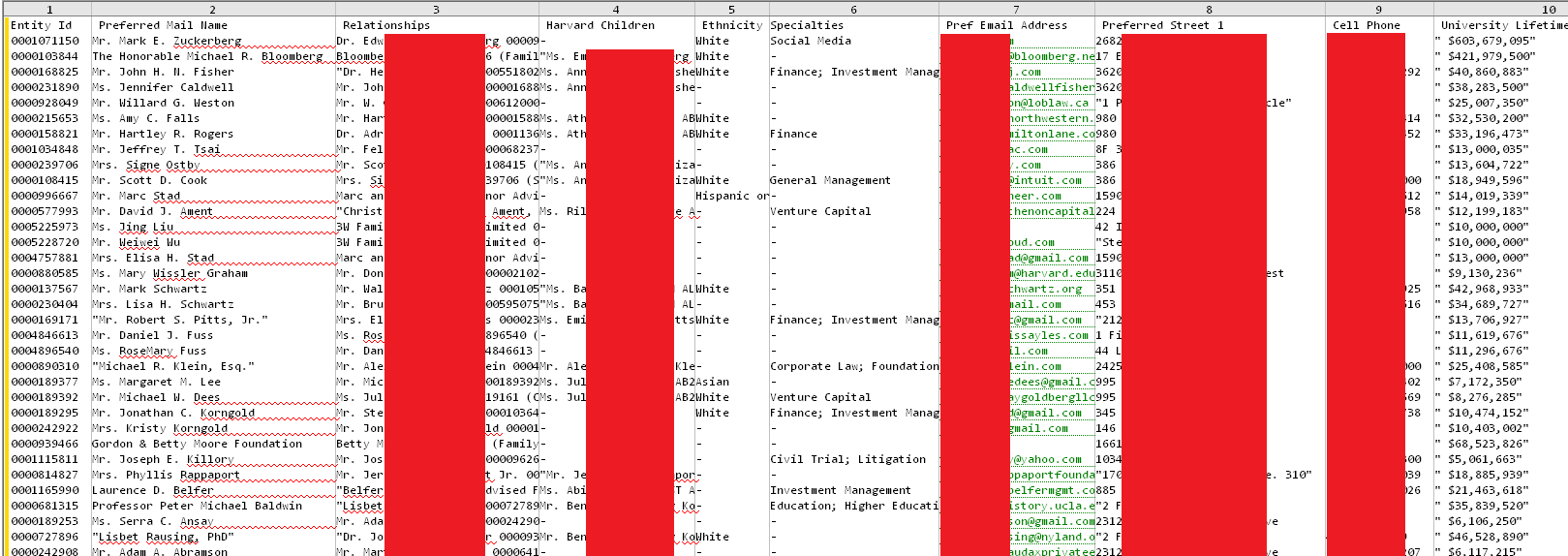
Figure 2: A snapshot of the “Top Donor” files, revealing how the university categorizes wealth and contact details.
3. Wealth Exposure: The “Top 115”
The breach creates a “high-value target” (HVT) environment by consolidating the financial and residential data of the global elite into a single SaaS-hosted repository. The leak explicitly reveals “Lifetime Recognition” amounts, providing a window into the exact financial relationship between specific figures and the university.
| Entity | Lifetime Recognition Amount | Rating Band | Exposed Sensitivity |
|---|---|---|---|
| Mark E. Zuckerberg | $603,679,095 | $5B+ | Home address, private email, spouse/sibling tracking. |
| Michael R. Bloomberg | $421,979,500 | $5B+ | Private Bloomberg LP emails, cell phone, NYC residential data. |
| Steven A. Ballmer | $102,409,226 | $5B+ | Specific campaign targets for SEAS. |
4. The Ethical Quagmire: “Admissions Holds”
Perhaps the most damaging aspect of the leak is the exposure of the synchronization between fundraising and admissions. Internal documents reveal the existence of “Admissions Pauses” or “Holds” – formal administrative triggers that halt solicitation while a family member is a prospective student.
The leak includes briefing notes on individuals like Sid Kosaraju and Lorence Kim. In Kosaraju’s case, a pause was active for his son [Redacted]’s senior year, even though the father explicitly stated the son would not be applying. This suggests a rigid, database-driven mechanism designed to protect the university from “pay-to-play” optics, yet its very existence in a fundraising database proves the departments are deeply coordinated.
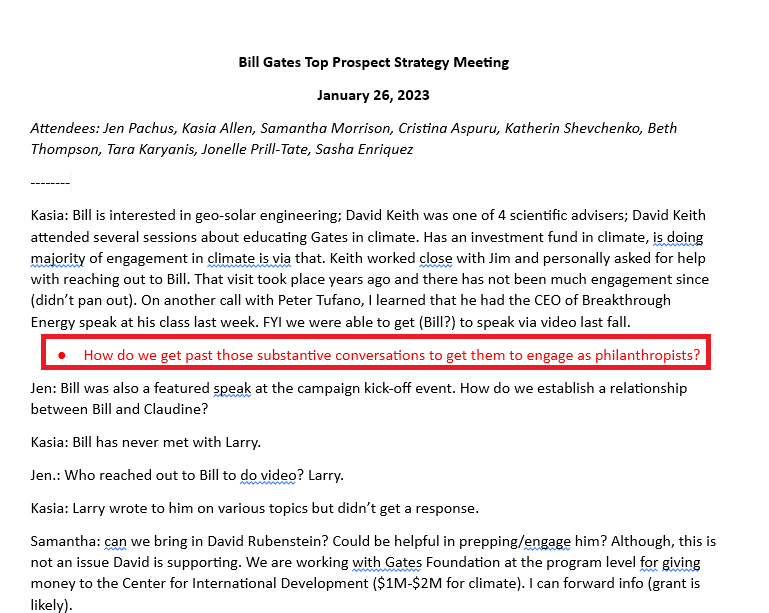
Figure 3: Strategy meeting notes regarding the cultivation of Bill Gates.
Furthermore, internal strategies regarding Bill Gates (Figure 3) reveal the university’s reliance on specific faculty members, like solar geo-engineering expert David Keith, to “cast [programs] from a programmatic angle” that appeals to Gates’ interests. It exposes the anxiety regarding faculty retention as a tool for donor retention.
5. Legal Intricacies: The Pershing Square Documents
The breach allows for a granular audit of legal agreements. Documents related to the Pershing Square Foundation, signed by Bill Ackman, detail specific payment schedules (e.g., $200,000 annual installments over 25 years) and clauses regarding “catastrophic events” that would allow the foundation to cease payments.

Figure 4: Signed agreements detailing long-term financial commitments from the Pershing Square Foundation.
Conclusion: The End of Obscurity
The ShinyHunters breach demonstrates that the most valuable data is no longer just credit card numbers, but the metadata of influence. By centralizing admissions statuses, wealth ratings, and private family hierarchies into cloud-based platforms protected by bypassable MFA, institutions have created a single point of failure.
This incident is a mandate for the immediate adoption of Phishing-Resistant MFA (FIDO2/Hardware Keys) and a “Zero Trust” architecture. As the data shows, a single phone call to an administrative assistant can now unravel the privacy of the world’s most powerful individuals.