Executive Summary
A compromised machine in Lebanon – most likely belonging to a person named قسورة (Qasura), a local ISIS cell commander – contained explosive synthesis manuals, jihadist propaganda, and locally stored XMPP chat logs that should have been encrypted. The chats reveal Qasura receiving direct instructions from Syria-based operatives, coordinating IED attacks that killed security personnel, requesting religious permission for torture, managing cross-border smuggling routes, handling money transfers through Turkey and Syria, and shipping detonator components across the region. Through this single compromised machine, we were able to map the entire cell hierarchy from local commander to senior leadership.
Geographic Network – Operational Footprint
Locations extracted from conversation analysis
The Network Exposed
The compromised machine contained locally stored XMPP chat logs from “chatwith.im” and “conversations.im” accounts. While these encrypted messaging platforms are designed for secure communications, someone appears to have created a backup copy of these conversations and stored it on the compromised machine – giving us complete access to years of operational communications and the ability to map this terror cell’s complete organizational hierarchy.
ISIS Cell Network Structure
Reconstructed from Conversation Analysis











🔍 Why We Believe This Is Qasura’s Machine
Several indicators point to قسورة (Qasura) as the most likely owner of this compromised endpoint:
- Consistent receiver role: In every conversation, the “baqeya” accounts (baqeya33baq, baqeya3333baq, baqeya4444baq) are the ones receiving instructions, shipments, and guidance – not giving them
- Lebanon geolocation: The machine’s IP address (213.204.111.35) geolocates to Lebanon, matching Qasura’s described role as the “Wilayat Lebanon” cell commander
- Local backup perspective: The conversation logs are stored from the perspective of the baqeya accounts, with their messages appearing as the local/sender side
- Credit for local operations: Syria-based operatives explicitly credit him for IED attacks and component shipments originating from Lebanon
- Account ownership pattern: Multiple baqeya accounts on the same machine suggests one person managing several operational identities
Throughout these conversations, Qasura emerges as the Lebanon-based cell commander, receiving operational instructions from Syria-based handlers like abo.mohamd332, getting credit for IED attacks that killed security personnel, receiving shipments of detonator components, and consulting religious authorities on matters of torture and “war spoils.” The conversations position him at the center of the cell’s Lebanon operations – and his infected endpoint likely exposed the entire network.
The nature of these conversations, combined with the files found on the machine, strongly indicates ISIS (Islamic State) affiliation. The compromised machine contains folders named after senior ISIS figures, including “أرشيف الأمراء” (Archive of the Emirs) with content from known ISIS ideologues like Turki al-Bin’ali. The conversations use ISIS-specific terminology including “Bay’ah” (بيعة – pledge of allegiance), “Fay'” (فيء – war spoils), references to “Wilayat” (ولايات – provinces), and the “Amir al-Mu’minin” (أمير المؤمنين – Commander of the Faithful). References appear to the Ajnad Foundation – ISIS’s official media production arm. Even the account naming convention – “baqeya” (baqeya33baq, etc.) – directly references the ISIS slogan “باقية وتتمدد” (remaining and expanding).
Deep Dive Into The Conversations
The following sections present direct excerpts from the recovered XMPP chat logs, with translations. Each conversation block reveals a different aspect of the cell’s operations – ordered by criticality from killings and attacks to routine communications.
IED Attacks & Component Supply Chain
baqeya3333baq ↔ abo.mohamd332 • Oct-Dec 2021In this exchange, abo.mohamd332 (a Syria-based operative) explains the dual-detonation workflow to baqeya3333baq (the Lebanon cell), then announces “good news” – IED devices supplied by the Lebanon cell have already been deployed in multiple locations. He shares what appears to be photo/video evidence (via encrypted AESGCM link) of a vehicle attack, stating: “This car contains 2 officers and personnel… Thank God they’re all dead.” The Lebanon cell member responds with celebration, and abo.mohamd332 confirms: “God willing, you will have a share in killing them”-directly crediting the Lebanon cell for the deaths.
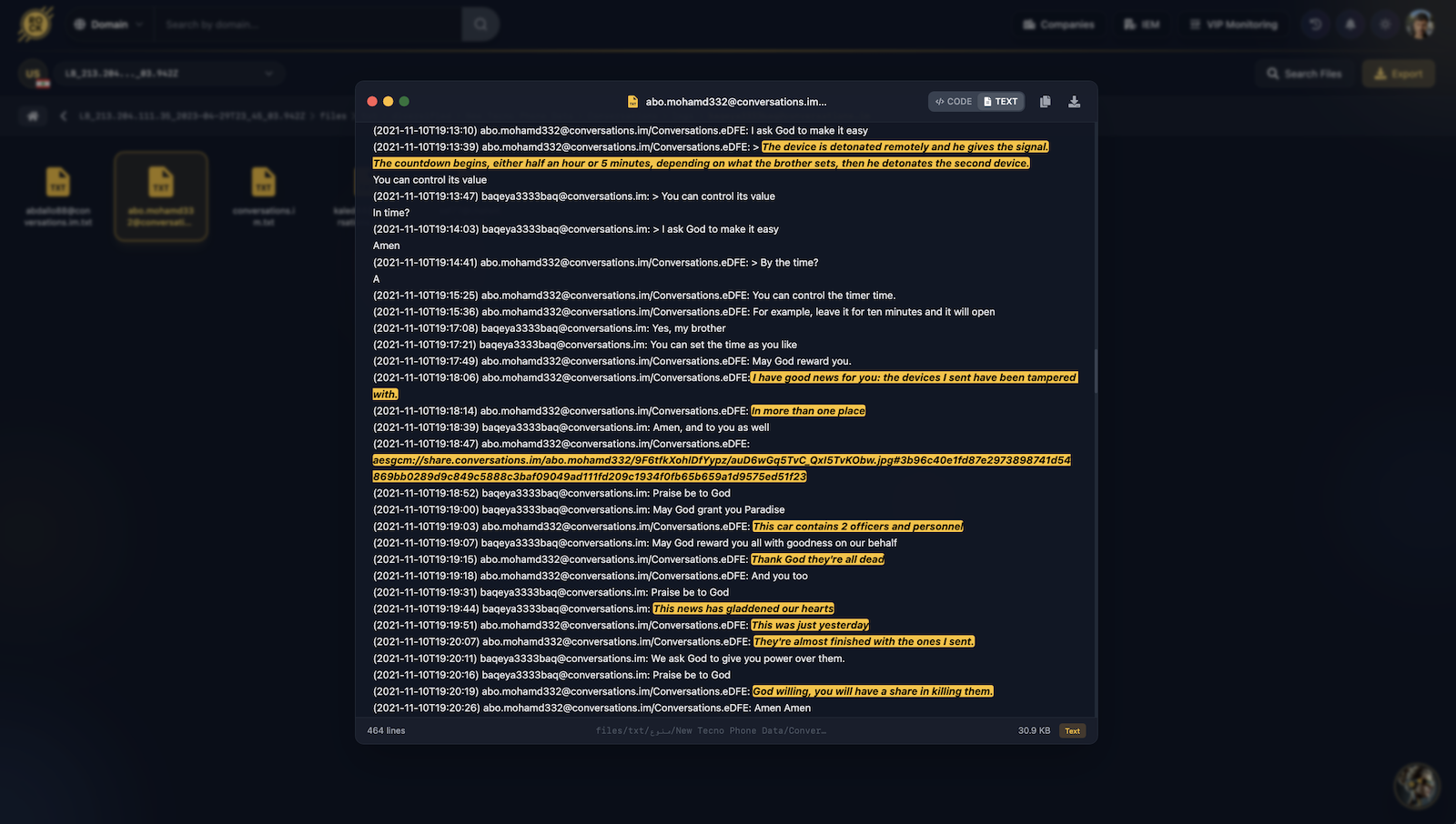
Part 1: IED Technical Discussion




Part 2: Attack Announcement & Evidence





Part 3: Celebration & Shared Credit





Part 3: IED Component Supply Chain
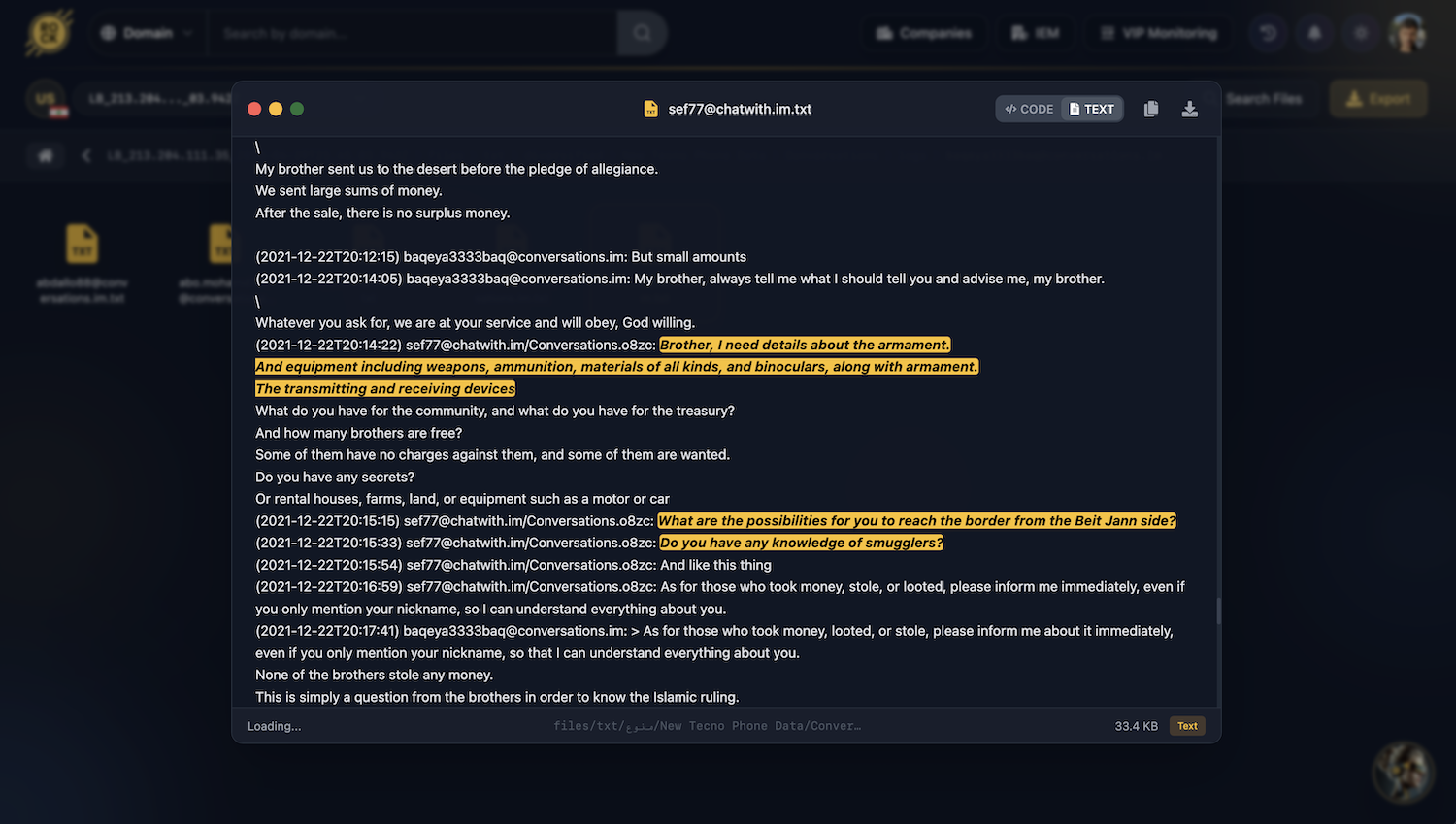
The same channel was used for coordinating large-scale IED component shipments from Lebanon to Syria/Iraq – documenting quantities of receivers (100+), timers (80+), and requests for thermal sniper scopes:




Attack Planning: Ambushes, IEDs, Poisoning
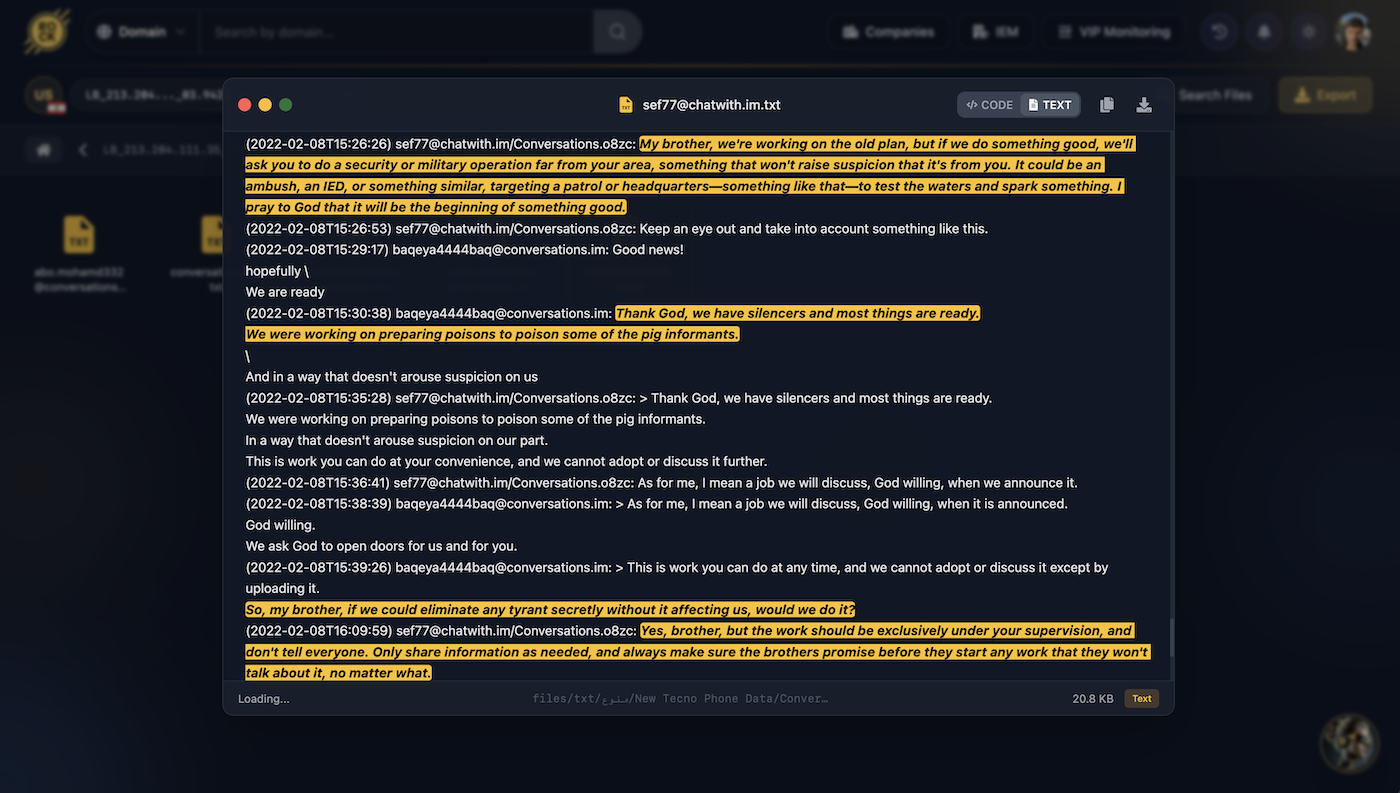
baqeya4444baq ↔ sef77 • February 8, 2022Senior commander (sef77) instructs Lebanon cell commander on planned operations including ambushes, IED attacks on patrols/headquarters, and poisoning informants. Cell confirms readiness with silencers and poison preparation.





Religious Rulings: Finance, Purity & Torture
baqeya33baq ↔ saker33/saker3333 • May-June 2021Lebanon cell member baqeya33baq consults extensively with sharia advisor saker33 (Abu Uthman) seeking religious rulings (fatwas) on various topics – from the permissibility of cryptocurrency trading, to ritual purity concerns (madhi/wadhi), to torture and mutilation of prisoners. The conversations reveal a structured process where even mundane personal matters require religious guidance from the group’s sharia authority.
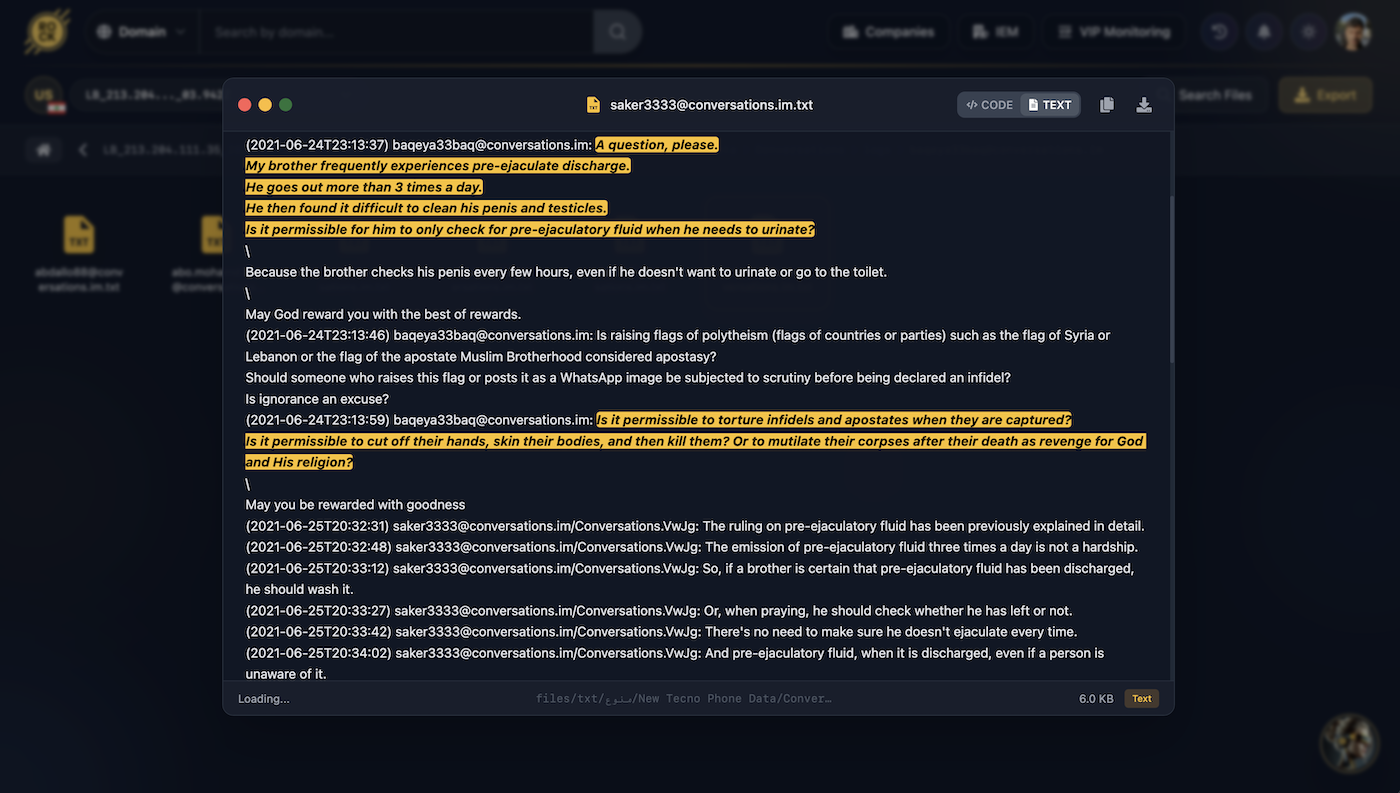
Torture & Mutilation Permission



Explosives Manufacturing Expertise
baqeya33baq/baqeya3333baq ↔ abdallo88 • May-July 2021Repeated requests to connect with an explosives/rocket manufacturing expert. Discussion of an expert in the “north” under security pressure (two raids). Request for manufacturing manuals.


War Spoils (Fay’): Robbery & Kidnapping
baqeya3333baq ↔ sef77 • Oct-Dec 2021Detailed discussion of “fay'” (war spoils)-money stolen from “tyrants.” Distribution formula: 25% cell, 25% local wilayah, 25% regional wilayah, 25% central treasury. Also discusses kidnapping for ransom infrastructure.



Hazardous Materials Discussion
nnn1111122222 ↔ asef55 • January 6-7, 2022Brief but significant discussion about an unidentified hazardous material. The Lebanon cell member assesses it as radioactive and requiring large facilities, possibly a poison with an incorrect name.


Money Transfers to Syria
baqeya3333baq ↔ kaled44 • June-July 2021Financial transfers from Lebanon to Syria (Deir ez-Zor area). Includes specific money transfer office name, location, and recipient name for hawala-style transfers.


Recruitment & Cell Management
Multiple conversations • 2021-2022Processing new recruits for bay’ah (pledge of allegiance to ISIS), CV/biography requirements, encryption protocols, endorsement (tazkiya) requirements, weapons inventory, smuggling routes, and hideout assessments.
Bay’ah (Pledge) Processing



Cell Management & Smuggling



Key Players & Communication Network
| Actor | Accounts | Role | Location |
|---|---|---|---|

Qasura
قسورة
Likely Machine Owner
|
baqeya33baq baqeya3333baq baqeya4444baq nnn1111122222 |
Lebanon Cell Leader (Likely Machine Owner) |
Lebanon |

Abu Muhammad
أبو محمد
|
abo.mohamd332 abo.mohamd334 mohamd434 |
Operations Coordinator Bay’ah Handler |
Syria/Iraq |

Sef
سيف
|
sef77@chatwith.im | Wilaya Commander Finance & Strategy |
Syria (Shaam) |

Abu Uthman
أبو عثمان
|
saker33 saker3333 saker333333 |
Sharia Judge Religious Authority |
Mobile |

Abdullah
عبد الله
|
abdallo88@conversations.im | Syria Field Coordinator | Syria |

Khaled
خالد
|
kaled44@conversations.im | Finance / البصيرة | Al-Busayra, Syria |
Identified Kunyas (Aliases)
- قسورة (Qasura) – Lebanon Cell Commander / Likely Machine Owner
- أبو محمد (Abu Muhammad) – Operations Coordinator / Bay’ah Handler
- أبو عثمان (Abu Uthman) – Sharia Judge / Religious Authority
- سيف (Sef) – Wilaya Commander / Finance Lead
- عبد الله (Abdullah) – Syria Field Coordinator
- خالد (Khaled) – Finance Operative / Al-Busayra
- العم (Al-‘Am / “The Uncle”) – Senior Commander
- أبو ماريا (Abu Maria) – Former Emir
Real Names from ID/Barcode Files
- مـوفق الباير محمد خير مريم المحمود (Mowafaq Al-Bayer) – DOB: 1-3-1979, Syrian National ID: 12020007918
- حمزه الخميس العويد محمد هناء العرنوس (Hamza Al-Khamis Al-Owaid) – DOB: 15-4-2005, Syrian National ID: 14030087260
- كنان عبد السلام ياسين لينا عمر (Kenan Abdel Salam Yassin) – DOB: 2-5-1987, Damascus, Syrian National ID: 03120035634
- نور ساطي (Nour Sati) – DOB: 05/07/2019, Location: Kamid al-Lawz, Western Bekaa
- فاطمة محمد موسى (Fatima Muhammad Musa) – Location: Azaz, Syria
Additional Findings
Dark Web & Hacking Tools
The machine contained offensive security and anonymity tools:
- Kali Linux 2021.3 installer
- Katana tool with TorSearchEngines.txt (list of Tor search engines)
- SQLMap (SQL injection tool)
- ProtonVPN
Supporting Evidence: Chemistry & Explosives Files
Beyond the conversations, the machine contained files that raised immediate red flags:
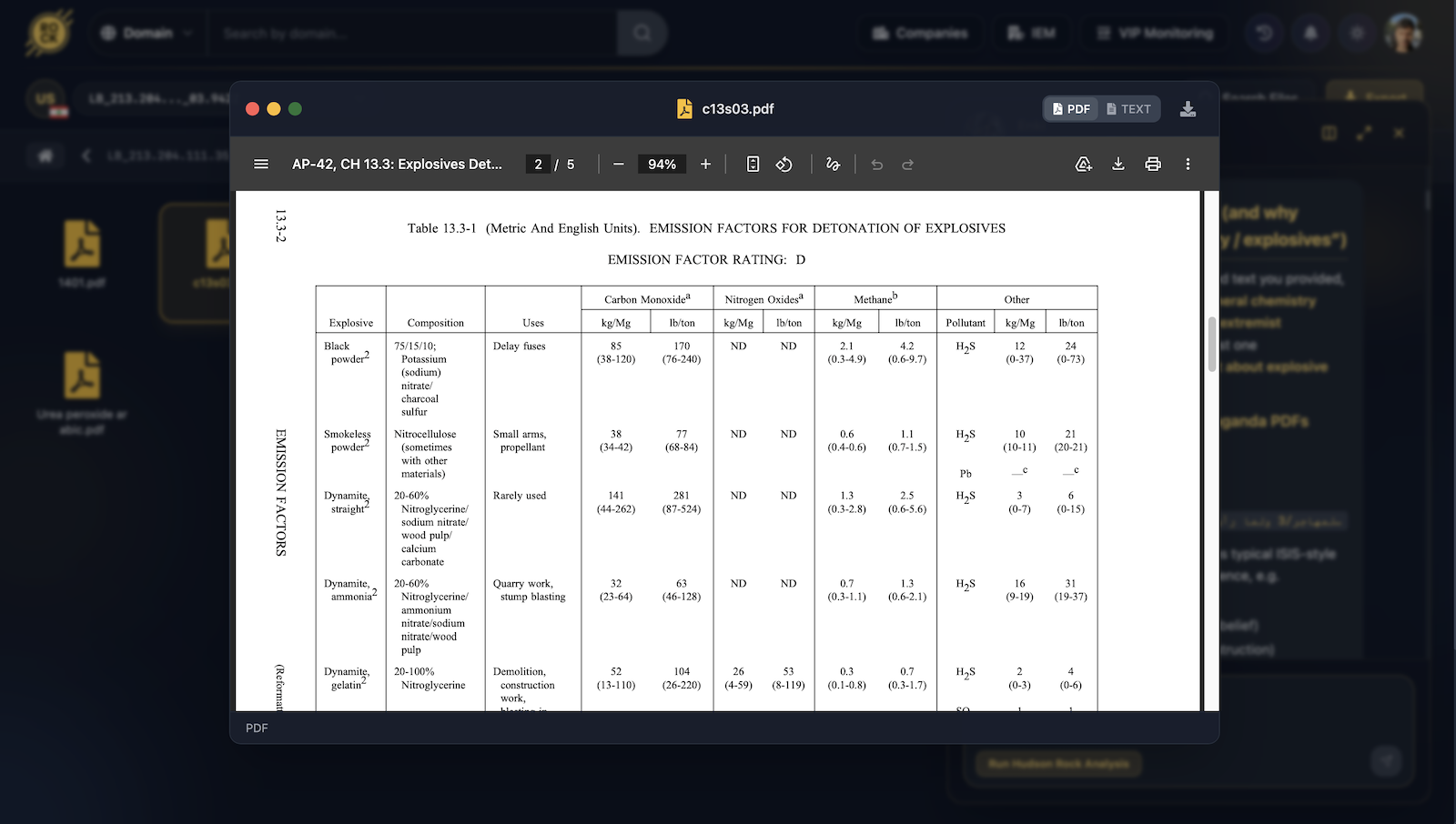
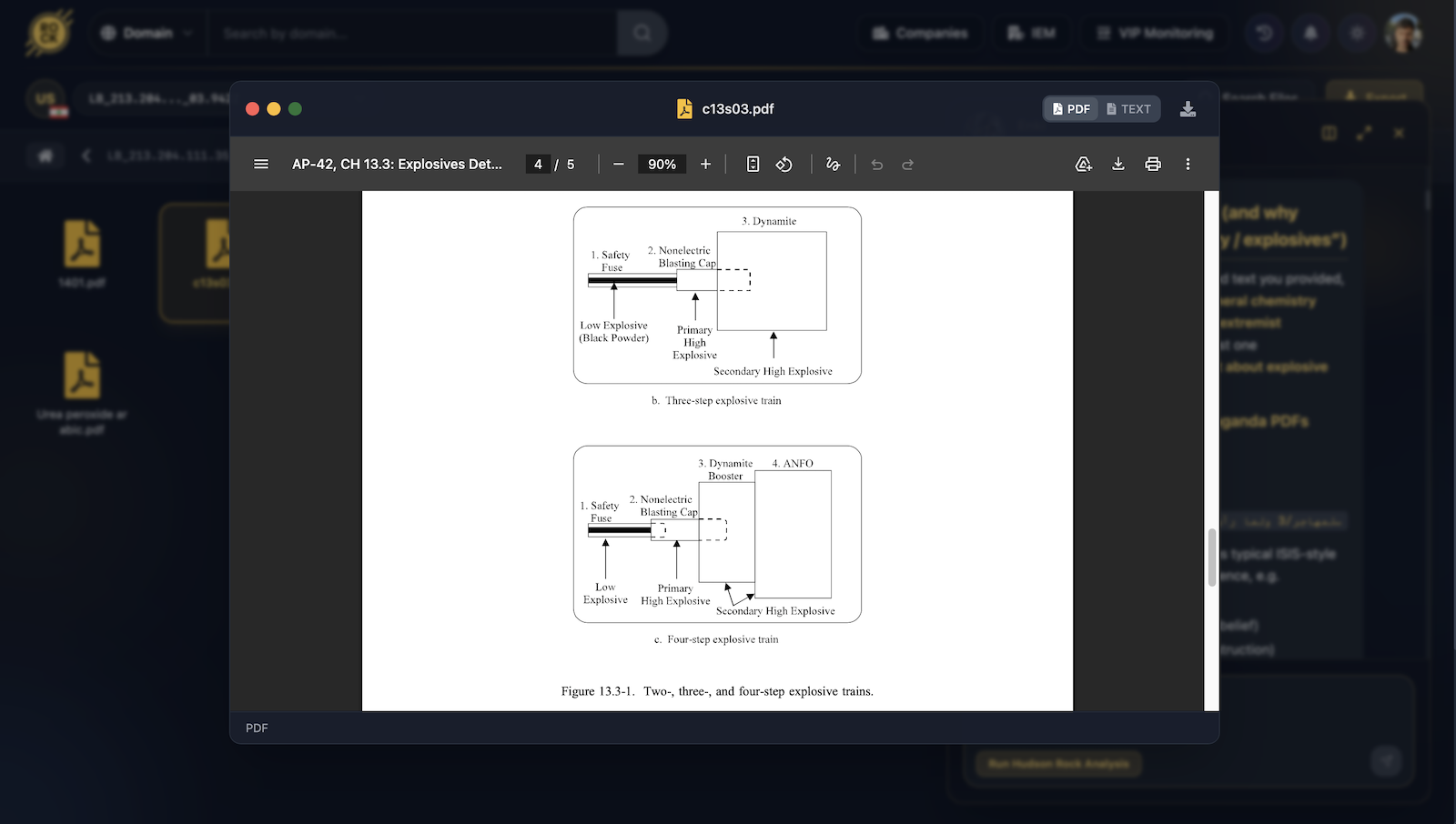
Urea Peroxide Synthesis Manual (Arabic)
A complete synthesis manual for urea peroxide, a primary explosive:
(In the name of God, the Most Gracious, the Most Merciful)
“Urea peroxide or carbamide peroxide is a white crystalline material produced by mixing urea with hydrogen peroxide at concentrations above 30%.”
“It can be used as an explosive with a detonation velocity between 3,000 and 4,000 meters per second.”
“For detonation, it requires a compound detonator with an activating charge to explode.”
Example: 30g H₂O₂ (50%) + 20g urea
The document ends with religious framing typical of jihadist technical manuals.
Conclusion: The InfoStealer Blindspot
Through a single InfoStealer infection on a machine in Lebanon, we recovered the complete operational communications of an active ISIS cell – conversations that reveal not just plans, but confirmed attacks with casualties.
1. Confirmed IED Attacks
Direct evidence of successful IED attacks, including photo/video evidence shared between operatives and celebration of killed officers: “Thank God they’re all dead.”
2. Cross-Border Supply Chain
A documented pipeline of IED components – 100+ receivers, 80+ timers – flowing from the Lebanon cell to operatives in Syria, with the Lebanon cell directly credited for attack casualties.
3. Sharia-Sanctioned Violence
Religious rulings explicitly authorizing torture, including permissions for burning, dismemberment, and the treatment of captured enemies as “fay'” (war spoils).
4. Complete Cell Hierarchy
Full organizational mapping from Qasura (the likely machine owner) through wilaya leadership (Sef77) to senior command (“The Uncle”), with bay’ah pledge processing and recruitment protocols – all exposed through a single infected endpoint.
The Power of InfoStealer Intelligence
The cell used every recommended operational security measure: encrypted XMPP messaging via conversations.im and chatwith.im, OMEMO encryption, and separate accounts for different functions. But a single InfoStealer infection – most likely on Qasura’s machine – uncovered the entire cell operational infrastructure.
This investigation demonstrates the critical value of InfoStealer intelligence for counter-terrorism. One compromised endpoint revealed an entire terror cell: confirmed attacks with casualties, cross-border supply chains, religious rulings sanctioning violence, and complete organizational hierarchies from local commanders to senior leadership.
The same malware infrastructure that exfiltrates corporate credentials can – and does – capture terrorist communications. For intelligence agencies and counter-terror units, InfoStealer data feeds represent a massively underutilized resource that no amount of encrypted messaging can protect against.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
Hudson Rock also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools