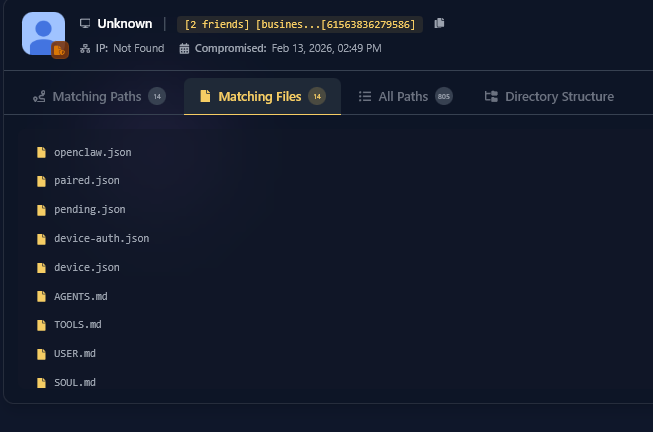
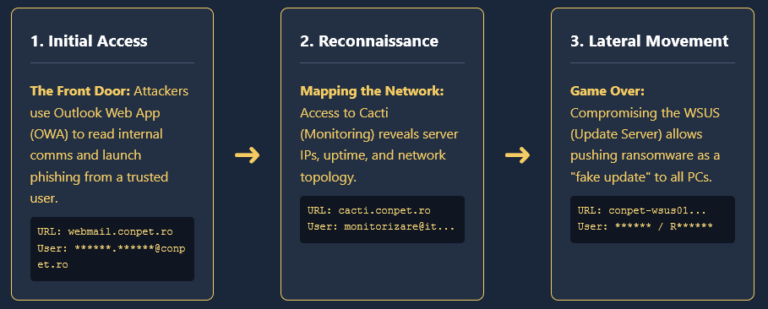
In a cyberattack that underscores the destructive power of infostealer malware, Hy-Vee, a prominent U.S. supermarket chain, has been hit by a massive data breach courtesy of the Stormous ransomware group. The attackers claim they’ve infiltrated Hy-Vee’s Atlassian accounts, specifically Confluence and Jira, using stolen credentials, Hudson Rock traced back these credentials to various Infostealer infections of Hy-Vee employees.
This breach, which allegedly exposes 53GB of sensitive internal data, aligns with Stormous’ own admission of leveraging infostealers in other attacks, such as their breach of a French government’s platform. Here’s how Infostealers fueled one of the boldest retail cyberattacks of 2025.
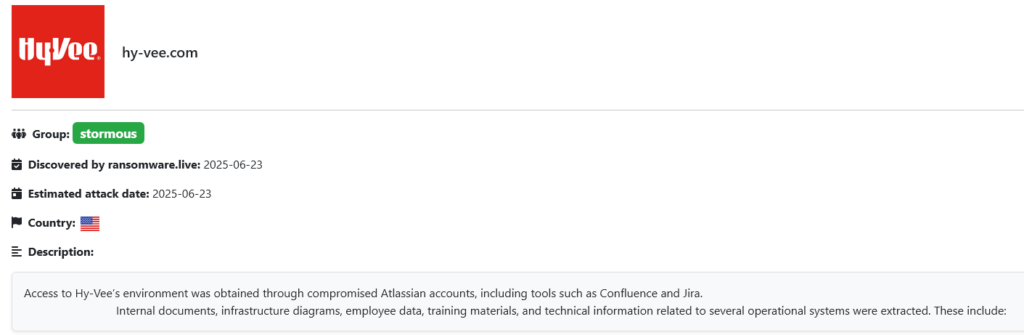
Stormous’ Atlassian Breach and Data Heist
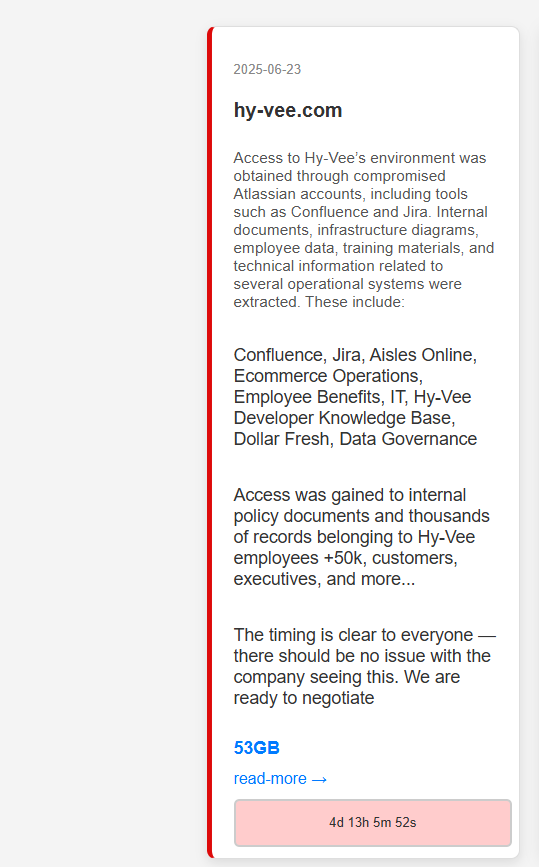
On June 23, 2025, Stormous claimed responsibility for breaching Hy-Vee’s Atlassian infrastructure, targeting Confluence and Jira, as reported by TechNadu. The group allegedly exfiltrated 53GB of critical data, including internal documents, infrastructure diagrams, training materials, and technical details about operational systems like Aisles Online, e-commerce operations, employee benefits, IT systems, and data governance.
The breach, which allegedly also exposed data related to over 50,000 individuals, was announced on Stormous’ dark web leak site with a four-day ransom deadline. A screenshot shared by HackManac on X confirmed the group’s claims, showing a dark web post detailing the stolen data.
Hudson Rock’s analysis revealed the root cause: over 50 Infostealer infections on Hy-Vee employee’s devices, which harvested credentials granting access to Atlassian accounts. These compromised credentials, stolen by malware like StealC, Lumma, and Redline, provided Stormous with a foothold to infiltrate Hy-Vee’s internal systems.
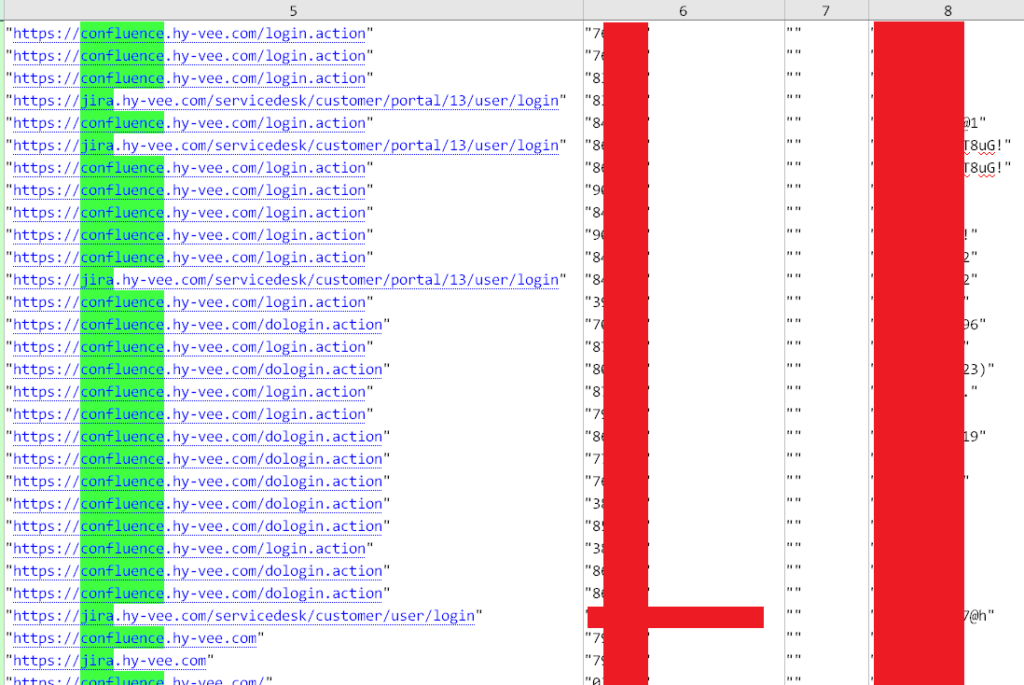
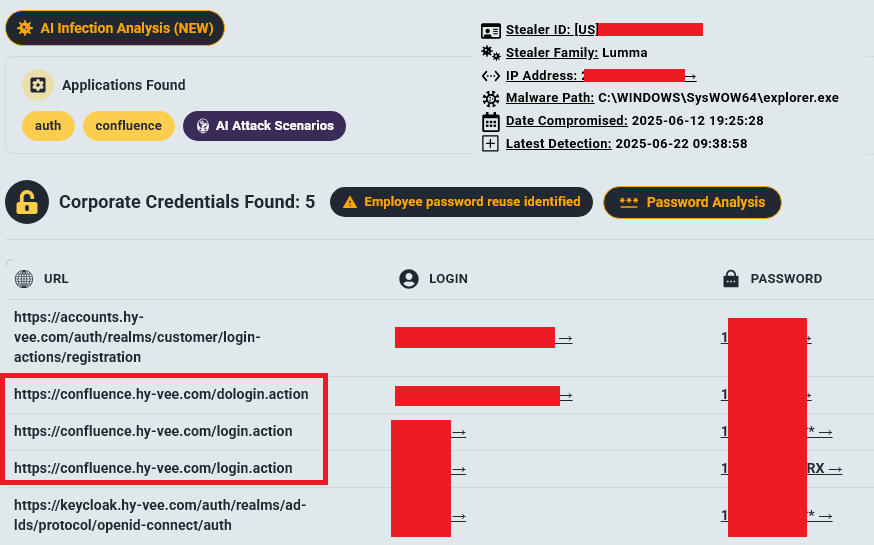
The breach’s impact is significant, as Confluence and Jira are critical collaboration tools containing sensitive corporate information, making them prime targets for cybercriminals seeking intellectual property and operational insights. Other hacking group such as HELLCAT Ransomware group previously hacked companies such as Schneider Electric, Jaguar Land Rover, Telefonica, and others, using Jira credentials from Infostealer credentials, leveraging the exact same technique.
A Retail Giant’s Nightmare
The fallout from Hy-Vee’s breach is severe. The stolen 53GB of data, will soon be circulating on the dark web, and pose risks of corporate espionage, phishing campaigns, and further cyberattacks.
Infrastructure diagrams and operational details could enable adversaries to map Hy-Vee’s IT environment, while employee and customer data may fuel identity theft or fraud. Hy-Vee has yet to officially confirm the breach, but the lack of response, as noted by TechNadu, leaves stakeholders in the dark. This incident follows a 2019 Hy-Vee breach involving point-of-sale systems, highlighting the chain’s recurring cybersecurity challenges.
Infostealers: The Key to Modern Ransomware
The Hy-Vee breach is a reminder of infostealers’ role as the linchpin of sophisticated cyberattacks. Hudson Rock’s database shows a surge in infostealer infections targeting retail and corporate environments, with Atlassian products being a prime target due to their widespread use. Stormous’ explicit reference to infostealers in other breaches and their success against Hy-Vee suggest a deliberate strategy of exploiting stolen credentials for high-impact breaches.
Organizations must prioritize Infostealer infection monitoring, endpoint security, multi-factor authentication (MFA), and regular credential audits to combat infostealers.
Hy-Vee’s breach is a wake-up call for retailers to secure their digital infrastructure against this evolving threat.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock